This is an automatic message: you are obliged to read this letter to accept
the order.
Please, use the link seen down below to contact the USPS support team.
http://www.stbishoy.org/wp-content/b4d47c6405.html
Thanks and best regards.
Takeisha Wernecke - USPS Senior Station Manager.
Email analysis :
NOTE : wo56816421@occhristian.pvt.k12.ia.us
NOTE : USPS Priority
NOTE : Received : from occhristian.pvt.k12.ia.us (unknown [186.151.239.161])
NOTE : User-Agent : Opera Mail/10.62 (Win32)
NOTE : 186.151.239.161
Phishing analysis :
CLICK : http://www.stbishoy.org/wp-content/b4d47c6405.html
OPEN : http://www.stbishoy.org/wp-content/b4d47c6405.html
REDIRECT : http://servisedelivery.com/bot14/lgen.php
RESULT : Phishing is unresponsive...
Stbishoy.org analysis :
Registrant Email: stbishoy.org@proxy.dreamhost.com
Updated Date: 2016-11-01T18:00:21
Creation Date: 2009-08-02T04:33:23
Registry Expiry Date: 2017-08-02T04:33:23
Servisedelivery.com analysis :
Updated Date: 2017-04-24T17:04:10
Creation Date: 2017-04-24T00:00:00
Registrar Registration Expiration Date: 2018-04-24T00:00:00
Registrar Abuse Contact Email: abuse@bizcn.com
Registrant Name: Wuxi Yilian LLC
Registrant Organization: Wuxi Yilian LLC
Registrant Street: No.1001 Anling Road
Registrant City: Xiamen
Registrant State/Province: Fujian
Registrant Postal Code: 361008
Registrant Country: cn
Registrant Phone: +86.5922577888
Registrant Fax: +86.5922179606
Registrant Email: whoisprivacyprotect@whoisservices.cn
Thursday, April 27, 2017
Monday, April 24, 2017
Vous avez de nouveau message ( Phishing Société Générale )
Cher(e) Client(e),
Votre conseiller vous informe que vous avez reçu un message important
conçernant votrecPass ,
eAccèsuàxvosxcomptes
Cordialement
Société Générale
sg
Email analysis :
NOTE : X-Php-Originating-Script : 0:njd.php
NOTE : e@atosucire.com
NOTE : Received : by batidocs.fr (Postfix, from userid 33)
NOTE : Received : from batidocs.fr ([46.101.97.198])
Phishing analysis :
CLICK : eAccèsuàxvosxcomptes
OPEN : http://ecodebredpasrapel.com/votrecode
REDIRECT : http://www.drivegeelong.com.au/journal/url/njd
RESULT : Phishing attempt...
Affected services :
NOTE : e@atosucire.com (Spoofed email.)
NOTE : batidocs.fr (46.101.97.198) (Relaying the phishing email.)
NOTE : ecodebredpasrapel.com (Hosting the redirect to the phishing.)
NOTE : drivegeelong.com.au (Hosting the phishing.)
NOTE : Société Générale (Victim.)
Votre conseiller vous informe que vous avez reçu un message important
conçernant votrecPass ,
eAccèsuàxvosxcomptes
Cordialement
Société Générale
sg
Email analysis :
NOTE : X-Php-Originating-Script : 0:njd.php
NOTE : e@atosucire.com
NOTE : Received : by batidocs.fr (Postfix, from userid 33)
NOTE : Received : from batidocs.fr ([46.101.97.198])
Phishing analysis :
CLICK : eAccèsuàxvosxcomptes
OPEN : http://ecodebredpasrapel.com/votrecode
REDIRECT : http://www.drivegeelong.com.au/journal/url/njd
RESULT : Phishing attempt...
Affected services :
NOTE : e@atosucire.com (Spoofed email.)
NOTE : batidocs.fr (46.101.97.198) (Relaying the phishing email.)
NOTE : ecodebredpasrapel.com (Hosting the redirect to the phishing.)
NOTE : drivegeelong.com.au (Hosting the phishing.)
NOTE : Société Générale (Victim.)
Banco Santander (Brasil) S.A. | Evite Bloqueio de sua conta (*) (Phishing Attempt)
Banco Santander S.A.
Prezado(a) Cliente,
Comunicamos que seus dados cadastrais encontram-se desatualizados em nosso sistema.Para que você possa desfrutar dos benefícios com comodidade e segurança, pedimos que você efetue a Atualização Cadastral de Segurança imposta pelo nosso sistema.
Este procedimento deve ser efetuado, evitando o bloqueio aos canais Santander tais como Telefone, Internet Banking e Caixas Eletrônicos.
Para evitar a suspensão automática desses serviços, habilite suas atualizações clicando no botão abaixo.
Este recurso só é ativado se você aceitar, e é atualizado a partir de servidores certificados..
Deseja confirmar suas definições de segurança?
Confirmar
Banco Santander (Brasil) S.A. CNPJ: 90.400.888/0001-42 Avenida Presidente Juscelino Kubitschek, 2041 e 2235 - Bloco A, Vila Olímpia, São Paulo/SP - CEP 04543-011
Screenshot of the phishing :
Email analysis :
NOTE : Received : by ip-160-153-226-153.ip.secureserver.net
NOTE : (Postfix, from userid 33)
NOTE : 160.153.226.184
NOTE : X-Mailer : Microsoft Office Outlook, Build 17.551210
NOTE : X-Mailer : iGMail [www.ig.com.br]
Phishing analysis :
CLICK : Confirmar
OPEN : http://ip-160-153-229-233.ip.secureserver.net/cadastro/*
RESULT : Phishing is unresponsive...
Prezado(a) Cliente,
Comunicamos que seus dados cadastrais encontram-se desatualizados em nosso sistema.Para que você possa desfrutar dos benefícios com comodidade e segurança, pedimos que você efetue a Atualização Cadastral de Segurança imposta pelo nosso sistema.
Este procedimento deve ser efetuado, evitando o bloqueio aos canais Santander tais como Telefone, Internet Banking e Caixas Eletrônicos.
Para evitar a suspensão automática desses serviços, habilite suas atualizações clicando no botão abaixo.
Este recurso só é ativado se você aceitar, e é atualizado a partir de servidores certificados..
Deseja confirmar suas definições de segurança?
