A partir do dia 10/08/2016, a Via Fácil realmente iniciou a aplicação de multas.
Todo motorista que passar a mais de 40 km/h receberá uma multa por excesso
de velocidade. Segundo a STP (empresa administradora), a multa do Sem Parar
é gerada pela Policia Rodoviária.
você foi multado veja abaixo copia da multa.
Download da multa aqui...
Email analysis :
NOTE : detran@drz.com.br
NOTE : Received : from unknown (HELO pc-PC)
NOTE : (menoli@drz.com.br@200.204.161.106)
NOTE : by beta.sercomtel.com.br
Link analysis :
CLICK : Download da multa aqui...
OPEN : https://tinyurl.com/j3nav3q?=visualizar/multa/10/08/2016
DOWNLOAD FILE FROM : https://dc431.4shared.com
RESULT : File is a virus.
Virus analysis :
FILENAME : Infração-de-transito-15-08-2016.rar
SHA256 : b3baf1dedb71e91ca1006d412b8ee7eb59bf6a0388bb89abd3aefc3ee0c14dd6
Ad-Aware : Gen:Variant.Symmi.60015
Arcabit : Trojan.Symmi.DEA6F
Avast : Win32:Malware-gen
Avira (no cloud) : TR/Downloader.sdtq
BitDefender : Gen:Variant.Symmi.60015
ESET-NOD32 : Win32/TrojanDownloader.Banload.XMW
Emsisoft : Gen:Variant.Symmi.60015 (B)
F-Secure : Gen:Variant.Symmi.60015
GData : Gen:Variant.Symmi.60015
Ikarus : Trojan-Downloader.Win32.Banload
K7GW : Trojan-Downloader ( 004f64451 )
Kaspersky : Trojan-Downloader.Win32.Delf.kkdi
McAfee : Artemis!383F16692822
eScan : Gen:Variant.Symmi.60015
TrendMicro : HEUR_NAMETRICK.A
TrendMicro-HouseCall : TROJ_GE.4D16FF7F
Conclusion :
Virus hosted by 4shared.com
Link to the virus hosted by tinyurl.com
Wednesday, August 17, 2016
Thursday, January 14, 2016
URGENT RFQ (MORE VIRUS)
Dear Sir,
We sent you an order inquiry last week, but we did not receive any response from your regarding our order.
ATTACHED is a copy of NEW ORDER LIST for December Shipment. Please let me know the availability and your best prices of MATERIALS MARKED IN BLUE.
We will be waiting for your quotation.
Best Regards,
Roy
Al Nasser LLC
Virus analysis :
RFQ NO (14203) JAN DELIVERY ETA ETD PMM 01062016 jpeg1..ace
SHA256 : dacb8ff543c462f954500431f2a795a24ed10fa454cd7f27e3f0f1787dbe58fa
AVG : MSIL9.BEMV
Ad-Aware : Gen:Variant.Zusy.175290
Arcabit : Trojan.Zusy.D2ACBA
Avast : MSIL:Injector-NE [Trj]
BitDefender : Gen:Variant.Zusy.175290
Cyren : W32/Trojan.ZNMT-3910
DrWeb : Trojan.PWS.Siggen1.45471
ESET-NOD32 : a variant of MSIL/Injector.NLR
Emsisoft : Gen:Variant.Zusy.175290 (B)
F-Prot : W32/Trojan3.TDU
F-Secure : Gen:Variant.Zusy.175290
Fortinet : PossibleThreat.P0
GData : Gen:Variant.Zusy.175290
Ikarus : Evilware.Outbreak
Kaspersky : Trojan-PSW.Win32.Tepfer.psxdsw
MicroWorld-eScan : Gen:Variant.Zusy.175290
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Sophos : Mal/DrodAce-A
RFQ#Requirments Quote list ETD 05012015 RFxNumber 6200133094 jpeg2..ace
SHA256 : b7dd4530f2b97c33d1ea6df114d8fd7a9a6c6b1b78288394fbcf175b182e4da0
AVG : MSIL9.BEMV
