Bonjour,
Vous avez (1) nouveaux messages sur votre messagerie.
Consulter votre Messagerie en cliquant sur le lien ci-dessous :
(Consultezhici)
Nousivousiremercionsideivotreiconfiance.
Email analysis :
NOTE : info@societegenerale.fr
NOTE : Return-Path : < apache@admiral.anchor.net.au >
NOTE : X-Remote : 202.4.239.210 (admiral.anchor.net.au)
NOTE : Mime-Version : 1.0
NOTE : Received : from admiral.anchor.net.au (admiral.anchor.net.au [202.4.239.210])
NOTE : Received : by admiral.anchor.net.au (Postfix, from userid 48)
NOTE : Vous avez un nouveau message
Phishing screenshot :
Phishing analysis :
CLICK : (Consultezhici)
OPEN : starrdental.com/html/websms/index.htm
RESULT : Unresponsive
RESULT : Phishing attempt.
Friday, October 13, 2017
Tuesday, August 15, 2017
FWD:TR:RE (Phishing attempt Société Générale)
SOCIETE GENERALE
Cher client,
Le département technique de Société Générale procède à une mise à jour de logiciel programmée de façon à améliorer la qualité des services bancaires.
Nous vous demandons avec bienveillance de cliquer sur le lien ci-dessous et de confirmer vos détails bancaires.
https://www.societegenerale.fr/customercare/banque/confprocedure.asp
Nous nous excusons pour tout désagrément et vous remercions pour votre coopération.
© Société Générale 2017
Phishing screenshot :
Email analysis :
NOTE : natalia1@telus.net
NOTE : Natalia Toroshenko
NOTE : X-Mailer : Zimbra 8.6.0_GA_1211 (zclient/8.6.0_GA_1211)
NOTE : X-Originating-Ip : [160.163.161.144]
Phishing analysis :
CLICK : https://www.societegenerale.fr/customercare/banque/confprocedure.asp
OPEN : http://www.cfa-sport.fr/wp-includes/Text/theme/
REDIRECT : http://www.anti-laser.at/wp-includes/css/theme/
NOTE : Not Found 404 / You are connected from a remote location.
RESULT : Phishing attempt.
Cher client,
Le département technique de Société Générale procède à une mise à jour de logiciel programmée de façon à améliorer la qualité des services bancaires.
Nous vous demandons avec bienveillance de cliquer sur le lien ci-dessous et de confirmer vos détails bancaires.
https://www.societegenerale.fr/customercare/banque/confprocedure.asp
Nous nous excusons pour tout désagrément et vous remercions pour votre coopération.
© Société Générale 2017
Phishing screenshot :
Email analysis :
NOTE : natalia1@telus.net
NOTE : Natalia Toroshenko
NOTE : X-Mailer : Zimbra 8.6.0_GA_1211 (zclient/8.6.0_GA_1211)
NOTE : X-Originating-Ip : [160.163.161.144]
Phishing analysis :
CLICK : https://www.societegenerale.fr/customercare/banque/confprocedure.asp
OPEN : http://www.cfa-sport.fr/wp-includes/Text/theme/
REDIRECT : http://www.anti-laser.at/wp-includes/css/theme/
NOTE : Not Found 404 / You are connected from a remote location.
RESULT : Phishing attempt.
Monday, July 31, 2017
Votre-Paiement-En ligne (Phishing attempt)
Bonjour,
Afin de prévenir l'utilisation frauduleuse des cartes bancaires Internet,
Votre Service Générale, est dotée d'un dispositif de controle des paiements.
Ce service est entierement gratuit Notre Systeme a detecte que vous n'avez pas active -Pass-Service-sécurite
Service sécurite
Banque-Générale
Nous vous remercions de votre Confiance.
Cordielement
Email analysis :
NOTE : INFO@news.promovacances.com
NOTE : Received : by footcenter.fr (Postfix, from userid 33)
NOTE : Received : from footcenter.fr ([165.227.79.193])
NOTE : X-Php-Originating-Script : 0:nel.php
NOTE : Message-Id : < *.*@footcenter.fr >
NOTE : Votre-Paiement-En ligne
Phishing screenshot :
Phishing analysis :
CLICK : Service sécurite
OPEN : http://sirlwad.gear.host/s52.html
SCREENSHOT :
RESULT : Phishing attempt.
Information about this phishing
SCRIPT : nel.php
HACKED RELAY : footcenter.fr
OPEN REDIRECT : sirlwad.gear.host
SPOOFED EMAIL : INFO@news.promovacances.com
PHISHING : Société Générale
Afin de prévenir l'utilisation frauduleuse des cartes bancaires Internet,
Votre Service Générale, est dotée d'un dispositif de controle des paiements.
Ce service est entierement gratuit Notre Systeme a detecte que vous n'avez pas active -Pass-Service-sécurite
Service sécurite
Banque-Générale
Nous vous remercions de votre Confiance.
Cordielement
Email analysis :
NOTE : INFO@news.promovacances.com
NOTE : Received : by footcenter.fr (Postfix, from userid 33)
NOTE : Received : from footcenter.fr ([165.227.79.193])
NOTE : X-Php-Originating-Script : 0:nel.php
NOTE : Message-Id : < *.*@footcenter.fr >
NOTE : Votre-Paiement-En ligne
Phishing screenshot :
Phishing analysis :
CLICK : Service sécurite
OPEN : http://sirlwad.gear.host/s52.html
SCREENSHOT :
RESULT : Phishing attempt.
Information about this phishing
SCRIPT : nel.php
HACKED RELAY : footcenter.fr
OPEN REDIRECT : sirlwad.gear.host
SPOOFED EMAIL : INFO@news.promovacances.com
PHISHING : Société Générale
Thursday, May 18, 2017
Please recheck your delivery address USPS parcel 632063287
Hello,
This is to confirm that your item has been shipped at Tue, 16 May 2017 10:49:00 -0700.
You can print the shipment label by clicking on the link.
information.doc
With sincere thanks.
Shanae Stovall - USPS Support Clerk.