Confirmar
Banco Santander (Brasil) S.A. CNPJ: 90.400.888/0001-42 Avenida Presidente Juscelino Kubitschek, 2041 e 2235 - Bloco A, Vila Olímpia, São Paulo/SP - CEP 04543-011
Screenshot of the phishing :
Email analysis :
NOTE : Received : by ip-160-153-226-153.ip.secureserver.net
NOTE : (Postfix, from userid 33)
NOTE : 160.153.226.184
NOTE : X-Mailer : Microsoft Office Outlook, Build 17.551210
NOTE : X-Mailer : iGMail [www.ig.com.br]
Phishing analysis :
CLICK : Confirmar
OPEN : http://ip-160-153-229-233.ip.secureserver.net/cadastro/*
RESULT : Phishing is unresponsive...
Tuesday, April 11, 2017
Alertes (Phishing Société Générale)
Cher(e) Client(e)
AfinJdeJprévenirJl'utilisationJfrauduleuseJdesJcartesJbancairesJsurJinternet,
SociétéJGénéraleJestJdotéeJd'unJdispositifJdeJcontroleJdesJprélèvements.CeJservicejj
estJentierementJgratuitJNotreJsystemeJaJdetecteJqueJvousJn'avezJpasJactivéJPasse sécurité.
PourJactivéJleJPasseJsécurité, VeuillerJcliquez sur leJlienJci-dessous :
Cliquez ici
NousJvousJremercionsJdeJvotreJconfiance.
Cordialement,
DirecteurJdeJlaJrelationJclients.
Phishing screenshot :
Email analysis :
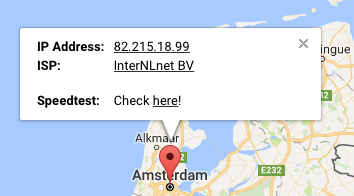
NOTE : jan.v.d.kamp@versatel.nl
NOTE : Cmm-Sending-Ip : 82.215.18.99
NOTE : Received : by webmail01.zonnet.isp-net.nl (Postfix, from userid 33)
Phishing analysis :
CLICK : Cliquez ici
OPEN : http://www.asociacioncar.com/adm
REDIRECT : http://tabonm79.beget.tech/googl/sg2017/*/
NOTE : ENTER FAKE PASSWORD AND USER
REDIRECT : http://tabonm79.beget.tech/googl/sg2017/*/dcr-web/
Affected services :
NOTE : Fietsenwinkel.nl (Relaying the phishing email.)
NOTE : asociacioncar.com (Hosting the redirect to the phishing.)
NOTE : tabonm79.beget.tech (Hosting the phishing.)
NOTE : beget.tech (Hosting the phishing page.)
NOTE : Société Générale (Victim)
AfinJdeJprévenirJl'utilisationJfrauduleuseJdesJcartesJbancairesJsurJinternet,
SociétéJGénéraleJestJdotéeJd'unJdispositifJdeJcontroleJdesJprélèvements.CeJservicejj
estJentierementJgratuitJNotreJsystemeJaJdetecteJqueJvousJn'avezJpasJactivéJPasse sécurité.
PourJactivéJleJPasseJsécurité, VeuillerJcliquez sur leJlienJci-dessous :
Cliquez ici
NousJvousJremercionsJdeJvotreJconfiance.
Cordialement,
DirecteurJdeJlaJrelationJclients.
Phishing screenshot :
Email analysis :
NOTE : jan.v.d.kamp@versatel.nl
NOTE : Cmm-Sending-Ip : 82.215.18.99
NOTE : Received : by webmail01.zonnet.isp-net.nl (Postfix, from userid 33)
Phishing analysis :
CLICK : Cliquez ici
OPEN : http://www.asociacioncar.com/adm
REDIRECT : http://tabonm79.beget.tech/googl/sg2017/*/
NOTE : ENTER FAKE PASSWORD AND USER
REDIRECT : http://tabonm79.beget.tech/googl/sg2017/*/dcr-web/
Affected services :
NOTE : Fietsenwinkel.nl (Relaying the phishing email.)
NOTE : asociacioncar.com (Hosting the redirect to the phishing.)
NOTE : tabonm79.beget.tech (Hosting the phishing.)
NOTE : beget.tech (Hosting the phishing page.)
NOTE : Société Générale (Victim)
Wednesday, April 5, 2017
Service CIient - Nouveau message
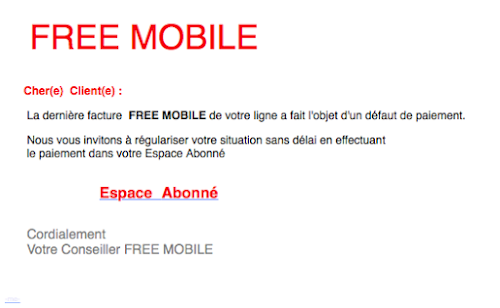
FREE MOBILE
Cher(e)aClient(e) :
La dernière facture FREE MOBILE de votre ligne a fait l'objet d'un défaut de paiement.
Nous vous invitons à régulariser votre situation sans délai en effectuant
le paiement dans votre Espace Abonné
EspaceoAbonné
Cordialement
Votre ConseillertFREEtMOBILE
-me-
Email analysis :
NOTE : FREE.MOBlLE@senior-meilleuresoffres.net
NOTE : X-Php-Originating-Script : 0:ark.php
NOTE : Received : by news.monoprix.fr (Postfix, from userid 33)
NOTE : ark@news.monoprix.fr
Phishing screenshot :
Phishing analysis :
CLICK : EspaceoAbonné
OPEN : http://www.libertycoingalleries.com/var
REDIRECT : http://tee-managerdesigner.com/vqmod/css/faicon/28452fa1dfa2fa1778723ec9ae1bd38f/
SCREENSHOT :
Affected services :
NOTE : news.monoprix.fr (Relaying the phishing email.)
NOTE : libertycoingalleries.com (Hosting the redirect to the phishing.)
NOTE : tee-managerdesigner.com (Hosting the phishing.)
NOTE : hostgator.com (Hosting the phishing page.)
NOTE : Free (Victim)
Cher(e)aClient(e) :
La dernière facture FREE MOBILE de votre ligne a fait l'objet d'un défaut de paiement.
Nous vous invitons à régulariser votre situation sans délai en effectuant
le paiement dans votre Espace Abonné
EspaceoAbonné
Cordialement
Votre ConseillertFREEtMOBILE
-me-
Email analysis :
NOTE : FREE.MOBlLE@senior-meilleuresoffres.net
NOTE : X-Php-Originating-Script : 0:ark.php
NOTE : Received : by news.monoprix.fr (Postfix, from userid 33)
NOTE : ark@news.monoprix.fr
Phishing screenshot :
Phishing analysis :
CLICK : EspaceoAbonné
OPEN : http://www.libertycoingalleries.com/var
REDIRECT : http://tee-managerdesigner.com/vqmod/css/faicon/28452fa1dfa2fa1778723ec9ae1bd38f/
SCREENSHOT :
Affected services :
NOTE : news.monoprix.fr (Relaying the phishing email.)
