My contact with you is with respect to the estate of a deceased client, and an investment placed under our management 7 years ago. I am Bao Tung, Deputy Manager for the China Trust Commercial ,China. Please see the attachment for full details. If you are unable to open the attachment, please send me a mail and I will resend full details to you. Regards, Bao Tung
Email analysis :
NOTE : btung1960a@gmail.com
NOTE : Vn86btung@cantv.net
NOTE : Received : from [192.168.1.81]
NOTE : (dbe48f7d9.dslam-172-17-49-247-292-746-lms-05.dsl.cantv.net [190.72.247.217]
NOTE : (may be forged))
Tuesday, June 27, 2017
Monday, June 26, 2017
RE: REPLY.
I seek your assistance to safe keep two military trunk boxes of values that is of great benefit to we both. Do not panic as i do not pose any threat to you neither do i mean harm on you whatsoever. Be patient to hear details as soon as i see your reply to this my direct Email: caseythoreen2017@yandex.com
Email analysis :
NOTE : casey.wish@key.ocn.ne.jp
NOTE : casey2017thoreen@rediffmail.com
NOTE : caseythoreen2017@yandex.com
NOTE : Received : from User
NOTE : (p460151-ipngn200408kanazawa.ishikawa.ocn.ne.jp [180.6.168.151])
NOTE : by vckey.ocn.ne.jp (Postfix)
Email analysis :
NOTE : casey.wish@key.ocn.ne.jp
NOTE : casey2017thoreen@rediffmail.com
NOTE : caseythoreen2017@yandex.com
NOTE : Received : from User
NOTE : (p460151-ipngn200408kanazawa.ishikawa.ocn.ne.jp [180.6.168.151])
NOTE : by vckey.ocn.ne.jp (Postfix)
Friday, June 23, 2017
RE: HELLO
Hello,
I need your assistance in a deal that will be of mutual benefit for the both of us from Camp Stanley, Stationed in Uijeongbu, South Korea. Please get back to me for more info.
Thank you for your time.
Sgt. Monica Martinez
Email analysis :
NOTE : resolution@webadicta.org
NOTE : test@rachatcredits.ovh
NOTE : Received : from User (unknown [41.217.118.193])
NOTE : by ns336204.ip-91-121-204.eu
I need your assistance in a deal that will be of mutual benefit for the both of us from Camp Stanley, Stationed in Uijeongbu, South Korea. Please get back to me for more info.
Thank you for your time.
Sgt. Monica Martinez
Email analysis :
NOTE : resolution@webadicta.org
NOTE : test@rachatcredits.ovh
NOTE : Received : from User (unknown [41.217.118.193])
NOTE : by ns336204.ip-91-121-204.eu
Monday, June 19, 2017
READY FOR DELIVERY $25.6 MILLION U.S DOLLARS IN A CONSIGNMENT BOX.
Attn: Dear Mr./ Madam
This is to notify you about our agreement with Bank of New York mellon to deliver to you without delay a Diplomatic Consignment Fund valued only $25.6 MILLION U.S DOLLARS which resulted from your outstanding contract Inheritance fund Following our agreement with Federal Reserve Bank, it must interest you to Know that the delivery documentation process has been legally finalized, so All you need to do now is for you to send me Your Full Names and Your Physical Delivery Address
including Your Direct Telephone Numbers for easy communication.
Be rest assured that upon the receipt of the above information from you as requested our Diplomatic Agent will use his diplomatic immunity to move the Consignment Fund straight to your doorstep immediately, Once again, bear in mind that every aspect of the delivery has been taken care of so there is nothing holding the Consignment Fund here now.
Best regards in anticipating hearing from you.
Dr. Jude Allen
Head Director, U.S. Diplomatic Base
Email: info.bankuba@freemail.hu
Email analysis :
NOTE : info.bankuba@freemail.hu
NOTE : "www."@alice.it
NOTE : Received : from mzcstore091.ocn.ad.jp
NOTE : (mz-cb091p.ocn.ad.jp [118.23.178.17])
This is to notify you about our agreement with Bank of New York mellon to deliver to you without delay a Diplomatic Consignment Fund valued only $25.6 MILLION U.S DOLLARS which resulted from your outstanding contract Inheritance fund Following our agreement with Federal Reserve Bank, it must interest you to Know that the delivery documentation process has been legally finalized, so All you need to do now is for you to send me Your Full Names and Your Physical Delivery Address
including Your Direct Telephone Numbers for easy communication.
Be rest assured that upon the receipt of the above information from you as requested our Diplomatic Agent will use his diplomatic immunity to move the Consignment Fund straight to your doorstep immediately, Once again, bear in mind that every aspect of the delivery has been taken care of so there is nothing holding the Consignment Fund here now.
Best regards in anticipating hearing from you.
Dr. Jude Allen
Head Director, U.S. Diplomatic Base
Email: info.bankuba@freemail.hu
Email analysis :
NOTE : info.bankuba@freemail.hu
NOTE : "www."@alice.it
NOTE : Received : from mzcstore091.ocn.ad.jp
NOTE : (mz-cb091p.ocn.ad.jp [118.23.178.17])
Friday, June 16, 2017
Re Urgent Attention:
EXXON MOBIL CEPU LTD Kabupaten Bojonegoro,Jawa Timur 62152, Indonesia Telephone: +(62)858 9101 0186 Fax Number: +(62)858 9101 0322 Email:jobs_exxonmobil@job4u.com Viridium Associates is the global leader in OIL/GAS staffing and recruitment providing our client ( EXXONMOBILCORPORATION) with permanent, temporary and project based solutions. Viridium Associates employs a team of 130 professionals globally with operations in Indonesia, Singapore, UK and in the U.S. (Texas and Florida).Viridium Associates has partnered with OIL/GAS industry leader EXXONMOBIL CEPU LIMITED CORPORATION that is looking for experience and qualify candidates for the job. Human Resources Manager of EXXONMOBIL CEPU LIMITED has found your experience and qualifications extremely useful for our requirements. If Interested, kindly send us your updated resume to; (jobs_exxonmobil@job4u.com). With the below details. Your Present Monthly Salary in USD:- Your Preferred Monthly salary in USD:- Total Years Of Experience:- Years Of Experience in Oil & Gas Companies:- Availability:- Current Location:- Most Recent Position Held: Best Regards, Daniel Hadi RECRUITMENT COORDINATOR
Email analysis :
NOTE : jobs_exxonmobil@job4u.com
NOTE : www@space.ocn.ne.jp
NOTE : Received : from User (p546209-ipngn200505osakachuo.osaka.ocn.ne.jp [222.147.164.209])
Email analysis :
NOTE : jobs_exxonmobil@job4u.com
NOTE : www@space.ocn.ne.jp
NOTE : Received : from User (p546209-ipngn200505osakachuo.osaka.ocn.ne.jp [222.147.164.209])
Tuesday, June 13, 2017
Dearest One.
I am contacting you today with full confidence that you respond me with the same spirit that I have contacted you which shall be beneficial to both of us at last. I have some personal discussion that I want to pass to you directly. Can you please respond me so that I will unfold that? Hope to hear from you soonest.
Yours sincerely,
Fatimata Haifa.
Email analysis :
NOTE : fatimatahaifa20@yahoo.co.jp
NOTE : fatimahaifa35@yahoo.co.jp
NOTE : 98.137.67.206
Yours sincerely,
Fatimata Haifa.
Email analysis :
NOTE : fatimatahaifa20@yahoo.co.jp
NOTE : fatimahaifa35@yahoo.co.jp
NOTE : 98.137.67.206
You be receiving $5000 dollars daily
Payment Notification
This message is from our Transfer Head Office in Benin Republic. We are instructed to pay you $5.5 Million dollars which you will be receiving $5000 daily. We will be directing $5000 daily to Our Agent Office in your location where you will go and pickup the $5000. Forward your current address as stated below to enable us link the payment to our agents in your location.