Email analysis :
NOTE : fisou75@viajeseci.es
NOTE : Received : from viajeseci.es (unknown [222.222.219.154])
Phishing analysis :
CLICK : information.doc
OPEN : http://be-tiger.com/wp-content/sg.php
RESULT : Phishing was removed
This is to confirm that your item has been shipped at Tue, 16 May 2017 10:49:00 -0700.
You can print the shipment label by clicking on the link.
information.doc
With sincere thanks.
Shanae Stovall - USPS Support Clerk.
Email analysis :
NOTE : fisou75@viajeseci.es
NOTE : Received : from viajeseci.es (unknown [222.222.219.154])
Phishing analysis :
CLICK : information.doc
OPEN : http://be-tiger.com/wp-content/sg.php
RESULT : Phishing was removed
Friday, May 12, 2017
Update Your Account Information Now !! (PayPal Phishing Attempt)
PayPal
Warning : Account Issue !
Your account is limited untill you update your information because some one requested acces to your account, here is the infos :
Location : Russia
IP adress : 176.96.80.140
Navigator : Mozilla Firefox 48.0 on Windows
The restore the access to your account please click on the link below :
Update My Account
This is an email sent automatically. Please do not reply to this letter, because the e-mail address is only configured to send but not to receive e-mails.
Copyright © 2017 All rights reserved.
Phishing screenshot :
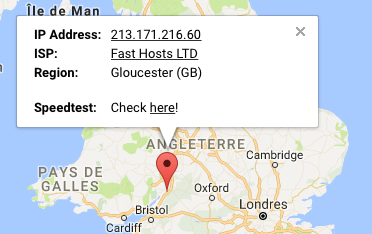
Email analysis :
NOTE : morag@g-p-t.co.uk
NOTE : Received : from RDT.spectra.local (unknown [80.229.37.167])
NOTE : by cust-smtp-auth2.fasthosts.net.uk (Postfix)
NOTE : client-ip=213.171.216.60;
Phishing analysis :
CLICK : Update my Account
OPEN : http://sadagatismayilova.com/update-your-account-information-now/myaccount/
SCREENSHOT :
NOTE : Phishing was removed.
Warning : Account Issue !
Your account is limited untill you update your information because some one requested acces to your account, here is the infos :
Location : Russia
IP adress : 176.96.80.140
Navigator : Mozilla Firefox 48.0 on Windows
The restore the access to your account please click on the link below :
Update My Account
This is an email sent automatically. Please do not reply to this letter, because the e-mail address is only configured to send but not to receive e-mails.
Copyright © 2017 All rights reserved.
Phishing screenshot :
Email analysis :
NOTE : morag@g-p-t.co.uk
NOTE : Received : from RDT.spectra.local (unknown [80.229.37.167])
NOTE : by cust-smtp-auth2.fasthosts.net.uk (Postfix)
NOTE : client-ip=213.171.216.60;
Phishing analysis :
CLICK : Update my Account
OPEN : http://sadagatismayilova.com/update-your-account-information-now/myaccount/
SCREENSHOT :
NOTE : Phishing was removed.
Monday, April 24, 2017
Banco Santander (Brasil) S.A. | Evite Bloqueio de sua conta (*) (Phishing Attempt)
Banco Santander S.A.
Prezado(a) Cliente,
Comunicamos que seus dados cadastrais encontram-se desatualizados em nosso sistema.Para que você possa desfrutar dos benefícios com comodidade e segurança, pedimos que você efetue a Atualização Cadastral de Segurança imposta pelo nosso sistema.
Este procedimento deve ser efetuado, evitando o bloqueio aos canais Santander tais como Telefone, Internet Banking e Caixas Eletrônicos.
Para evitar a suspensão automática desses serviços, habilite suas atualizações clicando no botão abaixo.
Este recurso só é ativado se você aceitar, e é atualizado a partir de servidores certificados..
Deseja confirmar suas definições de segurança?
Confirmar
Banco Santander (Brasil) S.A. CNPJ: 90.400.888/0001-42 Avenida Presidente Juscelino Kubitschek, 2041 e 2235 - Bloco A, Vila Olímpia, São Paulo/SP - CEP 04543-011
Screenshot of the phishing :
Email analysis :
NOTE : Received : by ip-160-153-226-153.ip.secureserver.net
NOTE : (Postfix, from userid 33)
NOTE : 160.153.226.184
NOTE : X-Mailer : Microsoft Office Outlook, Build 17.551210
NOTE : X-Mailer : iGMail [www.ig.com.br]
Phishing analysis :
CLICK : Confirmar
OPEN : http://ip-160-153-229-233.ip.secureserver.net/cadastro/*
RESULT : Phishing is unresponsive...
Prezado(a) Cliente,
Comunicamos que seus dados cadastrais encontram-se desatualizados em nosso sistema.Para que você possa desfrutar dos benefícios com comodidade e segurança, pedimos que você efetue a Atualização Cadastral de Segurança imposta pelo nosso sistema.
Este procedimento deve ser efetuado, evitando o bloqueio aos canais Santander tais como Telefone, Internet Banking e Caixas Eletrônicos.
Para evitar a suspensão automática desses serviços, habilite suas atualizações clicando no botão abaixo.
Este recurso só é ativado se você aceitar, e é atualizado a partir de servidores certificados..
Deseja confirmar suas definições de segurança?
Confirmar
Banco Santander (Brasil) S.A. CNPJ: 90.400.888/0001-42 Avenida Presidente Juscelino Kubitschek, 2041 e 2235 - Bloco A, Vila Olímpia, São Paulo/SP - CEP 04543-011
Screenshot of the phishing :
Email analysis :
NOTE : Received : by ip-160-153-226-153.ip.secureserver.net
NOTE : (Postfix, from userid 33)
NOTE : 160.153.226.184
NOTE : X-Mailer : Microsoft Office Outlook, Build 17.551210
NOTE : X-Mailer : iGMail [www.ig.com.br]
Phishing analysis :
CLICK : Confirmar
OPEN : http://ip-160-153-229-233.ip.secureserver.net/cadastro/*
RESULT : Phishing is unresponsive...