Ad-Aware : Gen:Variant.Zusy.175290
Arcabit : Trojan.Zusy.D2ACBA
Avast : MSIL:Injector-NE [Trj]
Avira : TR/Dropper.MSIL.242773
BitDefender : Gen:Variant.Zusy.175290
Cyren : W32/Trojan.PNIW-7381
DrWeb : Trojan.PWS.Siggen1.45471
ESET-NOD32 : a variant of MSIL/Injector.NLR
Emsisoft : Gen:Variant.Zusy.175290 (B)
F-Secure : Gen:Variant.Zusy.175290
Fortinet : PossibleThreat.P0
GData : Gen:Variant.Zusy.175290
Ikarus : Evilware.Outbreak
Kaspersky : Trojan-PSW.Win32.Tepfer.psxdsx
MicroWorld-eScan : Gen:Variant.Zusy.175290
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Sophos : Mal/DrodAce-A
Email analysis :
NOTE : brainkings24@gmail.com
NOTE : ecos@atr.ecos.kz
NOTE : Received : from [142.54.171.74] (helo=User)
NOTE : by ecos.kz
We sent you an order inquiry last week, but we did not receive any response from your regarding our order.
ATTACHED is a copy of NEW ORDER LIST for December Shipment. Please let me know the availability and your best prices of MATERIALS MARKED IN BLUE.
We will be waiting for your quotation.
Best Regards,
Roy
Al Nasser LLC
Virus analysis :
RFQ NO (14203) JAN DELIVERY ETA ETD PMM 01062016 jpeg1..ace
SHA256 : dacb8ff543c462f954500431f2a795a24ed10fa454cd7f27e3f0f1787dbe58fa
AVG : MSIL9.BEMV
Ad-Aware : Gen:Variant.Zusy.175290
Arcabit : Trojan.Zusy.D2ACBA
Avast : MSIL:Injector-NE [Trj]
BitDefender : Gen:Variant.Zusy.175290
Cyren : W32/Trojan.ZNMT-3910
DrWeb : Trojan.PWS.Siggen1.45471
ESET-NOD32 : a variant of MSIL/Injector.NLR
Emsisoft : Gen:Variant.Zusy.175290 (B)
F-Prot : W32/Trojan3.TDU
F-Secure : Gen:Variant.Zusy.175290
Fortinet : PossibleThreat.P0
GData : Gen:Variant.Zusy.175290
Ikarus : Evilware.Outbreak
Kaspersky : Trojan-PSW.Win32.Tepfer.psxdsw
MicroWorld-eScan : Gen:Variant.Zusy.175290
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Sophos : Mal/DrodAce-A
RFQ#Requirments Quote list ETD 05012015 RFxNumber 6200133094 jpeg2..ace
SHA256 : b7dd4530f2b97c33d1ea6df114d8fd7a9a6c6b1b78288394fbcf175b182e4da0
AVG : MSIL9.BEMV
Ad-Aware : Gen:Variant.Zusy.175290
Arcabit : Trojan.Zusy.D2ACBA
Avast : MSIL:Injector-NE [Trj]
Avira : TR/Dropper.MSIL.242773
BitDefender : Gen:Variant.Zusy.175290
Cyren : W32/Trojan.PNIW-7381
DrWeb : Trojan.PWS.Siggen1.45471
ESET-NOD32 : a variant of MSIL/Injector.NLR
Emsisoft : Gen:Variant.Zusy.175290 (B)
F-Secure : Gen:Variant.Zusy.175290
Fortinet : PossibleThreat.P0
GData : Gen:Variant.Zusy.175290
Ikarus : Evilware.Outbreak
Kaspersky : Trojan-PSW.Win32.Tepfer.psxdsx
MicroWorld-eScan : Gen:Variant.Zusy.175290
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Sophos : Mal/DrodAce-A
Email analysis :
NOTE : brainkings24@gmail.com
NOTE : ecos@atr.ecos.kz
NOTE : Received : from [142.54.171.74] (helo=User)
NOTE : by ecos.kz
Urgent RQF
Dear Sir,
We sent you an order inquiry last week, but we did not receive any response from your regarding our order.