Once you forward your current address as stated below, we will start releasing $5000 to you daily. Send your Full Names______ Address______ Country_____Tel_____Occupation_____Sex______Age_____ Forward the stated address to this email
Waiting to hear from you
Mr. Charles Dowling
Payment Director
Tel:+229-638
772-34
Email analysis :
NOTE : akinwumikolaa@gmail.com
NOTE : moneygramheadoffice@zoho.com
NOTE : Received : from [41.86.238.51]
NOTE : by webmail.numericable.fr with http webmail;
This message is from our Transfer Head Office in Benin Republic. We are instructed to pay you $5.5 Million dollars which you will be receiving $5000 daily. We will be directing $5000 daily to Our Agent Office in your location where you will go and pickup the $5000. Forward your current address as stated below to enable us link the payment to our agents in your location.
Once you forward your current address as stated below, we will start releasing $5000 to you daily. Send your Full Names______ Address______ Country_____Tel_____Occupation_____Sex______Age_____ Forward the stated address to this email
Waiting to hear from you
Mr. Charles Dowling
Payment Director
Tel:+229-638
772-34
Email analysis :
NOTE : akinwumikolaa@gmail.com
NOTE : moneygramheadoffice@zoho.com
NOTE : Received : from [41.86.238.51]
NOTE : by webmail.numericable.fr with http webmail;
Friday, June 9, 2017
Mrs. Nancy Viola
Attention Beneficiary Email ID,
I am Mrs. Nancy Viola.The Homemaker that wins Mega Millions jackpot of US$169 millions at New York Lottery office in January 30th 2016 and to avoid fraudlent notice, see my interview by visit link bellow:
www.dailymail.co.uk/news/article-3668744/Wife-wins-169million-Mega-Millions-jackpot-husband-buys-wrong-ticket.html :.
We just started international charitable donation campaign as we will be give a donation sum of Nine Million six Hundred Thousand United States Dollars each to improve the life of three Lucky individual from any part of worldwide. And your Name and email address was submitted to us by the Google internet management teams as a webmail User and your name is among those listed to receive the donation payment sum of US$9.6 Million through the help of Exchange State Bank Corporation Headquarter in 3992 E Chandler St,Carsonville, Michigan 48419 United States of America According to arrangement we sign: Dr. Dave Kirkbride, The Executive Vice President of Exchange State Bank Corporation Headquarter here in United States of America will contact you as soon as your draft check worth US$9.6 Million is ready to enable them send you the payment through bank to bank wire transfer to any of your bank account information you may provide to them. Therefore, contact the bank management Executive Vice President yourself with below information before 24hours today to enable quick releasing the donation payment to you because bank is always engage with many customers bank busineses.
Contact Person: Dr. Dave Kirkbride.
The Executive Vice President
Exchange State Bank Corporation Headquarter
Phone:..... +1 810 936 5964
Mobile: ....+1 810 515-7689
Email:.. kirkbride.dave1@gmail.com
Email:.. kirkbride.dave1@yahoo.com
Dr. Dave Kirkbride also always receive text message at +1 (810)936 5964 for bank business only. You can text him anytime about your donation payment because too many fraud use email address. So you must make sure you contact Dr. Dave Kirkbride direct once you read this mail message for more information because the donation US$9.6 Million sign in your name now is 100% genuine with due process of law, and it is well free from all illegal activities which you have the lawful right to claim your donation fund as soon as possible. And If you are receiving this notification for the first time, the ( US$9.6 Million ) can only be paid to you upon the receipt of DONATION CODE: [ NANCY+2017/GIFT/TWO+W ] to the bank Executive Vice President.
Congratulations & Happy Celebrations in Advance,
Best Regard.
Mrs. Nancy Viola
Homemaker wins Mega Millions jackpot.
https://www.youtube.com/watch?v=O4-_Gi1JS5E :.
Email analysis :
NOTE : kirkbride.dave1@gmail.com
NOTE : "mrs."@tenor.ocn.ne.jp
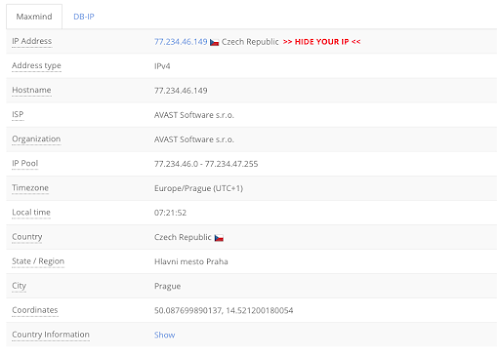
NOTE : X-Originating-Ip : [77.234.46.139]
NOTE : 77.234.46.0
I am Mrs. Nancy Viola.The Homemaker that wins Mega Millions jackpot of US$169 millions at New York Lottery office in January 30th 2016 and to avoid fraudlent notice, see my interview by visit link bellow:
www.dailymail.co.uk/news/article-3668744/Wife-wins-169million-Mega-Millions-jackpot-husband-buys-wrong-ticket.html :.
We just started international charitable donation campaign as we will be give a donation sum of Nine Million six Hundred Thousand United States Dollars each to improve the life of three Lucky individual from any part of worldwide. And your Name and email address was submitted to us by the Google internet management teams as a webmail User and your name is among those listed to receive the donation payment sum of US$9.6 Million through the help of Exchange State Bank Corporation Headquarter in 3992 E Chandler St,Carsonville, Michigan 48419 United States of America According to arrangement we sign: Dr. Dave Kirkbride, The Executive Vice President of Exchange State Bank Corporation Headquarter here in United States of America will contact you as soon as your draft check worth US$9.6 Million is ready to enable them send you the payment through bank to bank wire transfer to any of your bank account information you may provide to them. Therefore, contact the bank management Executive Vice President yourself with below information before 24hours today to enable quick releasing the donation payment to you because bank is always engage with many customers bank busineses.
Contact Person: Dr. Dave Kirkbride.
The Executive Vice President
Exchange State Bank Corporation Headquarter
Phone:..... +1 810 936 5964
Mobile: ....+1 810 515-7689
Email:.. kirkbride.dave1@gmail.com
Email:.. kirkbride.dave1@yahoo.com
Dr. Dave Kirkbride also always receive text message at +1 (810)936 5964 for bank business only. You can text him anytime about your donation payment because too many fraud use email address. So you must make sure you contact Dr. Dave Kirkbride direct once you read this mail message for more information because the donation US$9.6 Million sign in your name now is 100% genuine with due process of law, and it is well free from all illegal activities which you have the lawful right to claim your donation fund as soon as possible. And If you are receiving this notification for the first time, the ( US$9.6 Million ) can only be paid to you upon the receipt of DONATION CODE: [ NANCY+2017/GIFT/TWO+W ] to the bank Executive Vice President.
Congratulations & Happy Celebrations in Advance,
Best Regard.
Mrs. Nancy Viola
Homemaker wins Mega Millions jackpot.
https://www.youtube.com/watch?v=O4-_Gi1JS5E :.
Email analysis :
NOTE : kirkbride.dave1@gmail.com
NOTE : "mrs."@tenor.ocn.ne.jp
NOTE : X-Originating-Ip : [77.234.46.139]
NOTE : 77.234.46.0
Thursday, June 8, 2017
URGENT ATTENTION REQUIRED
Hello Friend.
You maybe surprise receiving such message from me, and being skeptical to reply. But I want to tell you to be free to respond. I am giving you my assurance and protection towards the deal I’m about to offer you which at the end we shall be more than happy.
My name is Caldwell William (Bill), born in Columbus, Georgia, USA. I was Commanding General of United States Army North, also known as the Fifth Army, served as the Commander of NATO Training Mission – Afghanistan, and simultaneously as the Commander of Combined Security Transition Command – Afghanistan and Iraq. While I was on duty, a lot happened which I cannot explained further because it was a tragedy.
While on duty, we also discovered a lot of things within my squad. I had in my possession Gold’s and physical Cash which were deposited in one of the security vault here, but safety of it is not guaranteed that is reason why I need your assistance to move it as soon as possible we can reach an agreement. I was planning to move it down to China for safety and for security purposes but it is not easier for I been on duty and handle that at same time.
That is reason why I am contacting you at this point of time, I need your help and if we reached an agreement I will authorize you with the proper documentations giving to me and security codes to retrieve what I had in the vault with the security company here in Iraq to move it down to you. If possible converting to the gold’s to Cash and have it secured also invest in your country on my behalf. But we have to reach an agreement and sign proper documents before this can be execute.