Saturday, February 25, 2017
Your iTunes ID (Phishing attempt)
Update your account when you're ready.
We suspect that someone is trying to use your account. When you're ready, click the link below to update your account information. For your safety your account has been temporarily locked.
https://appleid.apple.com/IDMSWebAuth/login.html?appIdKey=fgd55eeklw56q96w qq64.
Case ID: 662498345
This link will expire after 24 hours.
Sincerely,
Apple Support
Get help online
Visit Apple Support to learn more about your product, download software updates, and much more.
Join the conversation
Find and share solutions with Apple users around the world.
copyright 2016 Apple Inc.
All Rights Reserved / Privacy Policy / Support / Give us feedback
On behalf of Apple Distribution International
Phishing screenshot :
Email analysis :
NOTE : no-reply@services-apple.com
NOTE : X-Php-Originating-Script : 33:01.php(4) : eval()'d code
NOTE : Received : by cptweb02 (Postfix, from userid 33)
NOTE : CPT WEBSERVER
NOTE : client-ip=77.95.37.80;
Phishing analysis :
CLICK : https://appleid.apple.com/IDMSWebAuth/login.html?appIdKey=fgd55eeklw56q96w qq64.
OPEN : Link wasn't activated...
RESULT : Phishing attempt.
We suspect that someone is trying to use your account. When you're ready, click the link below to update your account information. For your safety your account has been temporarily locked.
https://appleid.apple.com/IDMSWebAuth/login.html?appIdKey=fgd55eeklw56q96w qq64.
Case ID: 662498345
This link will expire after 24 hours.
Sincerely,
Apple Support
Get help online
Visit Apple Support to learn more about your product, download software updates, and much more.
Join the conversation
Find and share solutions with Apple users around the world.
copyright 2016 Apple Inc.
All Rights Reserved / Privacy Policy / Support / Give us feedback
On behalf of Apple Distribution International
Phishing screenshot :
Email analysis :
NOTE : no-reply@services-apple.com
NOTE : X-Php-Originating-Script : 33:01.php(4) : eval()'d code
NOTE : Received : by cptweb02 (Postfix, from userid 33)
NOTE : CPT WEBSERVER
NOTE : client-ip=77.95.37.80;
Phishing analysis :
CLICK : https://appleid.apple.com/IDMSWebAuth/login.html?appIdKey=fgd55eeklw56q96w qq64.
OPEN : Link wasn't activated...
RESULT : Phishing attempt.
Saturday, February 4, 2017
URGENT: Confirmation Of Your Online Banking. (JPMorgan Phishing attempt)
Dear Chase Online(SM) Customer,
As part of our commitment to help keep your account secure, we have detected an irregular activity on your account and we are placing a hold on your account for your protection. Please click on the following link and follow the instructions for proper verification.
CLICK HERE
NB: If this important message seems to be spam/junk please move to inbox to enable you click on the link above, We are here to assist you anytime. Your account security is our priority. Thank you for choosing Chase.
Sincerely,
Chase Fraud Department
Copyright © 2016 Chase Online. All rights reserved
JPMorgan Chase & Co.
Email analysis :
NOTE : info@onlinebanking.com
NOTE : bblazzard@lusd.k12.ca.us
NOTE : Received : from onlinebanking.com (unknown [68.65.134.234])
Phishing analysis :
CLICK : CLICK HERE
OPEN : http://mobwarsdoa.com/banking/chaseonline/Logon.php?LOB=RBGLogon&_pageLabel=page_logonform
As part of our commitment to help keep your account secure, we have detected an irregular activity on your account and we are placing a hold on your account for your protection. Please click on the following link and follow the instructions for proper verification.
CLICK HERE
NB: If this important message seems to be spam/junk please move to inbox to enable you click on the link above, We are here to assist you anytime. Your account security is our priority. Thank you for choosing Chase.
Sincerely,
Chase Fraud Department
Copyright © 2016 Chase Online. All rights reserved
JPMorgan Chase & Co.
Email analysis :
NOTE : info@onlinebanking.com
NOTE : bblazzard@lusd.k12.ca.us
NOTE : Received : from onlinebanking.com (unknown [68.65.134.234])
Phishing analysis :
CLICK : CLICK HERE
OPEN : http://mobwarsdoa.com/banking/chaseonline/Logon.php?LOB=RBGLogon&_pageLabel=page_logonform
Thursday, December 8, 2016
FW: FTC subpoena (Phishing attempt)
You've been subpoenaed by the FTC.
FTC Subpoena
Please get back to me about this.
Thank you
Richard Kent
Senior Accountant
richard@*.*
Phone: 441-216-2849
Fax: 441-216-5880
Email analysis :
NOTE : richard@*.*
NOTE : Received : from unknown (HELO IEOSOZAX) (117.247.121.182)
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; rv:24.0)
NOTE : Gecko/20100101 Thunderbird/24.2.0
NOTE : BSNL was used to relay this phishing.
Phishing analysis :
CLICK : FTC Subpoena
OPEN : http://benxethainguyen.vn/api/get.php?id=dGVzdEB0ZXN0LmNvbQ==
RESULT : 404, removed...
WHOIS : benxethainguyen.vn
benxethainguyen.vn whois :
TÊN MIỀN benxethainguyen.vn
Ngày đăng ký: 16-03-2012
Ngày hết hạn : 16-03-2017
Tên chủ thể đăng ký sử dụng :Ông Nguyễn Sự
Trạng thái : clientTransferProhibited
Quản lý tại Nhà đăng ký: Công ty TNHH Một thành viên Viễn thông Quốc tế FPT
Máy chủ DNS chuyển giao: + ns2008.nhanhoa.com.vn + ns2009.nhanhoa.com.vn
Registration date : 16-03-2012
Expiration date : 16-03-2017
Registrant : Ông Nguyễn Sự
Status : clientTransferProhibited
Current Registrar : Công ty TNHH Một thành viên Viễn thông Quốc tế FPT
DNS Server : + ns2008.nhanhoa.com.vn + ns2009.nhanhoa.com.vn
FTC Subpoena
Please get back to me about this.