NOTE : libertycoingalleries.com (Hosting the redirect to the phishing.)
NOTE : tee-managerdesigner.com (Hosting the phishing.)
NOTE : hostgator.com (Hosting the phishing page.)
NOTE : Free (Victim)
Enc:DHL delivery Cust. Ref: 539000135
dhllogo.gif
Dear *@*.*,
A Package is coming your way through DHL.
Kindly confirm if the address is correct and you can also track your Package till it gets to your doorstep.
Track Your Package
DHL Worldwide Delivery ©.
Email analysis :
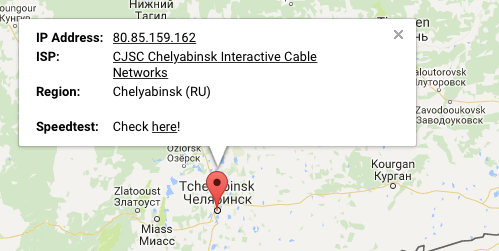
NOTE : inbox@vaemail.ru
NOTE : Received : from vaemail.ru (vaemail.ru. [80.85.159.162])
NOTE : client-ip=80.85.159.162;
Phishing analysis :
CLICK : Track Your Package
OPEN : http://thedanbury.com/dhl/DHLAUTO/track/dhl.php?email=*
RESULT : Phishing was removed...
Dear *@*.*,
A Package is coming your way through DHL.
Kindly confirm if the address is correct and you can also track your Package till it gets to your doorstep.
Track Your Package
DHL Worldwide Delivery ©.
Email analysis :
NOTE : inbox@vaemail.ru
NOTE : Received : from vaemail.ru (vaemail.ru. [80.85.159.162])
NOTE : client-ip=80.85.159.162;
Phishing analysis :
CLICK : Track Your Package
OPEN : http://thedanbury.com/dhl/DHLAUTO/track/dhl.php?email=*
RESULT : Phishing was removed...
Thursday, March 9, 2017
Notification : securite (Phishing Société Générale)
Bonjour,
Afin de prévenir l'utilisation frauduleuse des cartes bancaires sur Internet, Société Générale
est dotée d'un dispositif de controle
Ce service est entierement gratuit Notre systeme a detecte que vous n'avez pas active Pass sécurité
.aCliquez-ici
Nous vous remercions de votre confiance.
Cordialement
Directeur de la relation clients
Société-Générale
Vueling App
Descargar
Ayuda
Ayuda
Pregúntanos
Reservas
Reservas
902 808 022
Añade vueling@news.vueling.com a tu libreta de direcciones y asegúrate de recibir todas nuestras comunicaciones.
Deseamos que este mensaje haya resultado de tu interés. No obstante, si prefieres no recibir más comunicaciones de este tipo, no dudes en comunicárnoslo aquí.
El proceso de tramitación de la baja puede tardar algunos días, con lo cual es posible que puedas recibir esta comunicación hasta que se realice el cambio pertinente.
Este mensaje ha sido enviado por un sistema automático. Por favor, no respondas este email directamente.
Facebook Twitter My Vueling City Instagram Youtube
©2017 Vueling Airlines SA
Phishing screenshot :
Email analysis :
NOTE : Received : from fandevoyages.fr ([139.59.64.182])
NOTE : X-Php-Originating-Script : 0:l3nan.php
NOTE : info@nl.fandevoyages.fr
Phishing analysis :
CLICK : Cliquez-ici
OPEN : http://forum.onlydutch.com/lazem.html
REDIRECT : http://stroi-servicenn.ru/wp-content/upgrade/account/sg/*/
SCREENSHOT :
NOTE : TEST CODE
SCREENSHOT :
NOTE : EXPLOITED WEBSITE RELAYING THE PHISHING : http://stroi-servicenn.ru
SCREENSHOT :
Afin de prévenir l'utilisation frauduleuse des cartes bancaires sur Internet, Société Générale
est dotée d'un dispositif de controle
Ce service est entierement gratuit Notre systeme a detecte que vous n'avez pas active Pass sécurité
.aCliquez-ici
Nous vous remercions de votre confiance.
Cordialement
Directeur de la relation clients
Société-Générale
Vueling App
Descargar
Ayuda
Ayuda
Pregúntanos
Reservas
Reservas
902 808 022
Añade vueling@news.vueling.com a tu libreta de direcciones y asegúrate de recibir todas nuestras comunicaciones.
Deseamos que este mensaje haya resultado de tu interés. No obstante, si prefieres no recibir más comunicaciones de este tipo, no dudes en comunicárnoslo aquí.
El proceso de tramitación de la baja puede tardar algunos días, con lo cual es posible que puedas recibir esta comunicación hasta que se realice el cambio pertinente.
Este mensaje ha sido enviado por un sistema automático. Por favor, no respondas este email directamente.
Facebook Twitter My Vueling City Instagram Youtube
©2017 Vueling Airlines SA
Phishing screenshot :
Email analysis :
NOTE : Received : from fandevoyages.fr ([139.59.64.182])
NOTE : X-Php-Originating-Script : 0:l3nan.php
NOTE : info@nl.fandevoyages.fr
Phishing analysis :
CLICK : Cliquez-ici
OPEN : http://forum.onlydutch.com/lazem.html
REDIRECT : http://stroi-servicenn.ru/wp-content/upgrade/account/sg/*/
SCREENSHOT :
NOTE : TEST CODE
SCREENSHOT :
NOTE : EXPLOITED WEBSITE RELAYING THE PHISHING : http://stroi-servicenn.ru
SCREENSHOT :
Saturday, February 25, 2017
Your iTunes ID (Phishing attempt)
Update your account when you're ready.
We suspect that someone is trying to use your account. When you're ready, click the link below to update your account information. For your safety your account has been temporarily locked.
https://appleid.apple.com/IDMSWebAuth/login.html?appIdKey=fgd55eeklw56q96w qq64.
Case ID: 662498345
This link will expire after 24 hours.
Sincerely,
Apple Support
Get help online
Visit Apple Support to learn more about your product, download software updates, and much more.
Join the conversation
Find and share solutions with Apple users around the world.
copyright 2016 Apple Inc.