Note. This required 100% trust because you will be rewarded accordingly to the agreement. I need your feedback, and then we can proceed further to achieve our goals.
Thanks for your cooperation and understanding.
Yours Sincere
Caldwell William (Bill).
Email analysis :
NOTE : arodriguez@sinafocal.gov.py
NOTE : caldwilliam929@gmail.com
NOTE : X-Originating-Ip : [150.5.5.1]
You maybe surprise receiving such message from me, and being skeptical to reply. But I want to tell you to be free to respond. I am giving you my assurance and protection towards the deal I’m about to offer you which at the end we shall be more than happy.
My name is Caldwell William (Bill), born in Columbus, Georgia, USA. I was Commanding General of United States Army North, also known as the Fifth Army, served as the Commander of NATO Training Mission – Afghanistan, and simultaneously as the Commander of Combined Security Transition Command – Afghanistan and Iraq. While I was on duty, a lot happened which I cannot explained further because it was a tragedy.
While on duty, we also discovered a lot of things within my squad. I had in my possession Gold’s and physical Cash which were deposited in one of the security vault here, but safety of it is not guaranteed that is reason why I need your assistance to move it as soon as possible we can reach an agreement. I was planning to move it down to China for safety and for security purposes but it is not easier for I been on duty and handle that at same time.
That is reason why I am contacting you at this point of time, I need your help and if we reached an agreement I will authorize you with the proper documentations giving to me and security codes to retrieve what I had in the vault with the security company here in Iraq to move it down to you. If possible converting to the gold’s to Cash and have it secured also invest in your country on my behalf. But we have to reach an agreement and sign proper documents before this can be execute.
Note. This required 100% trust because you will be rewarded accordingly to the agreement. I need your feedback, and then we can proceed further to achieve our goals.
Thanks for your cooperation and understanding.
Yours Sincere
Caldwell William (Bill).
Email analysis :
NOTE : arodriguez@sinafocal.gov.py
NOTE : caldwilliam929@gmail.com
NOTE : X-Originating-Ip : [150.5.5.1]
Thursday, June 1, 2017
Рiԁ:382663110 (Apple Phishing)
myApple
Apple
Hello *@*,
We have unfortunately been unable to review some information in your Profile. To confirm your details Continue and SignOn.
Continue and Sign On
With our respects,
Apple Team
You're receiving this email from us because this address was entered to sign at apple.com. Having trouble? Let us know here.
© Copyright 2017 Apple.com
Email analysis :
NOTE : info@appleacres.co.uk
NOTE : Received : from smalldisk10 (13.65.207.162)
NOTE : by msx-van.nhc.local (192.168.101.10)
NOTE : Received : from MSX-VAN.nhc.local (192.168.101.10)
NOTE : by MSX-VAN.nhc.local (192.168.101.10)
NOTE : Received : from mail01.nhcweb.com (mail.nhcweb.com. [207.194.62.167])
Phishing analysis :
CLICK : Continue and Sign on
OPEN : http://charishospice.com/joy.php?*
REDIRECT : http://www.apple.com-logind52ac2j8rcgbjgpakeohtcy23rnbdx1vqw9o0w97rdamd89d67.saopaulonanet.com.br/apple/unitedstatesapple/*
SCREENSHOT :
Apple
Hello *@*,
We have unfortunately been unable to review some information in your Profile. To confirm your details Continue and SignOn.
Continue and Sign On
With our respects,
Apple Team
You're receiving this email from us because this address was entered to sign at apple.com. Having trouble? Let us know here.
© Copyright 2017 Apple.com
Email analysis :
NOTE : info@appleacres.co.uk
NOTE : Received : from smalldisk10 (13.65.207.162)
NOTE : by msx-van.nhc.local (192.168.101.10)
NOTE : Received : from MSX-VAN.nhc.local (192.168.101.10)
NOTE : by MSX-VAN.nhc.local (192.168.101.10)
NOTE : Received : from mail01.nhcweb.com (mail.nhcweb.com. [207.194.62.167])
Phishing analysis :
CLICK : Continue and Sign on
OPEN : http://charishospice.com/joy.php?*
REDIRECT : http://www.apple.com-logind52ac2j8rcgbjgpakeohtcy23rnbdx1vqw9o0w97rdamd89d67.saopaulonanet.com.br/apple/unitedstatesapple/*
SCREENSHOT :
Wednesday, May 31, 2017
Finance! (Loan Scam)
UNSECURED BUSINESS/PERSONAL LOAN BY LOAN CAPITAL FINANCE
- NO COLLATERAL
- MINIMUM DOCUMENTATION
- BUSINESS LOAN UP TO FIVE(5) MILLION US DOLLARS
CONTACT US TODAY VIA EMAIL: clfin77@foxmail.com
Email analysis :
NOTE : clfin77@foxmail.com
NOTE : angela.nava@zipaquira.gov.co
NOTE : Received : from correo.zipaquira.gov.co ([179.60.243.20])
NOTE : correo.zipaquira.gov.co
CONCLUSION :
The mail server of the colombian government has been used to relay this scam.
About Zipaquira :
Zipaquirá (Spanish pronunciation: [sipakiˈɾa]) is a municipality and city of Colombia in the department of Cundinamarca. Its neighboring municipalities are Tausa and Cogua to the north; Nemocón, Gachancipá and Sopó to the east; Cajicá and Tabio to the south; and Subachoque and Pacho to the west. Its seat of municipal government is 49 kilometers from Santa Fe de Bogotá. It is part of the Greater Bogotá Metropolitan Area, and is the capital of the province. It is also the headquarters of the diocese of the same name and that includes much of the Department of Cundinamarca, extending to the centre of Bogotá, the region of Rionegro, the Ubaté Valley, and the region of Guavio.
- NO COLLATERAL
- MINIMUM DOCUMENTATION
- BUSINESS LOAN UP TO FIVE(5) MILLION US DOLLARS
CONTACT US TODAY VIA EMAIL: clfin77@foxmail.com
Email analysis :
NOTE : clfin77@foxmail.com
NOTE : angela.nava@zipaquira.gov.co
NOTE : Received : from correo.zipaquira.gov.co ([179.60.243.20])
NOTE : correo.zipaquira.gov.co
CONCLUSION :
The mail server of the colombian government has been used to relay this scam.
About Zipaquira :
Zipaquirá (Spanish pronunciation: [sipakiˈɾa]) is a municipality and city of Colombia in the department of Cundinamarca. Its neighboring municipalities are Tausa and Cogua to the north; Nemocón, Gachancipá and Sopó to the east; Cajicá and Tabio to the south; and Subachoque and Pacho to the west. Its seat of municipal government is 49 kilometers from Santa Fe de Bogotá. It is part of the Greater Bogotá Metropolitan Area, and is the capital of the province. It is also the headquarters of the diocese of the same name and that includes much of the Department of Cundinamarca, extending to the centre of Bogotá, the region of Rionegro, the Ubaté Valley, and the region of Guavio.
Tuesday, May 30, 2017
Urgent Attention!! (Scam)
Good Day,
How are u doing today ? Apologies! I am a military woman ,seeking your kind assistance to move the sum of ($4.7.M USD) to you, as far as i can be assured that my money will be safe in your care until i complete my service here in Iraq and come over next month.
This is legitimate, and there is no danger involved. I need your full details to enable us proceed, such as : your Full Name, Full Address, Direct Mobile Number via hesterleigh.annz@gmail.com
Regards ,
Sgt. Leigh .A. Hester
Email analysis :
NOTE : Urgent Attention!!
NOTE : ovia.david2@aol.com
NOTE : hesterleigh.annz@gmail.com
NOTE : X-Aol-Ip : 197.210.227.124
How are u doing today ? Apologies! I am a military woman ,seeking your kind assistance to move the sum of ($4.7.M USD) to you, as far as i can be assured that my money will be safe in your care until i complete my service here in Iraq and come over next month.
This is legitimate, and there is no danger involved. I need your full details to enable us proceed, such as : your Full Name, Full Address, Direct Mobile Number via hesterleigh.annz@gmail.com
Regards ,
Sgt. Leigh .A. Hester
Email analysis :
NOTE : Urgent Attention!!