Thank you
Richard Kent
Senior Accountant
richard@*.*
Phone: 441-216-2849
Fax: 441-216-5880
Email analysis :
NOTE : richard@*.*
NOTE : Received : from unknown (HELO IEOSOZAX) (117.247.121.182)
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; rv:24.0)
NOTE : Gecko/20100101 Thunderbird/24.2.0
NOTE : BSNL was used to relay this phishing.
Phishing analysis :
CLICK : FTC Subpoena
OPEN : http://benxethainguyen.vn/api/get.php?id=dGVzdEB0ZXN0LmNvbQ==
RESULT : 404, removed...
WHOIS : benxethainguyen.vn
benxethainguyen.vn whois :
TÊN MIỀN benxethainguyen.vn
Ngày đăng ký: 16-03-2012
Ngày hết hạn : 16-03-2017
Tên chủ thể đăng ký sử dụng :Ông Nguyễn Sự
Trạng thái : clientTransferProhibited
Quản lý tại Nhà đăng ký: Công ty TNHH Một thành viên Viễn thông Quốc tế FPT
Máy chủ DNS chuyển giao: + ns2008.nhanhoa.com.vn + ns2009.nhanhoa.com.vn
Registration date : 16-03-2012
Expiration date : 16-03-2017
Registrant : Ông Nguyễn Sự
Status : clientTransferProhibited
Current Registrar : Công ty TNHH Một thành viên Viễn thông Quốc tế FPT
DNS Server : + ns2008.nhanhoa.com.vn + ns2009.nhanhoa.com.vn
Friday, October 14, 2016
Your Netflix Membership has been suspended [#348963] (Phishing)
Validation failed
During a routine check of your account we have failed to validate the billing method we have on record for your account. To continue using the Netflix service you will need to update/verify your billing information.
CONTINUE >>
Please note that failure to complete the validation process will result in permanent suspension of your netflix membership.
We thank you for your understanding.
Netflix Billing Support
TWEET LIKE FORWARD
Preferences | Unsubscribe
Phishing analysis :
CLICK : CONTINUE >>
OPEN : http://newdata01.com/
RESULT : Phishing was removed
Email analysis :
NOTE : Return-Path:
NOTE : Received: from [146.20.110.156] (port=57419 helo=User)
NOTE : From: " Netflix"< no-reply@netflix.ssl.com>
NOTE : Subject: Your Netflix Membership has been suspended [#348963]
NOTE : MIME-Version: 1.0
NOTE : Content-Type: text/html;charset="Windows-1251"
NOTE : Content-Transfer-Encoding: 7bit
NOTE : X-AntiAbuse: Sender Address Domain - netflix.ssl.com
NOTE : X-Get-Message-Sender-Via: server-33:
NOTE : authenticated_id: pro/only user confirmed/virtual account not confirmed
NOTE : X-Authenticated-Sender: server-33: pro
NOTE : X-Remote: 162.242.219.144 ()
During a routine check of your account we have failed to validate the billing method we have on record for your account. To continue using the Netflix service you will need to update/verify your billing information.
CONTINUE >>
Please note that failure to complete the validation process will result in permanent suspension of your netflix membership.
We thank you for your understanding.
Netflix Billing Support
TWEET LIKE FORWARD
Preferences | Unsubscribe
Phishing analysis :
CLICK : CONTINUE >>
OPEN : http://newdata01.com/
RESULT : Phishing was removed
Email analysis :
NOTE : Return-Path:
NOTE : Received: from [146.20.110.156] (port=57419 helo=User)
NOTE : From: " Netflix"< no-reply@netflix.ssl.com>
NOTE : Subject: Your Netflix Membership has been suspended [#348963]
NOTE : MIME-Version: 1.0
NOTE : Content-Type: text/html;charset="Windows-1251"
NOTE : Content-Transfer-Encoding: 7bit
NOTE : X-AntiAbuse: Sender Address Domain - netflix.ssl.com
NOTE : X-Get-Message-Sender-Via: server-33:
NOTE : authenticated_id: pro/only user confirmed/virtual account not confirmed
NOTE : X-Authenticated-Sender: server-33: pro
NOTE : X-Remote: 162.242.219.144 ()
Thursday, October 13, 2016
Aviso !!! (Phishing Attempt)
Aviso !!!
Nos dimos cuenta de que su cuenta de correo electrónico se ha casi exceder su límite. Y usted no puede enviar o recibir mensajes en cualquier momento a partir de ahora.
Haga clic en el enlace para iniciar la sesión y renovar su cuenta: http://ow.ly/JT19304XkK2
AVISO:
El no hacer login y renovar su cuenta de correo electrónico que será una incapacidad permanente.
Gracias,
cuenta de servicio
Phishing analysis :
CLICK : http://ow.ly/JT19304XkK2
SCREENSHOT :
NOTE : Phishing attempt...
Email analysis :
NOTE : Content-Type : text/plain; charset="iso-8859-1"
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < cgajardo@sence.cl >
NOTE : Return-Path : cgajardo@sence.cl
NOTE : account : cgajardo
NOTE : X-Originating-Ip : [120.146.244.171]
NOTE : Content-Transfer-Encoding : quoted-printable
NOTE : Received : from cipres.sence.local (osopanda.sence.cl. [163.247.55.173])
NOTE : Received : from ARAUCARIA.sence.local (192.9.200.57)
NOTE : by cipres.sence.local (192.9.200.55)
NOTE : Received-Spf : client-ip=163.247.55.173;
NOTE : Content-Description : Mail message body
NOTE : Aviso !!!
NOTE : sence.cl server with account cgajardo were used to relay this phishing...
Nos dimos cuenta de que su cuenta de correo electrónico se ha casi exceder su límite. Y usted no puede enviar o recibir mensajes en cualquier momento a partir de ahora.
Haga clic en el enlace para iniciar la sesión y renovar su cuenta: http://ow.ly/JT19304XkK2
AVISO:
El no hacer login y renovar su cuenta de correo electrónico que será una incapacidad permanente.