ATTACHED is a copy of NEW ORDER LIST for December Shipment. Please let me know the availability and your best prices of MATERIALS MARKED IN BLUE.
We will be waiting for your quotation.
Best Regards,
Roy
Al Nasser LLC
Proforma Invoice
RFQ#Requirments Quote list ETA ETD 05012015 RFxNumber 6200133094 jpeg.ace
Virus analysis :
DrWeb : Trojan.PWS.Stealer.15120
ESET-NOD32 : a variant of MSIL/Injector.NLF
Qihoo-360 : HEUR/QVM03.0.Malware.Gen 20160105
Sophos : Mal/DrodAce-A 20160105
Email analysis :
NOTE : prabhukumar59@yahoo.com
NOTE : ecos@atr.ecos.kz
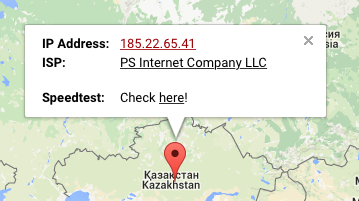
NOTE : 185.22.65.41 (mail.ecos.kz)
NOTE : Received : from [142.54.171.74] (helo=User) by ecos.kz
We sent you an order inquiry last week, but we did not receive any response from your regarding our order.
ATTACHED is a copy of NEW ORDER LIST for December Shipment. Please let me know the availability and your best prices of MATERIALS MARKED IN BLUE.
We will be waiting for your quotation.
Best Regards,
Roy
Al Nasser LLC
Proforma Invoice
RFQ#Requirments Quote list ETA ETD 05012015 RFxNumber 6200133094 jpeg.ace
Virus analysis :
DrWeb : Trojan.PWS.Stealer.15120
ESET-NOD32 : a variant of MSIL/Injector.NLF
Qihoo-360 : HEUR/QVM03.0.Malware.Gen 20160105
Sophos : Mal/DrodAce-A 20160105
Email analysis :
NOTE : prabhukumar59@yahoo.com
NOTE : ecos@atr.ecos.kz
NOTE : 185.22.65.41 (mail.ecos.kz)
NOTE : Received : from [142.54.171.74] (helo=User) by ecos.kz
Wednesday, October 28, 2015
New order 1320
Dear supplier,
Please find the attached purchase order and acknowledge the receipt.
We await your response with details.
Thanks,
Monica Paquette
Purchasing Manager.
JUBAILI TRADE COMPANY.
32107 Bad Salzuflen
Germany
T: +49-5208-9102-7523
F: +49-5208-9102-9054
M: +49 151 616023605
Web: www.ararmaturen.net
PO_FY6667544pdf.ace
PO_FY6667544pdf.ace analysis :
PO_FY6667544pdf.ace is a virus.
Virus analysis :
AVG : MSIL9.XGT
Ad-Aware : Gen:Variant.Kazy.758648
Arcabit : Trojan.Kazy.DB9378
BitDefender : Gen:Variant.Kazy.758648
ESET-NOD32 : a variant of MSIL/Kryptik.DZP
Emsisoft : Gen:Variant.Kazy.758648 (B)
F-Secure : Gen:Variant.Kazy.758648
GData : Gen:Variant.Kazy.758648
Ikarus : Trojan.MSIL.Crypt
Kaspersky : Trojan.MSIL.Inject.dbmu
MicroWorld-eScan : Gen:Variant.Kazy.758648
Microsoft : Trojan:Win32/Dynamer!ac
Sophos : Mal/DrodAce-A
TrendMicro : TSPY_GOLROTED.CP
TrendMicro-HouseCall : TSPY_GOLROTED.CP
Email analysis :
NOTE : monica.p@tech-center.com
NOTE : Received : from 210.195.249.3 (klg-58-154.tm.net.my [202.188.58.154])
NOTE : by cactus4.qatar.net.qa (Oracle Communications Messaging Exchange Server)
NOTE : does not designate 82.148.101.71 as permitted sender
Please find the attached purchase order and acknowledge the receipt.