NOTE : ovia.david2@aol.com
NOTE : hesterleigh.annz@gmail.com
NOTE : X-Aol-Ip : 197.210.227.124
Dear Lucky Winner, (Lottery Scam)
APEC LOTTERY PROMO
Ref Number: NLUS/910/16454
Batch Number: VC/32/ID1141
Dear Lucky Winner,
We are happy to announce to you that your email address have won $2,000,000.00 (Two Million US Dollars). You were selected among the 10(Ten) lucky winners during the internet ballot draw of the APEC LOTTERY PROMO.
You are advised to contact the claim department immediately with the below information for the release of your prize money.:
Mr Lawrence Markins (Claim Agent)
Tel: +1-323-999-9775
Fax: +1-8176281183
Email: apeclototerpromo@consultant.com
International prize Department
CONGRATULATIONS!!!
Yours faithfully,
Mrs. Alice schieble
Online Coordinator.
Email analysis :
NOTE : rebeccaschieble8@yahoo.com
NOTE : apeclototerpromo@consultant.com
NOTE : Received : from sonic.gate.mail.ne1.yahoo.com
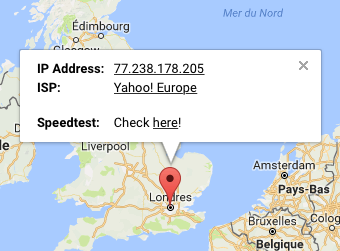
NOTE : client-ip=77.238.178.205;
Ref Number: NLUS/910/16454
Batch Number: VC/32/ID1141
Dear Lucky Winner,
We are happy to announce to you that your email address have won $2,000,000.00 (Two Million US Dollars). You were selected among the 10(Ten) lucky winners during the internet ballot draw of the APEC LOTTERY PROMO.
You are advised to contact the claim department immediately with the below information for the release of your prize money.:
Mr Lawrence Markins (Claim Agent)
Tel: +1-323-999-9775
Fax: +1-8176281183
Email: apeclototerpromo@consultant.com
International prize Department
CONGRATULATIONS!!!
Yours faithfully,
Mrs. Alice schieble
Online Coordinator.
Email analysis :
NOTE : rebeccaschieble8@yahoo.com
NOTE : apeclototerpromo@consultant.com
NOTE : Received : from sonic.gate.mail.ne1.yahoo.com
NOTE : client-ip=77.238.178.205;
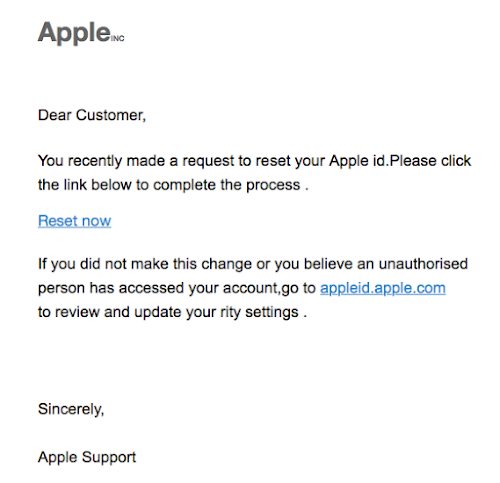
You recently made a request to reset your Apple id (Apple Phishing)
AppleINC
Dear Customer,
You recently made a request to reset your Apple id.Please click the link below to complete the process .
Reset now
If you did not make this change or you believe an unauthorised person has accessed your account,go to appleid.apple.com
to review and update your rity settings .
Sincerely,
Apple Support
Phishing screenshot :
Email analysis :
NOTE : paypal@service.fr
NOTE : Received : from lfsharedfs.FARMINDUSTRIA.LOCAL
NOTE : (extranet.farmindustria.com.pe [200.10.71.170])
Phishing analysis :
CLICK : http://amedamr06.webstarterz.com/apple.id.com
REDIRECT : http://93.182.172.19/Apple/Login.php?sslchannel=true&sessionid=*
SCREENSHOT :
Your Apple ID has been locked ! (Apple Phishing)
Validate your account information.
Dear iTunes Customer,
This is an automatic message sent by our security system to let you know that you have 48 hours to confirm your account information.
To validate your account information associated with your Apple ID, please
Visit the My Apple ID website
and sign in with your Apple ID and password. This will help protect your account in the future. This process does not take more than 3 minutes.
We apologise for any inconvenience caused.
Your sincerely,
Apple Security Department
TM and copyright 2017 Apple Inc. 1 Infinite Loop, MS 83-DM, Cupertino, CA 95014.
All Rights Reserved / Keep Informed / Privacy Policy / My Apple ID
Phishing screenshot :
Email analysis :
NOTE : noreply@email.apple.co.jp
NOTE : Received : from SERVER1 ([124.248.205.5])
Phishing analysis :
Click : Visit the My Apple ID website
OPEN : http://107.173.193.7/~eqjaeahu/index2.html
SCREENSHOT :
REDIRECT : http://107.173.193.7/~eqjaeahu/New1/*/suspended.php
SCREENSHOT :
CLICK : Confirm My Account
REDIRECT : http://107.173.193.7/~eqjaeahu/New1/*/personal.php
SCREENSHOT :
Dear iTunes Customer,
This is an automatic message sent by our security system to let you know that you have 48 hours to confirm your account information.
To validate your account information associated with your Apple ID, please
Visit the My Apple ID website
and sign in with your Apple ID and password. This will help protect your account in the future. This process does not take more than 3 minutes.
We apologise for any inconvenience caused.
Your sincerely,
Apple Security Department
TM and copyright 2017 Apple Inc. 1 Infinite Loop, MS 83-DM, Cupertino, CA 95014.
All Rights Reserved / Keep Informed / Privacy Policy / My Apple ID
Phishing screenshot :
Email analysis :
NOTE : noreply@email.apple.co.jp
NOTE : Received : from SERVER1 ([124.248.205.5])
Phishing analysis :
Click : Visit the My Apple ID website
OPEN : http://107.173.193.7/~eqjaeahu/index2.html
SCREENSHOT :
REDIRECT : http://107.173.193.7/~eqjaeahu/New1/*/suspended.php
SCREENSHOT :
CLICK : Confirm My Account
REDIRECT : http://107.173.193.7/~eqjaeahu/New1/*/personal.php
SCREENSHOT :
Tuesday, May 23, 2017
Confirme your account ! (PayPal Phishing)
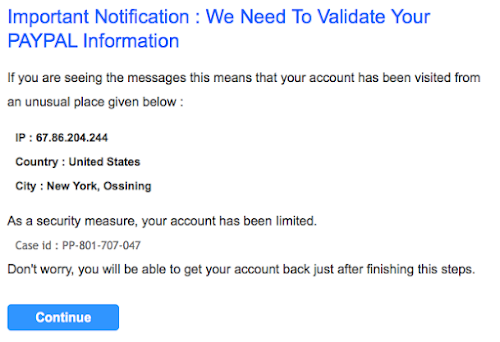
Important Notification : We Need To Validate Your ΡΑΥΡΑL Information
If you are seeing the messages this means that your account has been visited from an unusual place given below :
IP : 67.86.204.244
Country : United States
City : New York, Ossining
As a security measure, your account has been Iimited.
Case id : PP-801-707-047
Don't worry, you will be able to get your account back just after finishing this steps.
Continue
Email analysis :NOTE :
NOTE : Received : from d793.dinaserver.com (d793.dinaserver.com. [82.98.157.143])
NOTE : firstsunmallorca@d793.dinaserver.com
NOTE : X-Mailer : PHPMailer (phpmailer.sourceforge.net) [version ]
NOTE : firstsunmallorca@d793.dinaserver.com designates 82.98.157.143 as permitted sender)
Phishing screenshot :
Phishing analysis :
CLICK : Continue
OPEN : https://dhartiagro.net/aspnet_client/system_web/4_0_30319/HTTPS/Myaccount/home/new/Update
REDIRECT : https://dhartiagro.net/aspnet_client/system_web/4_0_30319/HTTPS/Myaccount/home/new/Update/myaccount/signin/
NOTE : VALIDATE FORM
REDIRECT : https://dhartiagro.net/aspnet_client/system_web/4_0_30319/HTTPS/Myaccount/home/new/Update/myaccount/settings/?verify_account=session=NL&*&dispatch=*
SCREENSHOT :
If you are seeing the messages this means that your account has been visited from an unusual place given below :
IP : 67.86.204.244
Country : United States
City : New York, Ossining
As a security measure, your account has been Iimited.