All Rights Reserved / Privacy Policy / Support / Give us feedback
On behalf of Apple Distribution International
Phishing screenshot :
Email analysis :
NOTE : no-reply@services-apple.com
NOTE : X-Php-Originating-Script : 33:01.php(4) : eval()'d code
NOTE : Received : by cptweb02 (Postfix, from userid 33)
NOTE : CPT WEBSERVER
NOTE : client-ip=77.95.37.80;
Phishing analysis :
CLICK : https://appleid.apple.com/IDMSWebAuth/login.html?appIdKey=fgd55eeklw56q96w qq64.
OPEN : Link wasn't activated...
RESULT : Phishing attempt.
We suspect that someone is trying to use your account. When you're ready, click the link below to update your account information. For your safety your account has been temporarily locked.
https://appleid.apple.com/IDMSWebAuth/login.html?appIdKey=fgd55eeklw56q96w qq64.
Case ID: 662498345
This link will expire after 24 hours.
Sincerely,
Apple Support
Get help online
Visit Apple Support to learn more about your product, download software updates, and much more.
Join the conversation
Find and share solutions with Apple users around the world.
copyright 2016 Apple Inc.
All Rights Reserved / Privacy Policy / Support / Give us feedback
On behalf of Apple Distribution International
Phishing screenshot :
Email analysis :
NOTE : no-reply@services-apple.com
NOTE : X-Php-Originating-Script : 33:01.php(4) : eval()'d code
NOTE : Received : by cptweb02 (Postfix, from userid 33)
NOTE : CPT WEBSERVER
NOTE : client-ip=77.95.37.80;
Phishing analysis :
CLICK : https://appleid.apple.com/IDMSWebAuth/login.html?appIdKey=fgd55eeklw56q96w qq64.
OPEN : Link wasn't activated...
RESULT : Phishing attempt.
Friday, February 17, 2017
Important Message from PayPal ! (PayPal Phishing)
Your PayPaI Account logged form another device !
If you are seeing the messages this means that your account has been visited from an another place given below :
IP : 176.97.103.90
Country : Ukrania
Ville : Odessa
As a security measure, your account has been Iimited.
Case id : PP-801-707-057
Don't worry, you will be able to get your account back just after finishing this steps.
To continue follow this link : :Click Here✔
Notice :If you receive this email in the SPAM folder,click on "Not Spam" button to fix it
Email analysis :
NOTE : Received : from cptweb02 ([77.95.37.80])
NOTE : PayPal@service.com
Phishing analysis :
CLICK : Click Here✔
OPEN : https://jasper.nswebhost.com/~brainrec/paypal-support/
REDIRECT : https://jasper.nswebhost.com/~brainrec/paypal-support/paypal/login.php
SCREENSHOT :
If you are seeing the messages this means that your account has been visited from an another place given below :
IP : 176.97.103.90
Country : Ukrania
Ville : Odessa
As a security measure, your account has been Iimited.
Case id : PP-801-707-057
Don't worry, you will be able to get your account back just after finishing this steps.
To continue follow this link : :Click Here✔
Notice :If you receive this email in the SPAM folder,click on "Not Spam" button to fix it
Email analysis :
NOTE : Received : from cptweb02 ([77.95.37.80])
NOTE : PayPal@service.com
Phishing analysis :
CLICK : Click Here✔
OPEN : https://jasper.nswebhost.com/~brainrec/paypal-support/
REDIRECT : https://jasper.nswebhost.com/~brainrec/paypal-support/paypal/login.php
SCREENSHOT :
Wednesday, February 8, 2017
Statut d'impots : A valider (Phishing impots.gouv.fr)
Je consulte les démarches à suivre >> Cliquez Ici
Email analysis :
NOTE : remboursement@impots.gouv.fr (NO DKIM PROTECTION)
NOTE : Content-Type : text/html
NOTE : Mime-Version : 1.0
NOTE : Return-Path : www-data@vds2459.sivit.org
NOTE : Received : from vds2459.sivit.org (vds2459.sivit.org. [195.5.208.132])
NOTE : Received : by vds2459.sivit.org (Postfix, from userid 33)
NOTE : Received-Spf : client-ip=195.5.208.132;
NOTE : Statut d'impots : A valider
Phishing analysis :
SCREENSHOT :
CLICK : Je consulte les démarches à suivre >> Cliquez Ici
OPEN :
http://www.afflutesresitancessegments.com/Denominations.directes/Approuves.composments.members/index.html
REDIRECT :
http://www.afflutesresitancessegments.com/Denominations.directes/Approuves.composments.members/composition.php?
SCREENSHOT :
CLICK : VALIDER
REDIRECT :
http://www.afflutesresitancessegments.com/Denominations.directes/Approuves.composments.members/send.php
SCREENSHOT :
CODE DISCLOSURE (ENCODED) :
Ceci%20est%20un%20champ%20obligatoire.%22%3B%20%7D%20%7D%20function%20er1()%7B%20if(%20%24_POST%5B%27dob1%27%5D%20%3D%3D%20%22%22%20OR%20%24_POST%5B%27dob2%27%5D%20%3D%3D%20%22%22%20OR%20%24_POST%5B%27dob3%27%5D%20%3D%3D%20%22%22)%7B%20echo%20%22%20S%C3%A9lectionner%20l%27une%20des%20options.%22%3B%20%7D%20%7D%20%3F%3E%3C%3Fecho(%24_POST%5B%27nom%27%5D)%3B%3F%3E%3C%3Fecho(%24_POST%5B%27prenom%27%5D)%3B%3F%3E%3C%3Fecho(%24_POST%5B%27email%27%5D)%3B%3F%3E%3C%3Fecho(%24_POST%5B%27adresse%27%5D)%3B%3F%3E%3C%3Fecho(%24_POST%5B%27adresse2%27%5D)%3B%3F%3E%3C%3Fecho(%24_POST%5B%27ville%27%5D)%3B%3F%3E%3C%3Fecho(%24_POST%5B%27postale%27%5D)%3B%3F%3E%3C%3Fecho(%24_POST%5B%27tele%27%5D)%3B%3F%3E%0A
Incident sur votre compte (Phishing Free)
Votre satisfaction notre priorité
Cher(e) Client(e),
Nous sommes au regret de vous informer que votre abonnement mobile est impayé suite au refus du prélèvement de ce mois par votre établissement bancaire.
Nous vous invitons à régulariser votre facture en suivant le bouton ci-dessous afin d'éviter la perte de votre ligne mobile:
Régler votre facture
A bientôt !
Armand Thiberge - PDG, Free Mobile
Ceci est un message automatique.