We await your response with details.
Thanks,
Monica Paquette
Purchasing Manager.
JUBAILI TRADE COMPANY.
32107 Bad Salzuflen
Germany
T: +49-5208-9102-7523
F: +49-5208-9102-9054
M: +49 151 616023605
Web: www.ararmaturen.net
PO_FY6667544pdf.ace
PO_FY6667544pdf.ace analysis :
PO_FY6667544pdf.ace is a virus.
Virus analysis :
AVG : MSIL9.XGT
Ad-Aware : Gen:Variant.Kazy.758648
Arcabit : Trojan.Kazy.DB9378
BitDefender : Gen:Variant.Kazy.758648
ESET-NOD32 : a variant of MSIL/Kryptik.DZP
Emsisoft : Gen:Variant.Kazy.758648 (B)
F-Secure : Gen:Variant.Kazy.758648
GData : Gen:Variant.Kazy.758648
Ikarus : Trojan.MSIL.Crypt
Kaspersky : Trojan.MSIL.Inject.dbmu
MicroWorld-eScan : Gen:Variant.Kazy.758648
Microsoft : Trojan:Win32/Dynamer!ac
Sophos : Mal/DrodAce-A
TrendMicro : TSPY_GOLROTED.CP
TrendMicro-HouseCall : TSPY_GOLROTED.CP
Email analysis :
NOTE : monica.p@tech-center.com
NOTE : Received : from 210.195.249.3 (klg-58-154.tm.net.my [202.188.58.154])
NOTE : by cactus4.qatar.net.qa (Oracle Communications Messaging Exchange Server)
NOTE : does not designate 82.148.101.71 as permitted sender
Friday, July 24, 2015
Inquiry
Dear Sir,
Refers to the new order raised to your company,
Attached please find the order and swift copy of the last shipment.
Kindly open the PDF file to view details
Regards
Thanks & Regards,
Michail Harik
CMT executive – Platinum Team
Aramex Doha – Doha, Qatar
Tel +974 44200193
aramex.com
pr.no.567890.docx
File analysis :
File : pr.no.567890.docx
SHA256 : dbdb40864695b3e8ffd980f051d829b38fb38bbd93711cfb2188165cc58c0ec9
NOTE : File pr.no.567890.docx is a virus
AVG : PSW.Generic12.CAPW
Ad-Aware : Trojan.GenericKD.2591074
Arcabit Trojan.Generic.D278962
Avast : MSIL:Zbot-Z [Trj]
Avira : TR/Dropper.MSIL.173869
BitDefender : Trojan.GenericKD.2591074
DrWeb : Trojan.PWS.Siggen1.39434
ESET-NOD32 : a variant of MSIL/Injector.KXP
Emsisoft : Trojan.GenericKD.2591074 (B)
F-Secure : Trojan.GenericKD.2591074
Fortinet : MSIL/Injector.KSL!tr
GData : Trojan.GenericKD.2591074
Ikarus : Trojan.MSIL.Injector
Kaspersky : Trojan-Dropper.Win32.Sysn.batm
McAfee : PWS-FCDG!4A71EF2B2FA1
McAfee-GW-Edition : PWS-FCDG!4A71EF2B2FA1
MicroWorld-eScan : Trojan.GenericKD.2591074
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Symantec : Infostealer.Limitail
Email analysis :
NOTE : info@paltinum.com
NOTE : X-Sender-Id : nisakorn@thai-nichi.com
NOTE : X-Msmail-Priority : Normal
NOTE : X-Mimeole : Produced By Microsoft MimeOLE V6.00.2600.0000
NOTE : Mime-Version : 1.0
NOTE : X-Priority : 3
NOTE : X-Mailer : Microsoft Outlook Express 6.00.2600.0000
NOTE : client-ip=173.203.6.144;
NOTE : Received : from smtp144.ord.emailsrvr.com
NOTE : (smtp144.ord.emailsrvr.com. [173.203.6.144])
NOTE : Received : from smtp27.relay.ord1a.emailsrvr.com
NOTE : (localhost.localdomain [127.0.0.1]) by smtp27.relay.ord1a.emailsrvr.com
NOTE : Received : by smtp27.relay.ord1a.emailsrvr.com
NOTE : (Authenticated sender: nisakorn-AT-thai-nichi.com)
NOTE : Received : from User ([UNAVAILABLE]. [66.76.199.160])
NOTE : by 0.0.0.0:25 (trex/5.4.2)
NOTE : Inquiry
Refers to the new order raised to your company,
Attached please find the order and swift copy of the last shipment.