Case id : PP-801-707-047
Don't worry, you will be able to get your account back just after finishing this steps.
Continue
Email analysis :NOTE :
NOTE : Received : from d793.dinaserver.com (d793.dinaserver.com. [82.98.157.143])
NOTE : firstsunmallorca@d793.dinaserver.com
NOTE : X-Mailer : PHPMailer (phpmailer.sourceforge.net) [version ]
NOTE : firstsunmallorca@d793.dinaserver.com designates 82.98.157.143 as permitted sender)
Phishing screenshot :
Phishing analysis :
CLICK : Continue
OPEN : https://dhartiagro.net/aspnet_client/system_web/4_0_30319/HTTPS/Myaccount/home/new/Update
REDIRECT : https://dhartiagro.net/aspnet_client/system_web/4_0_30319/HTTPS/Myaccount/home/new/Update/myaccount/signin/
NOTE : VALIDATE FORM
REDIRECT : https://dhartiagro.net/aspnet_client/system_web/4_0_30319/HTTPS/Myaccount/home/new/Update/myaccount/settings/?verify_account=session=NL&*&dispatch=*
SCREENSHOT :
PayPal Phishing
PayPal
Informations concernant votre compte:
Dans le cadre de nos mesures de sécurité, Nous vérifions régulièrement l'activité de l'écran PayPal. Nous avons demandé des informations à vous pour la raison suivante:
Notre système a détecté des charges inhabituelles à une carte de crédit liée à votre compte PayPal.
Numéro de Référence: PP-259-187-991
C'est le dernier rappel pour vous connecter à PayPal, le plus tôt possible. Une fois que vous serez connecter. PayPal vous fournira des mesures pour rétablir l'accès à votre compte.
une fois connecté, suivez les étapes pour activer votre compte . Nous vous remercions de votre compréhension pendant que nous travaillons à assurer la sécurité compte.
Cliquer ici pour vérifier votre compte
Nous vous remercions de votre grande attention à cette question. S’il vous plaît comprenez que c'est une mesure de sécurité destinée à vous protéger ainsi que votre compte. Nous nous excusons pour tout inconvénient..
Département de revue des comptes PayPal
Copyright © 2017 PayPal. Tous droits réservés.
PayPal (Europe) S.à r.l. & Cie, S.C.A. Société en Commandite par
Actions Siège social : 5ème étage 22-24 Boulevard Royal L-2449,
Luxembourg RCS Luxembourg B 118 349
Email PayPal n° PP059
Protégez votre compte
Assurez-vous de ne jamais donner votre mot de passe pour les sites Web frauduleux.
Toute sécurité d'accès au site PayPal ou à votre compte, ouvrez une fenêtre de navigateur Web (Internet Explorer ou Netscape) et tapez dans la page de connexion de PayPal (http://paypal.fr/) afin de vous assurer que vous êtes sur le véritable PayPal Site.
Pour plus d'informations sur la protection contre la fraude, s’il vous plaît consulter nos conseils de sécurité
Protégez votre mot de passe
Vous ne devriez jamais donner votre mot de passe PayPal à personne.
--
This email was Virus checked by Astaro Security Gateway. http://www.sophos.com
Email analysis :
NOTE : Paypal@contact.ca
NOTE : Received : from [200.107.238.35] (port=2757 helo=User) by mx1.shary.com.sa
NOTE : client-ip=94.77.230.169;
Phishing screenshot :
Phishing analysis :
CLICK : Cliquer ici pour vérifier votre compte
OPEN : http://mir-pchelovoda.ru/components/com_acepolls/views/poll/tmpl/Notifications-service-demande-compte-ca.php
REDIRECT : http://www.sunshinetravel.az/js/tinymce/plugins/autoresize/ooo412312aaaa/Notifications-compte-Canada-quebec-verified-moi-information.ca/comfirmetions-service-information-compte-demande.ca/
SCREENSHOT :
CLICK : CONNEXION
RESULT : BAD PASSWORD...
REDIRECT : http://www.sunshinetravel.az/js/tinymce/plugins/autoresize/ooo412312aaaa/Notifications-compte-Canada-quebec-verified-moi-information.ca/comfirmetions-service-information-compte-demande.ca/error.php
The website sunshinetravel was used to store this PayPal phishing :
Thursday, May 18, 2017
Congratulations! You've won 」2,000,000! (Scam leak)
Your E-mail/Mobile Number has won £2,000,000 GBP in the Coca-Cola Promo,
To claim go to www.moboccolagify.com , click CLAIM enter Ref#: CC74117Q
Email analysis :
NOTE : ash0611jnag@gmail.com
NOTE : Received : from User (unknown [109.236.88.198])
NOTE : (Authenticated sender: admin@demo.pop-it.fr)
NOTE : by mail1.demo.pop-it.fr
Scam analysis :
CLICK : http://www.moboccolagify.com/
REDIRECTED : http://www.moboccolagify.com/cgi-sys/suspendedpage.cgi
RESULT : The scam was removed.
www.moboccolagify.com analysis :
Domain Name: moboccolagify.com
Registry Domain ID: 2099820320_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: https://www.namesilo.com/
Updated Date: 2017-05-11
Creation Date: 2017-02-22
Registrar Registration Expiration Date: 2018-02-22
Registrar: NameSilo, LLC
Registrar IANA ID: 1479
Registrar Abuse Contact Email: abuse@namesilo.com
Registrar Abuse Contact Phone: +1.4805240066
Reseller: QHOSTER.COM
Status: clientTransferProhibited
Registrant Name: Catherine Wosoh
Registrant Street: Bow Cottage, Robin Hood Ln, Wrightington
Registrant City: Appley Bridge
Registrant State/Province: Wigan
Registrant Postal Code: WN6 9QG
Registrant Country: GB
Registrant Phone: +44.02033897270
Registrant Email: xavierjapa147@gmail.com
Admin Name: Catherine Wosoh
Admin Street: Bow Cottage, Robin Hood Ln, Wrightington
Admin City: Appley Bridge
Admin State/Province: Wigan
Admin Postal Code: WN6 9QG
Admin Country: GB
Admin Phone: +44.02033897270
Admin Email: xavierjapa147@gmail.com
Registry Tech ID:
Tech Name: Catherine Wosoh
Tech Organization:
Tech Street: Bow Cottage, Robin Hood Ln, Wrightington
Tech City: Appley Bridge
Tech State/Province: Wigan
Tech Postal Code: WN6 9QG
Tech Country: GB
Tech Phone: +44.02033897270
Tech Email: xavierjapa147@gmail.com
Name Server: NS1.QHOSTER.NET
Name Server: NS2.QHOSTER.NET
Name Server: NS3.QHOSTER.NET
Name Server: NS4.QHOSTER.NET
xavierjapa147@gmail.com analysis :
xavierjapa147@gmail.com
Name Marianne Dillon
Address 4988 WORTH ST
City MILLINGTON
State MICHIGAN
Country US United States
Phone +1.9893251951
Fax +1.8017659400
List of domains registred by xavierjapa147@gmail.com :
newteamonli.com :
Registrant Name: MARIANNE DILLON
Registrant Organization:
Registrant Street: 4988 WORTH ST
Registrant City: MILLINGTON
Registrant State/Province: MICHIGAN
Registrant Postal Code: 48746
Registrant Country: US
Registrant Phone: +1.9893251951
Registrant Email: XAVIERJAPA147@GMAIL.COM
moboccolaltd.com :
Out
leekansoliccitor.com
Name: samuel buchman
Organization: buchman Inc
Mailing Address: 12927 288th St, Lindstrom 55045 US
Phone: +1.9706730990
Email:xavierjapa147@Gmail.com
Conclusion : Too much leakage to send a scam with no content...