Gracias,
cuenta de servicio
Phishing analysis :
CLICK : http://ow.ly/JT19304XkK2
SCREENSHOT :
NOTE : Phishing attempt...
Email analysis :
NOTE : Content-Type : text/plain; charset="iso-8859-1"
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < cgajardo@sence.cl >
NOTE : Return-Path : cgajardo@sence.cl
NOTE : account : cgajardo
NOTE : X-Originating-Ip : [120.146.244.171]
NOTE : Content-Transfer-Encoding : quoted-printable
NOTE : Received : from cipres.sence.local (osopanda.sence.cl. [163.247.55.173])
NOTE : Received : from ARAUCARIA.sence.local (192.9.200.57)
NOTE : by cipres.sence.local (192.9.200.55)
NOTE : Received-Spf : client-ip=163.247.55.173;
NOTE : Content-Description : Mail message body
NOTE : Aviso !!!
NOTE : sence.cl server with account cgajardo were used to relay this phishing...
Compte Alerte! [Signature=664QT6]
BMO Banque de Montreal Canada
Cher (*@*),
Vous n'êtes plus autorisé à accéder à votre service en ligne.
Nous avons dû désactiver votre accès pour votre sécurité.
Cela a pu être le cas du fait d'un changement intervenu récemment dans votre adresse, ou parce que des informations incorrectes ont été fournies durant le processus d'enregistrement initial. Veuillez vérifier votre compte dans les 48 prochaines heures afin d'éviter une suspension complète de votre compte en ligne. À l'issue d'une vérification réussie de votre compte vous pourrez utiliser votre identifiant comme d'habitude.
Suivez cette page de vérification sécurisée afin de réaliser une authentification en ligne efficace:
https://www1.bmo.com/onlinebanking/cgi-bin/netbnx/NBmain?product=6
Nous prenons la sécurité de votre compte très au sérieux, et nous avons besoin de ces informations pour nous aider à empêcher des tiers d'accéder à votre compte.
Par contre, en ce qui concerne les comptes BMO bloqués, seule une utilisation responsable de votre compte BMO peut empêcher sa désactivation. La politique de BMO sur le déblocage de comptes semble dépendre de la fourniture de données précises, grâce auxquelles les opérateurs prennent une décision sur le compte. Les informations peuvent être mal interprétées, et les questions et réponses de sécurité peuvent être oubliées, il est donc plus pratique d'éviter ce genre de problème en utilisant votre compte de manière responsable.
%%%ID: 6640285754
Phishing analysis :
CLICK : https://www1.bmo.com/onlinebanking/cgi-bin/netbnx/NBmain?product=6
OPEN : http://www.marking-sb.hr/aget7/index.php
RESULT : Phishing is unresponsive...
Email analysis :
NOTE : X-Clientproxiedby : EMSERVER.CANNONKALLAR.local (10.1.1.3)
NOTE : To EMSERVER.CANNONKALLAR.local (10.1.1.3)
NOTE : Received : from [192.168.0.23] (75.151.23.97)
NOTE : by EMSERVER.CANNONKALLAR.local (10.1.1.3)
NOTE : Received : from mail.kallars.com (mail.kallars.com. [81.136.176.71])
Cher (*@*),
Vous n'êtes plus autorisé à accéder à votre service en ligne.
Nous avons dû désactiver votre accès pour votre sécurité.
Cela a pu être le cas du fait d'un changement intervenu récemment dans votre adresse, ou parce que des informations incorrectes ont été fournies durant le processus d'enregistrement initial. Veuillez vérifier votre compte dans les 48 prochaines heures afin d'éviter une suspension complète de votre compte en ligne. À l'issue d'une vérification réussie de votre compte vous pourrez utiliser votre identifiant comme d'habitude.
Suivez cette page de vérification sécurisée afin de réaliser une authentification en ligne efficace:
https://www1.bmo.com/onlinebanking/cgi-bin/netbnx/NBmain?product=6
Nous prenons la sécurité de votre compte très au sérieux, et nous avons besoin de ces informations pour nous aider à empêcher des tiers d'accéder à votre compte.
Par contre, en ce qui concerne les comptes BMO bloqués, seule une utilisation responsable de votre compte BMO peut empêcher sa désactivation. La politique de BMO sur le déblocage de comptes semble dépendre de la fourniture de données précises, grâce auxquelles les opérateurs prennent une décision sur le compte. Les informations peuvent être mal interprétées, et les questions et réponses de sécurité peuvent être oubliées, il est donc plus pratique d'éviter ce genre de problème en utilisant votre compte de manière responsable.
%%%ID: 6640285754
Phishing analysis :
CLICK : https://www1.bmo.com/onlinebanking/cgi-bin/netbnx/NBmain?product=6
OPEN : http://www.marking-sb.hr/aget7/index.php
RESULT : Phishing is unresponsive...
Email analysis :
NOTE : X-Clientproxiedby : EMSERVER.CANNONKALLAR.local (10.1.1.3)
NOTE : To EMSERVER.CANNONKALLAR.local (10.1.1.3)
NOTE : Received : from [192.168.0.23] (75.151.23.97)
NOTE : by EMSERVER.CANNONKALLAR.local (10.1.1.3)
NOTE : Received : from mail.kallars.com (mail.kallars.com. [81.136.176.71])
Monday, July 25, 2016
update your Apple ID (***@***) (Apple Phishing)
Dear ***,
you should verify your Apple ID (***@***) as soon as possible to reactivate your account.
Verify Now >
TM and copyright 2016 Apple Inc. Hollyhill Industrial Estate Hollyhill, Cork, Republic of Ireland.