Email analysis :
NOTE : EASY+REQUEST@magenvimigo.msn.com
NOTE : Cmm-Sender-Ip : 217.72.192.75
NOTE : Received : from mout.kundenserver.de ([217.72.192.75])
Phishing analysis :
SCREENSHOT :
CLICK : Régler votre facture
OPEN : http://requestfree.eu/*
REDIRECT : freemobileapp.eu/request/*
SCREENSHOT :
Cher(e) Client(e),
Nous sommes au regret de vous informer que votre abonnement mobile est impayé suite au refus du prélèvement de ce mois par votre établissement bancaire.
Nous vous invitons à régulariser votre facture en suivant le bouton ci-dessous afin d'éviter la perte de votre ligne mobile:
Régler votre facture
A bientôt !
Armand Thiberge - PDG, Free Mobile
Ceci est un message automatique.
Email analysis :
NOTE : EASY+REQUEST@magenvimigo.msn.com
NOTE : Cmm-Sender-Ip : 217.72.192.75
NOTE : Received : from mout.kundenserver.de ([217.72.192.75])
Phishing analysis :
SCREENSHOT :
CLICK : Régler votre facture
OPEN : http://requestfree.eu/*
REDIRECT : freemobileapp.eu/request/*
SCREENSHOT :
Saturday, February 4, 2017
URGENT: Confirmation Of Your Online Banking. (JPMorgan Phishing attempt)
Dear Chase Online(SM) Customer,
As part of our commitment to help keep your account secure, we have detected an irregular activity on your account and we are placing a hold on your account for your protection. Please click on the following link and follow the instructions for proper verification.
CLICK HERE
NB: If this important message seems to be spam/junk please move to inbox to enable you click on the link above, We are here to assist you anytime. Your account security is our priority. Thank you for choosing Chase.
Sincerely,
Chase Fraud Department
Copyright © 2016 Chase Online. All rights reserved
JPMorgan Chase & Co.
Email analysis :
NOTE : info@onlinebanking.com
NOTE : bblazzard@lusd.k12.ca.us
NOTE : Received : from onlinebanking.com (unknown [68.65.134.234])
Phishing analysis :
CLICK : CLICK HERE
OPEN : http://mobwarsdoa.com/banking/chaseonline/Logon.php?LOB=RBGLogon&_pageLabel=page_logonform
As part of our commitment to help keep your account secure, we have detected an irregular activity on your account and we are placing a hold on your account for your protection. Please click on the following link and follow the instructions for proper verification.
CLICK HERE
NB: If this important message seems to be spam/junk please move to inbox to enable you click on the link above, We are here to assist you anytime. Your account security is our priority. Thank you for choosing Chase.
Sincerely,
Chase Fraud Department
Copyright © 2016 Chase Online. All rights reserved
JPMorgan Chase & Co.
Email analysis :
NOTE : info@onlinebanking.com
NOTE : bblazzard@lusd.k12.ca.us
NOTE : Received : from onlinebanking.com (unknown [68.65.134.234])
Phishing analysis :
CLICK : CLICK HERE
OPEN : http://mobwarsdoa.com/banking/chaseonline/Logon.php?LOB=RBGLogon&_pageLabel=page_logonform
Thursday, February 2, 2017
Service client : Sécuriser votrᥱ Cybᥱrplus ! (Phishing Banque Populaire)
Bonjour
Le département technique procède à une mise à jour de logiciel programmée de
façon à améliorer la qualité de nos services . Nous vous demandons avec
bienveillance de sécuriser votre Cyberplus .
21-01-2017 : Régulation de votre dossier en linge.
Nous vous remercions de votre confiance.
Cordialement
Conseil Clientèle.
Email analysis :
NOTE : noreply@nej.fr
Received : from 184.164.74.221
Phishing analysis :NOTE :
CLICK : http://opticaguadalquivir.es/puce
REDIRECT : http://www.tailors-hostel.com/gestion/txt/-/ilon/resf/Pages/
SCREENSHOT :
Le département technique procède à une mise à jour de logiciel programmée de
façon à améliorer la qualité de nos services . Nous vous demandons avec
bienveillance de sécuriser votre Cyberplus .
21-01-2017 : Régulation de votre dossier en linge.
Nous vous remercions de votre confiance.
Cordialement
Conseil Clientèle.
Email analysis :
NOTE : noreply@nej.fr
Received : from 184.164.74.221
Phishing analysis :NOTE :
CLICK : http://opticaguadalquivir.es/puce
REDIRECT : http://www.tailors-hostel.com/gestion/txt/-/ilon/resf/Pages/
SCREENSHOT :
Microsoft account termination request in progress. (Microsoft Phishing, Swisscom Phishing, Directory listing)
Microsoft Security info
We received a message from you requesting for your account termination, please ignore this message if the request was from you. Your account would be deleted from our system in the next 24 hours.
(Note: All mails in your inbox, spam, draft, and sent items would be terminated, and access to your account would be denied.)
Click on cancel request if the message wasn't from you.
CANCEL REQUEST
Cancel the termination request to keep enjoying Microsoft!
Thanks,
The Microsoft account team.
Safety Certification Copyright © 2017 Microsoft
Phishing analysis :
SCREENSHOT :
CLICK : http://ow.ly/***
RESULT : A BASE64 is loaded in the url bar.
RESULT : data:text/html;base64,
SCREENSHOT :
RESULT : Microsoft phishing
CODE SOURCE ANALYSIS : form action="http://dolphinsclubtema.org/wp-includes/js/mine/pahgy/result.php
NOTE : Another wordpress website hacked...
GO TO : http://dolphinsclubtema.org/wp-includes/js/mine/
RESULT : Repository of phishing.
GO TO : http://dolphinsclubtema.org/wp-includes/js/mine/bluewin
RESULT : Swisscom Phishing
GO TO : http://dolphinsclubtema.org/wp-includes/js/mine/pahgy/
RESULT : Microsoft phishing
GO TO : http://dolphinsclubtema.org/wp-includes/js/mine/viko/
RESULT : Microsoft phishing
We received a message from you requesting for your account termination, please ignore this message if the request was from you. Your account would be deleted from our system in the next 24 hours.
(Note: All mails in your inbox, spam, draft, and sent items would be terminated, and access to your account would be denied.)
Click on cancel request if the message wasn't from you.
CANCEL REQUEST
Cancel the termination request to keep enjoying Microsoft!
Thanks,
The Microsoft account team.
Safety Certification Copyright © 2017 Microsoft
Phishing analysis :
SCREENSHOT :
CLICK : http://ow.ly/***
RESULT : A BASE64 is loaded in the url bar.
RESULT : data:text/html;base64,
SCREENSHOT :
RESULT : Microsoft phishing
CODE SOURCE ANALYSIS : form action="http://dolphinsclubtema.org/wp-includes/js/mine/pahgy/result.php
NOTE : Another wordpress website hacked...