To claim go to www.moboccolagify.com , click CLAIM enter Ref#: CC74117Q
Email analysis :
NOTE : ash0611jnag@gmail.com
NOTE : Received : from User (unknown [109.236.88.198])
NOTE : (Authenticated sender: admin@demo.pop-it.fr)
NOTE : by mail1.demo.pop-it.fr
Scam analysis :
CLICK : http://www.moboccolagify.com/
REDIRECTED : http://www.moboccolagify.com/cgi-sys/suspendedpage.cgi
RESULT : The scam was removed.
www.moboccolagify.com analysis :
Domain Name: moboccolagify.com
Registry Domain ID: 2099820320_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: https://www.namesilo.com/
Updated Date: 2017-05-11
Creation Date: 2017-02-22
Registrar Registration Expiration Date: 2018-02-22
Registrar: NameSilo, LLC
Registrar IANA ID: 1479
Registrar Abuse Contact Email: abuse@namesilo.com
Registrar Abuse Contact Phone: +1.4805240066
Reseller: QHOSTER.COM
Status: clientTransferProhibited
Registrant Name: Catherine Wosoh
Registrant Street: Bow Cottage, Robin Hood Ln, Wrightington
Registrant City: Appley Bridge
Registrant State/Province: Wigan
Registrant Postal Code: WN6 9QG
Registrant Country: GB
Registrant Phone: +44.02033897270
Registrant Email: xavierjapa147@gmail.com
Admin Name: Catherine Wosoh
Admin Street: Bow Cottage, Robin Hood Ln, Wrightington
Admin City: Appley Bridge
Admin State/Province: Wigan
Admin Postal Code: WN6 9QG
Admin Country: GB
Admin Phone: +44.02033897270
Admin Email: xavierjapa147@gmail.com
Registry Tech ID:
Tech Name: Catherine Wosoh
Tech Organization:
Tech Street: Bow Cottage, Robin Hood Ln, Wrightington
Tech City: Appley Bridge
Tech State/Province: Wigan
Tech Postal Code: WN6 9QG
Tech Country: GB
Tech Phone: +44.02033897270
Tech Email: xavierjapa147@gmail.com
Name Server: NS1.QHOSTER.NET
Name Server: NS2.QHOSTER.NET
Name Server: NS3.QHOSTER.NET
Name Server: NS4.QHOSTER.NET
xavierjapa147@gmail.com analysis :
xavierjapa147@gmail.com
Name Marianne Dillon
Address 4988 WORTH ST
City MILLINGTON
State MICHIGAN
Country US United States
Phone +1.9893251951
Fax +1.8017659400
List of domains registred by xavierjapa147@gmail.com :
newteamonli.com :
Registrant Name: MARIANNE DILLON
Registrant Organization:
Registrant Street: 4988 WORTH ST
Registrant City: MILLINGTON
Registrant State/Province: MICHIGAN
Registrant Postal Code: 48746
Registrant Country: US
Registrant Phone: +1.9893251951
Registrant Email: XAVIERJAPA147@GMAIL.COM
moboccolaltd.com :
Out
leekansoliccitor.com
Name: samuel buchman
Organization: buchman Inc
Mailing Address: 12927 288th St, Lindstrom 55045 US
Phone: +1.9706730990
Email:xavierjapa147@Gmail.com
Conclusion : Too much leakage to send a scam with no content...
lovelykumah
Hello Dear am well pleased to contact you here, i am female, please i will like you to mail me back so that i will send you my pictures and to discuss the confidential issue i have to discuss with you. please reply me back for more details,miss lovely my email(lovelykumah11@hotmail.com)
Email analysis :
NOTE : lovelykumah11@hotmail.com
NOTE : Received : from sonic.gate.mail.ne1.yahoo.com
NOTE : by sonic325.consmr.mail.gq1.yahoo.com
NOTE : client-ip=98.137.67.179;
Please recheck your delivery address USPS parcel 632063287
Hello,
This is to confirm that your item has been shipped at Tue, 16 May 2017 10:49:00 -0700.
You can print the shipment label by clicking on the link.
information.doc
With sincere thanks.
Shanae Stovall - USPS Support Clerk.
Email analysis :
NOTE : fisou75@viajeseci.es
NOTE : Received : from viajeseci.es (unknown [222.222.219.154])
Phishing analysis :
CLICK : information.doc
OPEN : http://be-tiger.com/wp-content/sg.php
RESULT : Phishing was removed
This is to confirm that your item has been shipped at Tue, 16 May 2017 10:49:00 -0700.
You can print the shipment label by clicking on the link.
information.doc
With sincere thanks.
Shanae Stovall - USPS Support Clerk.
Email analysis :
NOTE : fisou75@viajeseci.es
NOTE : Received : from viajeseci.es (unknown [222.222.219.154])
Phishing analysis :
CLICK : information.doc
OPEN : http://be-tiger.com/wp-content/sg.php
RESULT : Phishing was removed
Report-ID: *@* 21/04/2017 (Phishing attempt)
Dear Driver,
This is the automatic statement of the Parking Service.
Road cameras have recorded the limit exceeding of your vehicle. Therefore, you will have to pay the applicable fine.
--------------------------------------------------------------------------- ---
So as to successfully complete the payment, you will have to finalize the invoice on the official website.
Your Fine Invoice ID is VL05U
Please submit it here: pa rking-services.us
--------------------------------------------------------------------------- ---
Then, you will have all essential details to execute the payment.
You have one day to document the fine. Else, significant charges may apply.
Please do not reply to this message.
------
Kindest Regards,
Parking Service
Email analysis :
NOTE : oybi6@wwpinc.com
NOTE : User-Agent : Mozilla/5.0 (Windows; U; Windows NT 5.1;
NOTE : en-GB; rv:1.8.0.14) Gecko/20071210 Thunderbird/1.5.0.14
NOTE : client-ip=202.55.69.138;
Phishing analysis :
CLICK : pa rking-services.us
OPEN : http://www.wik.be/backend/modules/settings/c056bc1304.html
RESULT : Phishing attempt
This is the automatic statement of the Parking Service.
Road cameras have recorded the limit exceeding of your vehicle. Therefore, you will have to pay the applicable fine.
--------------------------------------------------------------------------- ---
So as to successfully complete the payment, you will have to finalize the invoice on the official website.
Your Fine Invoice ID is VL05U
Please submit it here: pa rking-services.us
--------------------------------------------------------------------------- ---
Then, you will have all essential details to execute the payment.
You have one day to document the fine. Else, significant charges may apply.
Please do not reply to this message.
------
Kindest Regards,
Parking Service
Email analysis :
NOTE : oybi6@wwpinc.com
NOTE : User-Agent : Mozilla/5.0 (Windows; U; Windows NT 5.1;
NOTE : en-GB; rv:1.8.0.14) Gecko/20071210 Thunderbird/1.5.0.14
NOTE : client-ip=202.55.69.138;
Phishing analysis :
CLICK : pa rking-services.us
OPEN : http://www.wik.be/backend/modules/settings/c056bc1304.html
RESULT : Phishing attempt
Saturday, May 13, 2017
Notification de la dette (Phishing Banque de France)
Vous avez les dettes.
Vous pouvez télécharger plus d'informations sur ce LIEN
Si vous avez des questions vous pouvez appeler les numéros indiqués sur notre site
Merci d'avance,
Sacha Pierre
Spécialiste responsable de la clientèle
BANQUE DE FRANCE
Tél.: 0 811 901 801
31 rue Croix des Petits-Champs
75049 PARIS cedex 01
Email analysis :
NOTE : banque@banque-france.fr
NOTE : gvbev@fulda170.server4you.de
NOTE : client-ip=62.75.219.171;
NOTE : LINK : http://ascomnotizie.confcommerciocremona.it/edizioni/2013/Settembre/mp3/config/page5.html
NOTE : Download a virus "facture.zip" then redirect to the Banque de France.
NOTE : https://www.banque-france.fr/
The title of the phishing can also be "L\\\'avis de Banque de France sur facturation" with a different content :
Bonjour!
Vous avez reçu une nouvelle facture
La facture à payer peut être consultée sur ce LIEN
Si vous avez des questions vous pouvez nous appeler.