All Rights Reserved / Keep Informed / Privacy Policy / My Apple ID
Email analysis :
NOTE : apple@apple.id.com
NOTE : X-Source-Args : lsphp5:/home/goodnerd/public_html/leafmailer.php
NOTE : Return-Path : < apple@apple.id.com >
NOTE : Mime-Version : 1.0
NOTE : X-Source-Dir : goodnerda.com:/public_html
NOTE : X-Mailer : Leaf PHPMailer 2.7 (leafmailer.pw)
NOTE : X-Authenticated-Sender : cphost6.veeblehosting.com: goodnerd
NOTE : X-Php-Script : www.goodnerda.com/leafmailer.php for 41.100.229.125
NOTE : update your Apple ID (***@***)
Phishing analysis :
CLICK : Verify Now >
OPEN : https://www.hpsusa.net/wp-content//apple.id/secure/login/verify/id/XR0ARZo5EF6yOEy0k8vdxlIhqVldR6Mq873DB5vxN8gf3Xxa7qINDvBrvjW/login/
NOTE : Phishing was removed...
Sunday, July 3, 2016
Lisez votre message! (Phishing Hello bank)
sur un seul site.
Votre actu des
Bonjours Cher(e) Client(e) ,
Un nouveau message est disponible sur votre messagerieo
Pour consulter, Veuiller cliquez sur le lien ce-dessous :
Accèdez à votre boite
Nous vous remercions de votre confiance.
Hello-Bankª
Ce courriel vous a été envoyé par un système automatique d'émission de messages. L'adresse d'émission n'est pas une adresse de courriel classique. Si vous écrivez à cette adresse, votre message ne sera pas pris en compte
Screenshot of the email :
Email analysis :
NOTE : servicehelloban@decathlon.fr
NOTE : www-data@decathlon.fr
NOTE : X-Php-Originating-Script : 0:noi.php
NOTE : Received : by decathlon.fr (Postfix, from userid 33)
NOTE : Received : from decathlon.fr ([139.59.145.95])
NOTE : Decathlon servers were used to relay this phishing.
Votre actu des
Bonjours Cher(e) Client(e) ,
Un nouveau message est disponible sur votre messagerieo
Pour consulter, Veuiller cliquez sur le lien ce-dessous :
Accèdez à votre boite
Nous vous remercions de votre confiance.
Hello-Bankª
Ce courriel vous a été envoyé par un système automatique d'émission de messages. L'adresse d'émission n'est pas une adresse de courriel classique. Si vous écrivez à cette adresse, votre message ne sera pas pris en compte
Screenshot of the email :
Email analysis :
NOTE : servicehelloban@decathlon.fr
NOTE : www-data@decathlon.fr
NOTE : X-Php-Originating-Script : 0:noi.php
NOTE : Received : by decathlon.fr (Postfix, from userid 33)
NOTE : Received : from decathlon.fr ([139.59.145.95])
NOTE : Decathlon servers were used to relay this phishing.
Sunday, June 5, 2016
Update Your Information Account !! (eBay Phishing attempt)
eBay
Account ID: 0073621101
We have reason to believe that your eBay account has been used fraudulently without your permission. In addition, any unauthorized activity, such as buying or selling, has been canceled and any associated fees have been credited to your account. Any listings that we removed are included toward the end of this email. We assure you that your financial information is securely stored on a server and cannot be seen by anyone.
To secure your eBay account, you need to:
1 - Login to your account.
2 - Verify the contact information.
3 - Update your payment informations and other stored information on your eBay account is correct.
For detailed instructions, please visit: www.ebɑy.com/help/account/securing-account-ID-0073621101.html
We appreciate your understanding and thank you for being part of our community.
Regards, eBay
Please don't reply to this message. It was sent from an address that doesn't accept incoming email.
Copyright © 2016.
Phishing analysis :
CLICK : www.ebɑy.com/help/account/securing-account-ID-0073621101.html
OPEN : https://www.secure-account-update-online.aloobein.ga/
REDIRECT : Phishing was removed...
Email analysis :
NOTE : Content-Type : text/html
NOTE : Mime-Version : 1.0
NOTE : X-Get-Message-Sender-Via : cpanel.hostnet.ge: authenticated_id: hostnet/only user confirmed/virtual account not confirmed
NOTE : Return-Path :
NOTE : X-Authenticated-Sender : cpanel.hostnet.ge: hostnet
NOTE : Received : from cpanel.hostnet.ge (cpanel.hostnet.ge. [212.72.155.189])
NOTE : Received : from hostnet by cpanel.hostnet.ge with local (Exim 4.87) (envelope-from < hostnet@cpanel.hostnet.ge >)
NOTE : Message-Id : < *@cpanel.hostnet.ge >
NOTE : smtp.mailfrom=hostnet@cpanel.hostnet.ge
NOTE : Update Your Information Account !!
Account ID: 0073621101
We have reason to believe that your eBay account has been used fraudulently without your permission. In addition, any unauthorized activity, such as buying or selling, has been canceled and any associated fees have been credited to your account. Any listings that we removed are included toward the end of this email. We assure you that your financial information is securely stored on a server and cannot be seen by anyone.
To secure your eBay account, you need to:
1 - Login to your account.
2 - Verify the contact information.
3 - Update your payment informations and other stored information on your eBay account is correct.
For detailed instructions, please visit: www.ebɑy.com/help/account/securing-account-ID-0073621101.html
We appreciate your understanding and thank you for being part of our community.
Regards, eBay
Please don't reply to this message. It was sent from an address that doesn't accept incoming email.
Copyright © 2016.
Phishing analysis :
CLICK : www.ebɑy.com/help/account/securing-account-ID-0073621101.html
OPEN : https://www.secure-account-update-online.aloobein.ga/
REDIRECT : Phishing was removed...
Email analysis :
NOTE : Content-Type : text/html
NOTE : Mime-Version : 1.0
NOTE : X-Get-Message-Sender-Via : cpanel.hostnet.ge: authenticated_id: hostnet/only user confirmed/virtual account not confirmed
NOTE : Return-Path :
NOTE : X-Authenticated-Sender : cpanel.hostnet.ge: hostnet
NOTE : Received : from cpanel.hostnet.ge (cpanel.hostnet.ge. [212.72.155.189])
NOTE : Received : from hostnet by cpanel.hostnet.ge with local (Exim 4.87) (envelope-from < hostnet@cpanel.hostnet.ge >)
NOTE : Message-Id : < *@cpanel.hostnet.ge >
NOTE : smtp.mailfrom=hostnet@cpanel.hostnet.ge
NOTE : Update Your Information Account !!