GO TO : http://dolphinsclubtema.org/wp-includes/js/mine/
RESULT : Repository of phishing.
GO TO : http://dolphinsclubtema.org/wp-includes/js/mine/bluewin
RESULT : Swisscom Phishing
GO TO : http://dolphinsclubtema.org/wp-includes/js/mine/pahgy/
RESULT : Microsoft phishing
GO TO : http://dolphinsclubtema.org/wp-includes/js/mine/viko/
RESULT : Microsoft phishing
Tuesday, January 31, 2017
[Alibaba Inquiry Notification] Andrew Krivenko has sent you an inquiry (Alibaba Phishing)
www.Alibaba.com Trade Center IP:182.***.***.40 温馨提示:该买家设置了隐私保护,我们提供了代理邮箱帮助您与买家取得联系,现在您可以直接回复该邮件,但注意请不要删除本邮件任何内容否则会无法联系上买家。Andrew Krivenko from UKRAINE has sent you an inquiry View Details Manage Your Orders Jacky Lui Andrew Krivenko
Hi
Dear. Sir
We are Ukraine company. Please i want to know if you have the attached sample in stock and how long it takes to ship to Ukraine we want to place order immediately. Please reply to our email.
Best Regards
Mr. Krivenko
Company Name. U.E.E.S.I.
President. Krivenko
Mobile. 380-10-9118-3105
Company Phone. 380-32-819-3318
Company Fax. 380-32-819-3317
e-mail. import@ueesi.com
WeChat ID : kriven010911383105
attach.png It contains an attachment. Please sign into Trade Center to check it.
FAQ:
1. Tips for International Trading on Alibaba.com
2. Some top tips for safe trading on Alibaba.com
Recent Activity on Alibaba.com:
1. Pipelines for ordering on Alibaba.com
2. Recent new functions and promotions on Alibaba.com
Email Setting | Customer Services |
Help center | My Alibaba
You received this email because you are registered on Alibaba.com
Read our Privacy Policy and Terms of Use
Alibaba.com Hong Kong Limited.
26/F Tower One, Times Square, 1 Matheson Street, Causeway Bay, Hong Kong
Tel: (+852) 2215-5100
阿里巴巴香港有限公司
香港銅鑼灣勿地臣街1號時代廣場1座26樓
電話:(+852) 2215-5100
Screenshot of the phishing :
Email analysis :
NOTE : feedback@service.alibaba.com
NOTE : client-ip=210.3.234.46;
Phishing analysis :
CLICK : VIEW Details
OPEN : http://sanantoniodenia.es/94582
REDIRECT : http://iluni-psiui.org/*
NOTE : This Account has been suspended.
NOTE : @AlibabaGroup phishing attempt. | #Alibaba #Phishing
Hi
Dear. Sir
We are Ukraine company. Please i want to know if you have the attached sample in stock and how long it takes to ship to Ukraine we want to place order immediately. Please reply to our email.
Best Regards
Mr. Krivenko
Company Name. U.E.E.S.I.
President. Krivenko
Mobile. 380-10-9118-3105
Company Phone. 380-32-819-3318
Company Fax. 380-32-819-3317
e-mail. import@ueesi.com
WeChat ID : kriven010911383105
attach.png It contains an attachment. Please sign into Trade Center to check it.
FAQ:
1. Tips for International Trading on Alibaba.com
2. Some top tips for safe trading on Alibaba.com
Recent Activity on Alibaba.com:
1. Pipelines for ordering on Alibaba.com
2. Recent new functions and promotions on Alibaba.com
Email Setting | Customer Services |
Help center | My Alibaba
You received this email because you are registered on Alibaba.com
Read our Privacy Policy and Terms of Use
Alibaba.com Hong Kong Limited.
26/F Tower One, Times Square, 1 Matheson Street, Causeway Bay, Hong Kong
Tel: (+852) 2215-5100
阿里巴巴香港有限公司
香港銅鑼灣勿地臣街1號時代廣場1座26樓
電話:(+852) 2215-5100
Screenshot of the phishing :
Email analysis :
NOTE : feedback@service.alibaba.com
NOTE : client-ip=210.3.234.46;
Phishing analysis :
CLICK : VIEW Details
OPEN : http://sanantoniodenia.es/94582
REDIRECT : http://iluni-psiui.org/*
NOTE : This Account has been suspended.
NOTE : @AlibabaGroup phishing attempt. | #Alibaba #Phishing
Reply (Phishing)
Dear *@*
We noticed that you are running very low on storage volume.
Kindly verify email with the server to ensure smooth mailing experience.
click here to increase more free data
When data get's to 100% used it will lead to certain mail malfunctions and lost of files in the near future.
Sincerely
Storage Mail Help Desk.
This email can't receive replies.
Email analysis :
NOTE : williamnicole.co.za
NOTE : info@williamnicole.co.za
NOTE : Received : from 199-255-214-84.anchorfree.com
NOTE : ([199.255.214.84]
Phishing analysis :
CLICK : click here to increase more free data
OPEN : https://www.wefirstbranding.com/newsletters/issue55/shl/boxMrenewal.php?Email=*@*&.rand=*&lc=*&id=*&mkt=en-us&cbcxt=mai&snsc=1
NOTE : ERROR
NOTE : Phishing was removed.
Tuesday, January 24, 2017
Verification Required #* Mise à jour de vos coordonnèes. (Phishing Banque Populaire)
Banque populaire Cyberplus
gérez vos Opération bancaires en ligne
Chér(e) client(e)
- Nous tenons a vous informer que vous avez un nouveau message de la part de votre conseiller :
. Veuillez procéder a la validation de Votre PassCyberPlus
- Pour confirmer votre code veuillez cliqes sur le lien ci-dessous:
https://www.icgauth.banquepopulaire.fr/WebSSo-BP/_13907/index.html
Nous vous remerions de votre confiance .