Kindly open the PDF file to view details
Regards
Thanks & Regards,
Michail Harik
CMT executive – Platinum Team
Aramex Doha – Doha, Qatar
Tel +974 44200193
aramex.com
pr.no.567890.docx
File analysis :
File : pr.no.567890.docx
SHA256 : dbdb40864695b3e8ffd980f051d829b38fb38bbd93711cfb2188165cc58c0ec9
NOTE : File pr.no.567890.docx is a virus
AVG : PSW.Generic12.CAPW
Ad-Aware : Trojan.GenericKD.2591074
Arcabit Trojan.Generic.D278962
Avast : MSIL:Zbot-Z [Trj]
Avira : TR/Dropper.MSIL.173869
BitDefender : Trojan.GenericKD.2591074
DrWeb : Trojan.PWS.Siggen1.39434
ESET-NOD32 : a variant of MSIL/Injector.KXP
Emsisoft : Trojan.GenericKD.2591074 (B)
F-Secure : Trojan.GenericKD.2591074
Fortinet : MSIL/Injector.KSL!tr
GData : Trojan.GenericKD.2591074
Ikarus : Trojan.MSIL.Injector
Kaspersky : Trojan-Dropper.Win32.Sysn.batm
McAfee : PWS-FCDG!4A71EF2B2FA1
McAfee-GW-Edition : PWS-FCDG!4A71EF2B2FA1
MicroWorld-eScan : Trojan.GenericKD.2591074
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Symantec : Infostealer.Limitail
Email analysis :
NOTE : info@paltinum.com
NOTE : X-Sender-Id : nisakorn@thai-nichi.com
NOTE : X-Msmail-Priority : Normal
NOTE : X-Mimeole : Produced By Microsoft MimeOLE V6.00.2600.0000
NOTE : Mime-Version : 1.0
NOTE : X-Priority : 3
NOTE : X-Mailer : Microsoft Outlook Express 6.00.2600.0000
NOTE : client-ip=173.203.6.144;
NOTE : Received : from smtp144.ord.emailsrvr.com
NOTE : (smtp144.ord.emailsrvr.com. [173.203.6.144])
NOTE : Received : from smtp27.relay.ord1a.emailsrvr.com
NOTE : (localhost.localdomain [127.0.0.1]) by smtp27.relay.ord1a.emailsrvr.com
NOTE : Received : by smtp27.relay.ord1a.emailsrvr.com
NOTE : (Authenticated sender: nisakorn-AT-thai-nichi.com)
NOTE : Received : from User ([UNAVAILABLE]. [66.76.199.160])
NOTE : by 0.0.0.0:25 (trex/5.4.2)
NOTE : Inquiry
Monday, July 20, 2015
Order for Sp/LLC /2015 (Virus)
Dear Sir/Madam,
It was nice to see you again. In attachment you will find the order for Sp/LLC /2015 Please first confirm the price with us. If you have any question about the changes, please ask. In attachment also the logo’s for NieZoe Woven Label new. I know the woven label NieZoe you have to take more quantity. Please let us know the quantity and price. We can use in future also.