Veuillez d\\\'agréer les salutations distinguées,
Patrice Salmon
Spécialiste responsable de la clientèle
BANQUE DE FRANCE
Tél.: 0 811 901 801
31 rue Croix des Petits-Champs
75049 PARIS cedex 01
Email analysis :
NOTE : infos@banque-france.fr
NOTE : www-data@vs186078.vserver.de
NOTE : Received : from www-data by vs186078.vserver.de
NOTE : LINK : http://deko-studio.ru/templates/jblank/html/com_contact/categories/content2.html
NOTE : Phishing is unresponsive.
The title of the phishing can also be "Notification du paiement" with a different content :
Cher client!
Nous vous informons sur la dette existante
Vous pouvez télécharger plus d'informations sur ce LIEN
Si vous avez des questions vous pouvez nous appeler.
Meilleurs vœux,
Aubin Pascal
Spécialiste responsable de la clientèle
BANQUE DE FRANCE
Email analysis :
NOTE : apache@vps11617909.123-vps.co.uk
NOTE : Received : by vps11617909.123-vps.co.uk
NOTE : LINK : http://rolkatravel.ru/includes/Archive/content2.html
NOTE : Redirect to another phishing then Banque de France
The title of the phishing can also be "Rappel de dette" with a different content :
Vous avez reçu la facture de la société Banque de France
Vous pouvez télécharger plus d'informations sur ce LIEN
Si vous avez des questions vous pouvez nous appeler
Meilleurs vœux!
Samy Bouchet
Spécialiste principal responsable de la clientèle
BANQUE DE FRANCE
Email analysis :
NOTE : commercial@banque-france.fr
NOTE : webmaster@missdress.ru
NOTE : Received : from www-data by webs3.ru
NOTE : LINK : http://купить-дом-в-испании.рф/wp-admin/css/colors/blue/content2.html
NOTE : Phishing was removed.
The title of the phishing can also be "Vous avez les dettes" with a different content :
Vous avez les dettes.
Vous pouvez télécharger plus d'informations sur ce LIEN
Si vous avez des questions vous pouvez appeler les numéros indiqués sur notre site
Merci d'avance!
Salomon Legros
Chef
BANQUE DE FRANCE
Tél.: 0 811 901 801
31 rue Croix des Petits-Champs
75049 PARIS cedex 01
Email analysis :
NOTE : contact@banque-france.fr
NOTE : Received : by vps11617909.123-vps.co.uk
NOTE : LINK : http://smartfitness.com.ua/wp-content/themes/fitnesstheme/fontawesome/css/page6.html
NOTE : Redirect to the Banque de France.
Conclusion
Numerous phishing were removed, but I found one still active and I downloaded a virus called facture.zip
Open facture.zip
AegisLab : Troj.Script.Agent!c
Antiy-AVL : Trojan/Generic.ASVCS3S.3FA
Arcabit : JS:Trojan.Cryxos.725
Avast : Other:Malware-gen [Trj]
AVG : Script/Generic_c.NOE
Avira (no cloud) : HEUR/Suspar.Gen
BitDefender : JS:Trojan.Cryxos.725
Comodo : Heur.Dual.Extensions
Cyren : JS/Nemucod.EB1!Eldorado
DrWeb : Trojan.DownLoader24.57175
Emsisoft : JS:Trojan.Cryxos.725 (B)
ESET-NOD32 : JS/TrojanDownloader.Nemucod.CXN
F-Prot : JS/Nemucod.EB1!Eldorado
F-Secure : JS:Trojan.Cryxos.725
Fortinet : JS/Nemucod.CXN!tr
GData : JS:Trojan.Cryxos.725
Ikarus : Trojan-Downloader.JS.Nemucod
K7AntiVirus : Trojan ( 004dfe6d1 )
K7GW : Trojan ( 004dfe6d1 )
Kaspersky : HEUR:Trojan.Script.Agent.gen
Microsoft : TrojanDownloader:JS/Nemucod
eScan : JS:Trojan.Cryxos.725
Rising : Downloader.Nemucod!8.34 (cloud:EJcAeQsE3jG)
Sophos : Mal/DrodZp-A
Symantec : Trojan.Gen.NPE
Tencent : Js.Trojan-downloader.Nemucod.Gbr
TrendMicro-HouseCall : Suspicious_GEN.F47V0510
ZoneAlarm by Check Point : HEUR:Trojan.Script.Agent.gen
Source code of the virus :
https://pastebin.com/raw/VaBZWADT
Vous pouvez télécharger plus d'informations sur ce LIEN
Si vous avez des questions vous pouvez appeler les numéros indiqués sur notre site
Merci d'avance,
Sacha Pierre
Spécialiste responsable de la clientèle
BANQUE DE FRANCE
Tél.: 0 811 901 801
31 rue Croix des Petits-Champs
75049 PARIS cedex 01
Email analysis :
NOTE : banque@banque-france.fr
NOTE : gvbev@fulda170.server4you.de
NOTE : client-ip=62.75.219.171;
NOTE : LINK : http://ascomnotizie.confcommerciocremona.it/edizioni/2013/Settembre/mp3/config/page5.html
NOTE : Download a virus "facture.zip" then redirect to the Banque de France.
NOTE : https://www.banque-france.fr/
The title of the phishing can also be "L\\\'avis de Banque de France sur facturation" with a different content :
Bonjour!
Vous avez reçu une nouvelle facture
La facture à payer peut être consultée sur ce LIEN
Si vous avez des questions vous pouvez nous appeler.
Veuillez d\\\'agréer les salutations distinguées,
Patrice Salmon
Spécialiste responsable de la clientèle
BANQUE DE FRANCE
Tél.: 0 811 901 801
31 rue Croix des Petits-Champs
75049 PARIS cedex 01
Email analysis :
NOTE : infos@banque-france.fr
NOTE : www-data@vs186078.vserver.de
NOTE : Received : from www-data by vs186078.vserver.de
NOTE : LINK : http://deko-studio.ru/templates/jblank/html/com_contact/categories/content2.html
NOTE : Phishing is unresponsive.
The title of the phishing can also be "Notification du paiement" with a different content :
Cher client!
Nous vous informons sur la dette existante
Vous pouvez télécharger plus d'informations sur ce LIEN
Si vous avez des questions vous pouvez nous appeler.
Meilleurs vœux,
Aubin Pascal
Spécialiste responsable de la clientèle
BANQUE DE FRANCE
Email analysis :
NOTE : apache@vps11617909.123-vps.co.uk
NOTE : Received : by vps11617909.123-vps.co.uk
NOTE : LINK : http://rolkatravel.ru/includes/Archive/content2.html
NOTE : Redirect to another phishing then Banque de France
The title of the phishing can also be "Rappel de dette" with a different content :
Vous avez reçu la facture de la société Banque de France
Vous pouvez télécharger plus d'informations sur ce LIEN
Si vous avez des questions vous pouvez nous appeler
Meilleurs vœux!
Samy Bouchet
Spécialiste principal responsable de la clientèle
BANQUE DE FRANCE
Email analysis :
NOTE : commercial@banque-france.fr
NOTE : webmaster@missdress.ru
NOTE : Received : from www-data by webs3.ru
NOTE : LINK : http://купить-дом-в-испании.рф/wp-admin/css/colors/blue/content2.html
NOTE : Phishing was removed.
The title of the phishing can also be "Vous avez les dettes" with a different content :
Vous avez les dettes.
Vous pouvez télécharger plus d'informations sur ce LIEN
Si vous avez des questions vous pouvez appeler les numéros indiqués sur notre site
Merci d'avance!
Salomon Legros
Chef
BANQUE DE FRANCE
Tél.: 0 811 901 801
31 rue Croix des Petits-Champs
75049 PARIS cedex 01
Email analysis :
NOTE : contact@banque-france.fr
NOTE : Received : by vps11617909.123-vps.co.uk
NOTE : LINK : http://smartfitness.com.ua/wp-content/themes/fitnesstheme/fontawesome/css/page6.html
NOTE : Redirect to the Banque de France.