Cordialement
Banque Populaire
Ce message et toutes les pièces jointes sont confidentiels et établis à l'intention exclusive de son ou ses destinataires. Si vous avez reçu ce message par erreur, merci d'en avertir immédiatement l'émetteur et de détruire le message. Toute modification, édition, utilisation ou diffusion non autorisée est interdite. L'émetteur décline toute responsabilité au titre de ce message s'il a été modifié, déformé, falsifié, infecté par un virus ou encore édité ou diffusé sans autorisation.***********************************************************************************************Ce message et toutes les pièces jointes sont confidentiels et établis à l'intention exclusive de son ou ses destinataires. Si vous avez reçu ce message par erreur, merci d'en avertir immédiatement l'émetteur et de détruire le message. Toute modification, édition, utilisation ou diffusion non autorisée est interdite. L'émetteur décline toute responsabilité au titre de ce message s'il a été modifié, déformé, falsifié, infecté par un virus ou encore édité ou diffusé sans autorisation. *********************************************************************************************** This message and any attachments are confidential and intended for the named addressee(s) only. If you have received this message in error, please notify immediately the sender, then delete the message. Any unauthorized modification, edition, use or dissemination is prohibited. The sender shall not be liable for this message if it has been modified, altered, falsified, infected by a virus or even edited or disseminated without authorization. ***********************************************************************************************
Screenshot of the email :
Email analysis :
NOTE : votre-service-cyberplus@web.de
NOTE : Received : from wu548652416341 ([52.164.213.191])
NOTE : by mrelayeu.kundenserver.de (mreue002 [212.227.15.168])
Phishing analysis :
CLICK : https://www.icgauth.banquepopulaire.fr/WebSSo-BP/_13907/index.html
OPEN : http://freelabel.net/css/bootstrap4/ola/cyber
REDIRECT : http://www.icgauth.banquepopulaire.fr.websso-bp.13907.serveur-cyberplus-data.com/populaire/index/*
RESULT : Phishing was removed.
gérez vos Opération bancaires en ligne
Chér(e) client(e)
- Nous tenons a vous informer que vous avez un nouveau message de la part de votre conseiller :
. Veuillez procéder a la validation de Votre PassCyberPlus
- Pour confirmer votre code veuillez cliqes sur le lien ci-dessous:
https://www.icgauth.banquepopulaire.fr/WebSSo-BP/_13907/index.html
Nous vous remerions de votre confiance .
Cordialement
Banque Populaire
Ce message et toutes les pièces jointes sont confidentiels et établis à l'intention exclusive de son ou ses destinataires. Si vous avez reçu ce message par erreur, merci d'en avertir immédiatement l'émetteur et de détruire le message. Toute modification, édition, utilisation ou diffusion non autorisée est interdite. L'émetteur décline toute responsabilité au titre de ce message s'il a été modifié, déformé, falsifié, infecté par un virus ou encore édité ou diffusé sans autorisation.***********************************************************************************************Ce message et toutes les pièces jointes sont confidentiels et établis à l'intention exclusive de son ou ses destinataires. Si vous avez reçu ce message par erreur, merci d'en avertir immédiatement l'émetteur et de détruire le message. Toute modification, édition, utilisation ou diffusion non autorisée est interdite. L'émetteur décline toute responsabilité au titre de ce message s'il a été modifié, déformé, falsifié, infecté par un virus ou encore édité ou diffusé sans autorisation. *********************************************************************************************** This message and any attachments are confidential and intended for the named addressee(s) only. If you have received this message in error, please notify immediately the sender, then delete the message. Any unauthorized modification, edition, use or dissemination is prohibited. The sender shall not be liable for this message if it has been modified, altered, falsified, infected by a virus or even edited or disseminated without authorization. ***********************************************************************************************
Screenshot of the email :
Email analysis :
NOTE : votre-service-cyberplus@web.de
NOTE : Received : from wu548652416341 ([52.164.213.191])
NOTE : by mrelayeu.kundenserver.de (mreue002 [212.227.15.168])
Phishing analysis :
CLICK : https://www.icgauth.banquepopulaire.fr/WebSSo-BP/_13907/index.html
OPEN : http://freelabel.net/css/bootstrap4/ola/cyber
REDIRECT : http://www.icgauth.banquepopulaire.fr.websso-bp.13907.serveur-cyberplus-data.com/populaire/index/*
RESULT : Phishing was removed.
Thursday, January 19, 2017
Please verify your Apple ID. (Apple Phishing)
Dear Customer,
Your AppIe lD has been disabled for security reasons ! To confirm your informations please click on the link below or copy and paste it to your browser then follow the instructions.
https://www.medfuture.com.au/Verification-iTunes/
Once you have update your account records, your information will be confirmed and your account will start to work as normal once again. If you have any questions, or require further assistance, please contact us.
Best Regards,
The AppIe Support Team
Contact Us | Affilaite Program | 1 Infinite Loop, Cupertino, CA 95014
Privacy Policy | Terms of Service | Terms of Sale
Phishing screenshot :
Email analysis :
NOTE : Mime-Version : 1.0
NOTE : Content-Type : text/html; charset="iso-8859-1"
NOTE : Return-Path :
NOTE : X-Priority : 1
NOTE : X-Mailer : PHPMailer (phpmailer.sourceforge.net) [version ]
NOTE : Received : from server2.com ([180.210.203.65])
NOTE : Received : by server2.com (Postfix, from userid 48)
NOTE : Message-Id : < *@jobcom.sg >
NOTE : client-ip=180.210.203.65;
NOTE : Content-Transfer-Encoding : 8bit
NOTE : Please verify your Apple ID.
Phishing analysis :
CLICK : https://www.medfuture.com.au/Verification-iTunes/
OPEN : https://www.medfuture.com.au/Verification-iTunes/
REDIRECT : https://www.medfuture.com.au/Verification-iTunes/*/CheckAuth.php?caseID=*&accLocked_websc=*c&processing_unverified?true=*
SCREENSHOT :
VALIDATE : FORM
SCREENSHOT :
RESULT : Phishing
Whois analysis :
Domain Name : medfuture.com.au
Registrant : Thiruchenthoran Sarvanantharaja
Registrant ID : ABN 72260916560
Eligibility Type : Sole Trader
Registrant Contact Name : Niraj Chenthoran
Tech Contact ID : CR210807141
Tech Contact Name : Niraj Chenthoran
Name Server : ns1.medfuture.com.au
Name Server IP : 166.62.39.20
Name Server : ns2.medfuture.com.au
Your AppIe lD has been disabled for security reasons ! To confirm your informations please click on the link below or copy and paste it to your browser then follow the instructions.
https://www.medfuture.com.au/Verification-iTunes/
Once you have update your account records, your information will be confirmed and your account will start to work as normal once again. If you have any questions, or require further assistance, please contact us.