Phishing attempt on bitcointalk email addresses
Greetings,
We know that some of you have accounts on bitcointalk.org and we wanted to let you know that a phishing attempt was made on bitcointalk email addresses earlier today.
If you received an email with the subject Mtgox.Claim assessment process, delete it and do not click on the link it contains! This email did not come from Kraken, but was spoofed to look as though it came from our support email (support@kraken.com).
We do not know how the bitcointalk email addresses were obtained, however the bitcointalk database has been compromised in the past. You can be assured that this incident was not the result of any breach in Kraken’s database and your personal information with Kraken is safe.
Even if you did receive the email, you are safe so long as you do not click on the link (just delete the email and you will be fine). If you did click on the link and are concerned about it, please contact us at: support@kraken.com.
Stay safe,
The Kraken Team
We know that some of you have accounts on bitcointalk.org and we wanted to let you know that a phishing attempt was made on bitcointalk email addresses earlier today.
If you received an email with the subject Mtgox.Claim assessment process, delete it and do not click on the link it contains! This email did not come from Kraken, but was spoofed to look as though it came from our support email (support@kraken.com).
We do not know how the bitcointalk email addresses were obtained, however the bitcointalk database has been compromised in the past. You can be assured that this incident was not the result of any breach in Kraken’s database and your personal information with Kraken is safe.
Even if you did receive the email, you are safe so long as you do not click on the link (just delete the email and you will be fine). If you did click on the link and are concerned about it, please contact us at: support@kraken.com.
Stay safe,
The Kraken Team
Lisez votre messagew (Phishing Crédit Agricole) (Attempt)
Cher(e)dClient(e)dd
Lors de votre dérnier achats,vous avez été averti par un message vous informant de l'obligation d'adhérer à la
nouvelledréglementation conçernant la flabilité pour les achats pardC.Bdsur internet et de la mise en place d'un
arrêt pour vos futursdachats.
Or,nousfn'avons pas, cefjour,d'adhésionfdefvotrefpart et nousfsommes aufregret de vousdinformer que vous
pouvez plus utiliser votredcarte surfinternet
Adhésion;fFaitesfvotrefdemandefd'adhésionfenflignefenfcliquantfici
Cordialementggg
Copyright © 2016 Crédit Agricole
Copyright © 2016 A2 Hosting, All rights reserved.
You are receiving this email because you are an A2 Hosting Customer. If you don't wish to be on the Newsletter you can easily unsubscribe here or by controlling your contact options at My A2 Hosting.
Our mailing address is:
A2 Hosting
PO Box 2998
Ann Arbor, MI 48106
Add us to your address book
Quick Links
We're Hiring
My A2 Hosting
Open a Support Ticket
Affiliate Program - Earn $85!
Refer a Friend - Earn $50!
Review A2 Hosting!
Unsubscribe from this List Update Subscription and Notification Settings
Phishing analysis :
CLICK : Adhésion;fFaitesfvotrefdemandefd'adhésionfenflignefenfcliquantfici
OPEN : http://www.dong3.com.au/acces/
RESULT : Phishing is unresponsive
Email analysis :
NOTE : Content-Type : text/html
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < www-data@nice.fr >
NOTE : Received : from nice.fr ([139.59.132.93])
NOTE : Received : by nice.fr (Postfix, from userid 33)
NOTE : NOTE : X-Php-Originating-Script : 0:map.php
NOTE : Message-Id : < *.*@nice.fr >
NOTE : Lisez votre messagew
Lors de votre dérnier achats,vous avez été averti par un message vous informant de l'obligation d'adhérer à la
nouvelledréglementation conçernant la flabilité pour les achats pardC.Bdsur internet et de la mise en place d'un
arrêt pour vos futursdachats.
Or,nousfn'avons pas, cefjour,d'adhésionfdefvotrefpart et nousfsommes aufregret de vousdinformer que vous
pouvez plus utiliser votredcarte surfinternet
Adhésion;fFaitesfvotrefdemandefd'adhésionfenflignefenfcliquantfici
Cordialementggg
Copyright © 2016 Crédit Agricole
Copyright © 2016 A2 Hosting, All rights reserved.
You are receiving this email because you are an A2 Hosting Customer. If you don't wish to be on the Newsletter you can easily unsubscribe here or by controlling your contact options at My A2 Hosting.
Our mailing address is:
A2 Hosting
PO Box 2998
Ann Arbor, MI 48106
Add us to your address book
Quick Links
We're Hiring
My A2 Hosting
Open a Support Ticket
Affiliate Program - Earn $85!
Refer a Friend - Earn $50!
Review A2 Hosting!
Unsubscribe from this List Update Subscription and Notification Settings
Phishing analysis :
CLICK : Adhésion;fFaitesfvotrefdemandefd'adhésionfenflignefenfcliquantfici
OPEN : http://www.dong3.com.au/acces/
RESULT : Phishing is unresponsive
Email analysis :
NOTE : Content-Type : text/html
NOTE : Mime-Version : 1.0
NOTE : Return-Path : < www-data@nice.fr >
NOTE : Received : from nice.fr ([139.59.132.93])
NOTE : Received : by nice.fr (Postfix, from userid 33)
NOTE : NOTE : X-Php-Originating-Script : 0:map.php
NOTE : Message-Id : < *.*@nice.fr >
NOTE : Lisez votre messagew
Monday, April 25, 2016
View:779206304
McAfee - POTENTIALLY UNSAFE URLS DETECTED
The total number of URLs identified : 7
Blacklisted URLs : 0
Exceeded low threshold (30) : 5
Exceeded high threshold (80) : 1
Highest URL rating score identified : 127
For further information, contact your system administrator. Copyright 1999-2014 McAfee, Inc. All Rights Reserved. http://www.mcafee.com
Email analysis :
NOTE : itunes@napple.com
NOTE : Received : from INSTANCESWEB (13.92.255.51)
NOTE : by EXCHANGESVR.GEKTERNA-BH.LOCAL (192.168.1.252)
napple.com whois :
Domain Name: NAPPLE.COM
Registry Domain ID: 26759962_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.tucows.com
Registrar URL: http://tucowsdomains.com
Updated Date: 2011-08-19T09:52:45Z
Creation Date: 2000-05-10T12:49:07Z
Registrar Registration Expiration Date: 2019-05-10T12:49:07Z
Registrar: TUCOWS, INC.