Conclusion
Numerous phishing were removed, but I found one still active and I downloaded a virus called facture.zip
Open facture.zip
AegisLab : Troj.Script.Agent!c
Antiy-AVL : Trojan/Generic.ASVCS3S.3FA
Arcabit : JS:Trojan.Cryxos.725
Avast : Other:Malware-gen [Trj]
AVG : Script/Generic_c.NOE
Avira (no cloud) : HEUR/Suspar.Gen
BitDefender : JS:Trojan.Cryxos.725
Comodo : Heur.Dual.Extensions
Cyren : JS/Nemucod.EB1!Eldorado
DrWeb : Trojan.DownLoader24.57175
Emsisoft : JS:Trojan.Cryxos.725 (B)
ESET-NOD32 : JS/TrojanDownloader.Nemucod.CXN
F-Prot : JS/Nemucod.EB1!Eldorado
F-Secure : JS:Trojan.Cryxos.725
Fortinet : JS/Nemucod.CXN!tr
GData : JS:Trojan.Cryxos.725
Ikarus : Trojan-Downloader.JS.Nemucod
K7AntiVirus : Trojan ( 004dfe6d1 )
K7GW : Trojan ( 004dfe6d1 )
Kaspersky : HEUR:Trojan.Script.Agent.gen
Microsoft : TrojanDownloader:JS/Nemucod
eScan : JS:Trojan.Cryxos.725
Rising : Downloader.Nemucod!8.34 (cloud:EJcAeQsE3jG)
Sophos : Mal/DrodZp-A
Symantec : Trojan.Gen.NPE
Tencent : Js.Trojan-downloader.Nemucod.Gbr
TrendMicro-HouseCall : Suspicious_GEN.F47V0510
ZoneAlarm by Check Point : HEUR:Trojan.Script.Agent.gen
Source code of the virus :
https://pastebin.com/raw/VaBZWADT
Need mnoey?Eaarn 50.000 per moonth.
###MAKE MONEY ON1|NE###
===EAARN 50.000 PER MONNTH===
1.You need 0nly email to regisster
2.Fluly automattic sytsem!NOTHING TO DO...
3.@bs0lutely passvie inc0me
http://www.wildstonesolution.com/wp-content/plugins/wordpress-seo/vendor/xrstf/composer-php52/lib/5bc10d79da.html
The title of the scam can also be : Need mooney?Eran 50.000 per moonth. with a different content
###MAAKE MONNEY ONLLNE###
===EAARN 50.000 PER MONTH===
1.You neeed only emmail to reg|$ter
2.Fuliy automatic ssytem!NOTHING TO DO...
3.Absolute1y passive lnc0me
http://www.ieee-papers.com/wp-content/themes/twentyseventeen/2159b211e2.html
Email analysis :
NOTE : mhurdsj@excite.it
NOTE : gfgrimaud@tjb-barre.com
NOTE : 202.150.50.14
NOTE : 113.186.177.167
Phishing analysis :
CLICK : http://www.wildstonesolution.com/wp-content/plugins/wordpress-seo/vendor/xrstf/composer-php52/lib/5bc10d79da.html
Result : Redirect to Google, the phishing was removed...
CLICK : http://www.ieee-papers.com/wp-content/themes/twentyseventeen/2159b211e2.html
RESULT : Redirect to Google, the phishing was removed
NOTE : Two wordpress websites were compromised to do this phishing.
===EAARN 50.000 PER MONNTH===
1.You need 0nly email to regisster
2.Fluly automattic sytsem!NOTHING TO DO...
3.@bs0lutely passvie inc0me
http://www.wildstonesolution.com/wp-content/plugins/wordpress-seo/vendor/xrstf/composer-php52/lib/5bc10d79da.html
The title of the scam can also be : Need mooney?Eran 50.000 per moonth. with a different content
###MAAKE MONNEY ONLLNE###
===EAARN 50.000 PER MONTH===
1.You neeed only emmail to reg|$ter
2.Fuliy automatic ssytem!NOTHING TO DO...
3.Absolute1y passive lnc0me
http://www.ieee-papers.com/wp-content/themes/twentyseventeen/2159b211e2.html
Email analysis :
NOTE : mhurdsj@excite.it
NOTE : gfgrimaud@tjb-barre.com
NOTE : 202.150.50.14
NOTE : 113.186.177.167
Phishing analysis :
CLICK : http://www.wildstonesolution.com/wp-content/plugins/wordpress-seo/vendor/xrstf/composer-php52/lib/5bc10d79da.html
Result : Redirect to Google, the phishing was removed...
CLICK : http://www.ieee-papers.com/wp-content/themes/twentyseventeen/2159b211e2.html
RESULT : Redirect to Google, the phishing was removed
NOTE : Two wordpress websites were compromised to do this phishing.
Friday, May 12, 2017
Update Your Account Information Now !! (PayPal Phishing Attempt)
PayPal
Warning : Account Issue !
Your account is limited untill you update your information because some one requested acces to your account, here is the infos :
Location : Russia
IP adress : 176.96.80.140
Navigator : Mozilla Firefox 48.0 on Windows
The restore the access to your account please click on the link below :
Update My Account
This is an email sent automatically. Please do not reply to this letter, because the e-mail address is only configured to send but not to receive e-mails.
Copyright © 2017 All rights reserved.
Phishing screenshot :
Email analysis :
NOTE : morag@g-p-t.co.uk
NOTE : Received : from RDT.spectra.local (unknown [80.229.37.167])
NOTE : by cust-smtp-auth2.fasthosts.net.uk (Postfix)
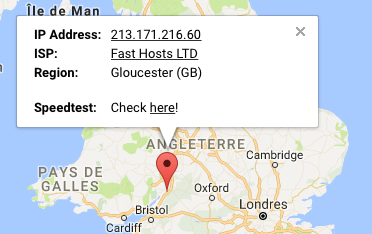
NOTE : client-ip=213.171.216.60;
Phishing analysis :
CLICK : Update my Account
OPEN : http://sadagatismayilova.com/update-your-account-information-now/myaccount/
SCREENSHOT :
NOTE : Phishing was removed.
Warning : Account Issue !
Your account is limited untill you update your information because some one requested acces to your account, here is the infos :
Location : Russia
IP adress : 176.96.80.140
Navigator : Mozilla Firefox 48.0 on Windows
The restore the access to your account please click on the link below :
Update My Account
This is an email sent automatically. Please do not reply to this letter, because the e-mail address is only configured to send but not to receive e-mails.
Copyright © 2017 All rights reserved.
Phishing screenshot :
Email analysis :
NOTE : morag@g-p-t.co.uk
NOTE : Received : from RDT.spectra.local (unknown [80.229.37.167])
NOTE : by cust-smtp-auth2.fasthosts.net.uk (Postfix)
NOTE : client-ip=213.171.216.60;
Phishing analysis :
CLICK : Update my Account
OPEN : http://sadagatismayilova.com/update-your-account-information-now/myaccount/
SCREENSHOT :
NOTE : Phishing was removed.
(no subject)
السلام عليكم انا مدام نادية محمد اريد منك ان تساعدنى لاننى لدى مشروع اريد ان اعرضه اليك لذا ارجو منك التواصل معى على هذا الايميل
nadia55mohammed@gmail.com
Translation :
Salam alaikum. I am Madame Nadia Mohamed. I want you to help me because I have a project I want to introduce to you so I hope you can contact me on this email
Nadia55mohammed@gmail.com
Email analysis :
NOTE : nadia55mohammed@gmail.com
NOTE : ib@caucasus.net
NOTE : Received : from webmail.caucasus.net
NOTE : (unknown [213.157.215.234])
NOTE : by mail.caucasus.net (Postfix)
nadia55mohammed@gmail.com
Translation :
Salam alaikum. I am Madame Nadia Mohamed. I want you to help me because I have a project I want to introduce to you so I hope you can contact me on this email
Nadia55mohammed@gmail.com
Email analysis :
NOTE : nadia55mohammed@gmail.com
NOTE : ib@caucasus.net
NOTE : Received : from webmail.caucasus.net
NOTE : (unknown [213.157.215.234])
NOTE : by mail.caucasus.net (Postfix)
Subscribe to:
Posts (Atom)