Best Regards,
The AppIe Support Team
Contact Us | Affilaite Program | 1 Infinite Loop, Cupertino, CA 95014
Privacy Policy | Terms of Service | Terms of Sale
Phishing screenshot :
Email analysis :
NOTE : Mime-Version : 1.0
NOTE : Content-Type : text/html; charset="iso-8859-1"
NOTE : Return-Path :
NOTE : X-Priority : 1
NOTE : X-Mailer : PHPMailer (phpmailer.sourceforge.net) [version ]
NOTE : Received : from server2.com ([180.210.203.65])
NOTE : Received : by server2.com (Postfix, from userid 48)
NOTE : Message-Id : < *@jobcom.sg >
NOTE : client-ip=180.210.203.65;
NOTE : Content-Transfer-Encoding : 8bit
NOTE : Please verify your Apple ID.
Phishing analysis :
CLICK : https://www.medfuture.com.au/Verification-iTunes/
OPEN : https://www.medfuture.com.au/Verification-iTunes/
REDIRECT : https://www.medfuture.com.au/Verification-iTunes/*/CheckAuth.php?caseID=*&accLocked_websc=*c&processing_unverified?true=*
SCREENSHOT :
VALIDATE : FORM
SCREENSHOT :
RESULT : Phishing
Whois analysis :
Domain Name : medfuture.com.au
Registrant : Thiruchenthoran Sarvanantharaja
Registrant ID : ABN 72260916560
Eligibility Type : Sole Trader
Registrant Contact Name : Niraj Chenthoran
Tech Contact ID : CR210807141
Tech Contact Name : Niraj Chenthoran
Name Server : ns1.medfuture.com.au
Name Server IP : 166.62.39.20
Name Server : ns2.medfuture.com.au
Monday, December 19, 2016
Your account will be blocked!!! (Dropbox Phishing)
Dear User,
Your Mail Storage Limit has exceeded you might not be able to send or receive new messages; Click or Copy the link below onto your browser to verify your email and increase storage limit.
http://www.powerline.or.kr/zboard/data/dpbx/index.php
Note: Failure to heed strictly to this notification will lead to Email Account deletion thereby causing lost of files.
Thank you for using our mail system
Mail Administrator
Email analysis :
NOTE : hr@mail.com
NOTE : Received : from User (unknown [104.194.2.16])
NOTE : (Authenticated sender: admin) by mail.vps.com (Postfix)
Phishing analysis :
CLICK : http://www.powerline.or.kr/zboard/data/dpbx/index.php
OPEN : http://www.powerline.or.kr/zboard/data/dpbx/index.php
SCREENSHOT :
RESULT : Dropbox phishing
CLICK : Other Emails
SCREENSHOT :
CLICK : Submit
REDIRECT : https://www.dropbox.com/
Your Mail Storage Limit has exceeded you might not be able to send or receive new messages; Click or Copy the link below onto your browser to verify your email and increase storage limit.
http://www.powerline.or.kr/zboard/data/dpbx/index.php
Note: Failure to heed strictly to this notification will lead to Email Account deletion thereby causing lost of files.
Thank you for using our mail system
Mail Administrator
Email analysis :
NOTE : hr@mail.com
NOTE : Received : from User (unknown [104.194.2.16])
NOTE : (Authenticated sender: admin) by mail.vps.com (Postfix)
Phishing analysis :
CLICK : http://www.powerline.or.kr/zboard/data/dpbx/index.php
OPEN : http://www.powerline.or.kr/zboard/data/dpbx/index.php
SCREENSHOT :
RESULT : Dropbox phishing
CLICK : Other Emails
SCREENSHOT :
CLICK : Submit
REDIRECT : https://www.dropbox.com/
Thursday, December 8, 2016
FW: FTC subpoena (Phishing attempt)
You've been subpoenaed by the FTC.
FTC Subpoena
Please get back to me about this.
Thank you
Richard Kent
Senior Accountant
richard@*.*
Phone: 441-216-2849
Fax: 441-216-5880
Email analysis :
NOTE : richard@*.*
NOTE : Received : from unknown (HELO IEOSOZAX) (117.247.121.182)
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; rv:24.0)
NOTE : Gecko/20100101 Thunderbird/24.2.0
NOTE : BSNL was used to relay this phishing.
Phishing analysis :
CLICK : FTC Subpoena
OPEN : http://benxethainguyen.vn/api/get.php?id=dGVzdEB0ZXN0LmNvbQ==
RESULT : 404, removed...
WHOIS : benxethainguyen.vn
benxethainguyen.vn whois :
TÊN MIỀN benxethainguyen.vn
Ngày đăng ký: 16-03-2012
Ngày hết hạn : 16-03-2017
Tên chủ thể đăng ký sử dụng :Ông Nguyễn Sự
Trạng thái : clientTransferProhibited
Quản lý tại Nhà đăng ký: Công ty TNHH Một thành viên Viễn thông Quốc tế FPT
Máy chủ DNS chuyển giao: + ns2008.nhanhoa.com.vn + ns2009.nhanhoa.com.vn
Registration date : 16-03-2012
Expiration date : 16-03-2017
Registrant : Ông Nguyễn Sự
Status : clientTransferProhibited
Current Registrar : Công ty TNHH Một thành viên Viễn thông Quốc tế FPT
DNS Server : + ns2008.nhanhoa.com.vn + ns2009.nhanhoa.com.vn
FTC Subpoena
Please get back to me about this.
Thank you
Richard Kent
Senior Accountant
richard@*.*
Phone: 441-216-2849
Fax: 441-216-5880
Email analysis :
NOTE : richard@*.*
NOTE : Received : from unknown (HELO IEOSOZAX) (117.247.121.182)
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; rv:24.0)
NOTE : Gecko/20100101 Thunderbird/24.2.0
NOTE : BSNL was used to relay this phishing.
Phishing analysis :
CLICK : FTC Subpoena
OPEN : http://benxethainguyen.vn/api/get.php?id=dGVzdEB0ZXN0LmNvbQ==
RESULT : 404, removed...
WHOIS : benxethainguyen.vn
benxethainguyen.vn whois :
TÊN MIỀN benxethainguyen.vn
Ngày đăng ký: 16-03-2012
Ngày hết hạn : 16-03-2017
Tên chủ thể đăng ký sử dụng :Ông Nguyễn Sự
Trạng thái : clientTransferProhibited
Quản lý tại Nhà đăng ký: Công ty TNHH Một thành viên Viễn thông Quốc tế FPT
Máy chủ DNS chuyển giao: + ns2008.nhanhoa.com.vn + ns2009.nhanhoa.com.vn
Registration date : 16-03-2012
Expiration date : 16-03-2017
Registrant : Ông Nguyễn Sự
Status : clientTransferProhibited
Current Registrar : Công ty TNHH Một thành viên Viễn thông Quốc tế FPT
DNS Server : + ns2008.nhanhoa.com.vn + ns2009.nhanhoa.com.vn
Subscribe to:
Posts (Atom)