Registrar IANA ID: 69
Registrar Abuse Contact Email: domainabuse@tucows.com
Registrar Abuse Contact Phone: +1.4165350123
Reseller: Blueweb Co., Ltd
Domain Status: ok
Registrant Name: yong rak Lee
Registrant Organization: Lee yong rak
Registrant Street: 105-1204 Samsung Apt. Majang-dong, Seongdong-gu
Registrant City: Seoul
Registrant Postal Code: 133754
Registrant Country: KR
Registrant Phone: +82.5021245689
Registrant Email: napple@napple.com
Admin Name: yong rak Lee
Admin Organization: Lee yong rak
Admin Street: 105-1204 Samsung Apt. Majang-dong Seongdong-gu
Admin City: seoul
Admin State/Province: Seoul
Admin Postal Code: 133754
Admin Country: KR
Admin Phone: +82.5021245689
Admin Fax: +82.226275228
Admin Email: napple@napple.com
Registry Tech ID:
Tech Name: blueweb blueweb
Tech Organization: blueweb
Tech Street: Hangangro3-ga #113 Hangang Grand Officetel Yongsan-gu
Tech City: Seoul
Tech State/Province: kr
Tech Postal Code: 140-013
Tech Country: KR
Tech Phone: +82.267322000
Tech Fax: +82.267322003
Tech Email: tdomain@blueweb.co.kr
Name Server: NIS.BLUEWEB.CO.KR
Name Server: NS.BLUEWEB.CO.KR
DNSSEC: unsigned
The total number of URLs identified : 7
Blacklisted URLs : 0
Exceeded low threshold (30) : 5
Exceeded high threshold (80) : 1
Highest URL rating score identified : 127
For further information, contact your system administrator. Copyright 1999-2014 McAfee, Inc. All Rights Reserved. http://www.mcafee.com
Email analysis :
NOTE : itunes@napple.com
NOTE : Received : from INSTANCESWEB (13.92.255.51)
NOTE : by EXCHANGESVR.GEKTERNA-BH.LOCAL (192.168.1.252)
napple.com whois :
Domain Name: NAPPLE.COM
Registry Domain ID: 26759962_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.tucows.com
Registrar URL: http://tucowsdomains.com
Updated Date: 2011-08-19T09:52:45Z
Creation Date: 2000-05-10T12:49:07Z
Registrar Registration Expiration Date: 2019-05-10T12:49:07Z
Registrar: TUCOWS, INC.
Registrar IANA ID: 69
Registrar Abuse Contact Email: domainabuse@tucows.com
Registrar Abuse Contact Phone: +1.4165350123
Reseller: Blueweb Co., Ltd
Domain Status: ok
Registrant Name: yong rak Lee
Registrant Organization: Lee yong rak
Registrant Street: 105-1204 Samsung Apt. Majang-dong, Seongdong-gu
Registrant City: Seoul
Registrant Postal Code: 133754
Registrant Country: KR
Registrant Phone: +82.5021245689
Registrant Email: napple@napple.com
Admin Name: yong rak Lee
Admin Organization: Lee yong rak
Admin Street: 105-1204 Samsung Apt. Majang-dong Seongdong-gu
Admin City: seoul
Admin State/Province: Seoul
Admin Postal Code: 133754
Admin Country: KR
Admin Phone: +82.5021245689
Admin Fax: +82.226275228
Admin Email: napple@napple.com
Registry Tech ID:
Tech Name: blueweb blueweb
Tech Organization: blueweb
Tech Street: Hangangro3-ga #113 Hangang Grand Officetel Yongsan-gu
Tech City: Seoul
Tech State/Province: kr
Tech Postal Code: 140-013
Tech Country: KR
Tech Phone: +82.267322000
Tech Fax: +82.267322003
Tech Email: tdomain@blueweb.co.kr
Name Server: NIS.BLUEWEB.CO.KR
Name Server: NS.BLUEWEB.CO.KR
DNSSEC: unsigned
Monday, April 11, 2016
Amazon account statut has been changed (Amazon Phishing Attempt)
Dear customer,
To get back into your account, you'll need to confirm your account . It's easy: Click the link below to open a secure browser window. Confirm that you're the owner of the account and then follow the instructions. .
By Clicking Here
Or contact Amazon Member Services Team. We're available 24 hours a day, 7 days a week. If you have recently updated your billing information, please disregard this message as we are processing the changes you have made.
-The Amazon Team
(EMID: CM_M_3.0_500_X_M_EN)(MD: 2014071907341)(EPID: 181719754)(ETID: 906330)
Phishing analysis :
CLICK : By Clicking Here
OPEN : http://www.lavandariatamico.com/aze/test@test.com
REDIRECT : http://mairie-thurey.fr/amz/
RESULT : Internal Server Error
Email analysis :
NOTE : xx@yy
NOTE : Mime-Version : 1.0
NOTE : Received : from CFHTERMINAL.COOKIESFROMHOME.COM ([68.15.179.5])
NOTE : Received : from CFHTERMINAL.COOKIESFROMHOME.COM ([127.0.0.1])
Tuesday, April 5, 2016
(No Subject) (Wells Fargo Phishing Attempt)
We have detect some unusual activities on your account, for your security we have place your account on hold. Please followed the bellowed link to update your security question or copy and past in your browser ..
http://welllsfargo-secure-update.de.be
Thanks for helping us keep your account safe
Phishing analysis :
CLICK : http://welllsfargo-secure-update.de.be
OPEN : url seems non responding.
Email analysis :
NOTE : maiu_04@theadgarage.com
NOTE : X-Mailer : Zoho Mail
NOTE : client-ip=74.201.84.163;
Subscribe to:
Posts (Atom)