Thank you in advance.
Met vriendelijke groet,
Best regards,
Mit Mreundlichen Krussen,
logo
Larlou Lvan Looten
Sales Manager
Nmbyerstraat Noord 162 | 6225 EJ Maastricht The Netherlands | HR14054804 VAT NL809075957B00
T 0031 43 3521470
File analysis :
SHA256 : cc4db92ec0f923c02171c746fd8417b6763257d9a2fcfd6b30818da344791ea3
Filename : Sp-LLC -2015.docx
ALYac : Gen:Variant.Kazy.679360
Ad-Aware : Gen:Variant.Kazy.679360
Arcabit : Trojan.Kazy.DA5DC0
BitDefender : Gen:Variant.Kazy.679360
DrWeb : BackDoor.Bladabindi.1056
ESET-NOD32 : a variant of MSIL/Injector.KSL
Emsisoft : Gen:Variant.Kazy.679360 (B)
F-Secure : Gen:Variant.Kazy.679360
Fortinet : MSIL/Injector.KSL!tr
GData : Gen:Variant.Kazy.679360
Kaspersky : HEUR:Trojan.Win32.Generic
MicroWorld-eScan : Gen:Variant.Kazy.679360
TrendMicro-HouseCall : TROJ_GE.856647F7
Email analysis :
NOTE : NieZoe@NieZoe.COM
NOTE : nisakorn@thai-nichi.com
NOTE : Received : from User ([UNAVAILABLE].
NOTE : [66.76.199.160]) by 0.0.0.0:25 (trex/5.4.2);
NOTE : Received : by smtp24.relay.ord1a.emailsrvr.com
NOTE : (Authenticated sender: nisakorn-AT-thai-nichi.com)
It was nice to see you again. In attachment you will find the order for Sp/LLC /2015 Please first confirm the price with us. If you have any question about the changes, please ask. In attachment also the logo’s for NieZoe Woven Label new. I know the woven label NieZoe you have to take more quantity. Please let us know the quantity and price. We can use in future also.
Thank you in advance.
Met vriendelijke groet,
Best regards,
Mit Mreundlichen Krussen,
logo
Larlou Lvan Looten
Sales Manager
Nmbyerstraat Noord 162 | 6225 EJ Maastricht The Netherlands | HR14054804 VAT NL809075957B00
T 0031 43 3521470
File analysis :
SHA256 : cc4db92ec0f923c02171c746fd8417b6763257d9a2fcfd6b30818da344791ea3
Filename : Sp-LLC -2015.docx
ALYac : Gen:Variant.Kazy.679360
Ad-Aware : Gen:Variant.Kazy.679360
Arcabit : Trojan.Kazy.DA5DC0
BitDefender : Gen:Variant.Kazy.679360
DrWeb : BackDoor.Bladabindi.1056
ESET-NOD32 : a variant of MSIL/Injector.KSL
Emsisoft : Gen:Variant.Kazy.679360 (B)
F-Secure : Gen:Variant.Kazy.679360
Fortinet : MSIL/Injector.KSL!tr
GData : Gen:Variant.Kazy.679360
Kaspersky : HEUR:Trojan.Win32.Generic
MicroWorld-eScan : Gen:Variant.Kazy.679360
TrendMicro-HouseCall : TROJ_GE.856647F7
Email analysis :
NOTE : NieZoe@NieZoe.COM
NOTE : nisakorn@thai-nichi.com
NOTE : Received : from User ([UNAVAILABLE].
NOTE : [66.76.199.160]) by 0.0.0.0:25 (trex/5.4.2);
NOTE : Received : by smtp24.relay.ord1a.emailsrvr.com
NOTE : (Authenticated sender: nisakorn-AT-thai-nichi.com)
Subscribe to:
Posts (Atom)