Hola.
Como habíamos conversado el día 21/11/2017 Se ha efectuado la transferencia a su cuenta sobre la anulación de la compra, Por favor verifique.
Nota: Usted puede imprimir el recibo Clicando Aquí
B&F - Abogados Asociados - CL
Email analysis :
NOTE : abogados82734.com@live.com
NOTE : root@live.com
NOTE : root@live.com does not designate 173.255.211.90 as permitted sender
Phishing analysis :
CLICK : Clicando Aquí
STUDY LINK : https://bit.do/dUvpv?*@*.com
REMOVE EMAIL : https://bit.do/dUvpv
ADD - : https://bit.do/dUvpv-
SCREENSHOT :
DOWNLOAD : http://inmisrad.org/Comprobante.zip
FILE : VIRUS
Virus :
Cyren : JS/Downldr.ES2!Eldorado
DrWeb : VBS.Psyme.126
ESET-NOD32 : JS/TrojanDownloader.Banload.RM
F-Prot : JS/Downldr.ES2!Eldorado
Ikarus : Win32.Outbreak
Kaspersky : HEUR:Trojan.Script.Agent.gen
NANO-Antivirus : Trojan.Script.Heuristic-js.iacgm
Qihoo-360 : virus.js.qexvmc.1080
Rising : Downloader.Banload!8.15B (TOPIS:acBkcffG9cJ)
Symantec : JS.Downloader!gen40
ZoneAlarm : HEUR:Trojan.Script.Agent.gen
Paste :
PASTE : https://pastebin.com/upZWkBFT
Tuesday, November 28, 2017
Thursday, August 24, 2017
About Payment 23-08-2017
Good day,
We have been instructed by your customer to make this transfer to you. Please we are very sorry for the delay in the payment, it was due to the Holidays. Attached is the Payment remittance copy for your reference.Please confirm for errors and get back to us through email.
Best Regards,
DANIEL MURRAY
Sharaf Exchange LLC.
Address:Sharaf Exchange Shop No. G15,
Union Co-Op Society,
Al Aweer,Near Fruit and Vegetable Market, Ras Al Khor, Dubai - UAE
Phone No:04-3200698
Website: http://www.sharafexchange.com
IMG-051220378052.DOC
Email analysis :
NOTE : danielmurray@mail.ru
NOTE : Received : from [104.243.26.4] (port=51917 helo=User)
NOTE : by shared.buxar-host.in
NOTE : bylinkove-zdravi@seznam.cz
Virus analysis :
Ad-Aware W97m.Downloader.GCK
AhnLab-V3 W97M/Downloader
BitDefender W97m.Downloader.GCK
DrWeb W97M.DownLoader.1802
eScan W97m.Downloader.GCK
F-Secure W97m.Downloader.GCK
GData W97m.Downloader.GCK
Ikarus Trojan-Downloader.VBA.Agent
MAX malware (ai score=81)
NANO-Antivirus Trojan.Ole2.Vbs-heuristic.druvzi
ZoneAlarm HEUR:Trojan-Downloader.Script.Generic
We have been instructed by your customer to make this transfer to you. Please we are very sorry for the delay in the payment, it was due to the Holidays. Attached is the Payment remittance copy for your reference.Please confirm for errors and get back to us through email.
Best Regards,
DANIEL MURRAY
Sharaf Exchange LLC.
Address:Sharaf Exchange Shop No. G15,
Union Co-Op Society,
Al Aweer,Near Fruit and Vegetable Market, Ras Al Khor, Dubai - UAE
Phone No:04-3200698
Website: http://www.sharafexchange.com
IMG-051220378052.DOC
Email analysis :
NOTE : danielmurray@mail.ru
NOTE : Received : from [104.243.26.4] (port=51917 helo=User)
NOTE : by shared.buxar-host.in
NOTE : bylinkove-zdravi@seznam.cz
Virus analysis :
Ad-Aware W97m.Downloader.GCK
AhnLab-V3 W97M/Downloader
BitDefender W97m.Downloader.GCK
DrWeb W97M.DownLoader.1802
eScan W97m.Downloader.GCK
F-Secure W97m.Downloader.GCK
GData W97m.Downloader.GCK
Ikarus Trojan-Downloader.VBA.Agent
MAX malware (ai score=81)
NANO-Antivirus Trojan.Ole2.Vbs-heuristic.druvzi
ZoneAlarm HEUR:Trojan-Downloader.Script.Generic
317061979269082.doc (Virus)
317061979269082.doc
Email analysis :
NOTE : Return-Path: < noreply@xo.net >
NOTE : identity=mailfrom; client-ip=208.36.229.61;
NOTE : helo=xo.net; envelope-from=noreply@xo.net;
NOTE : Received: from xo.net (208.36.229.61.ptr.us.xo.net [208.36.229.61])
NOTE : Content-Type: application/msword; name="317061979269082.doc"
NOTE : From: < noreply@ulegv.com >
NOTE : 208.36.229.61.ptr.us.xo.net)
Virus analysis :
Ad-Aware W97M.Downloader.GDB
AegisLab Troj.Script.Agent!c
AhnLab-V3 W97M/Downloader
ALYac Trojan.Downloader.W97M.Gen
Arcabit HEUR.VBA.Trojan.e
Avast Other:Malware-gen [Trj]
AVG Other:Malware-gen [Trj]
Avira W97M/Dldr.Agent.mgjui
Baidu VBA.Trojan-Downloader.Agent.bup
BitDefender W97M.Downloader.GDB
Comodo UnclassifiedMalware
Cyren PP97M/Downldr
DrWeb W97M.DownLoader.1961
Emsisoft Trojan-Downloader.Agent (A)
eScan W97M.Downloader.GDB
ESET-NOD32 VBA/TrojanDownloader.Agent.DYZ
F-Prot New or modified PP97M/Downldr
F-Secure W97M.Downloader.GDB
Fortinet WM/Agent.Q!tr.dldr
GData W97M.Downloader.GDB
Ikarus Trojan-Downloader.VBA.Agent
Kaspersky HEUR:Trojan.Script.Agent.gen
MAX malware (ai score=99)
McAfee W97M/Downloader.cfm
McAfee-GW-Edition W97M/Downloader.cfm
Microsoft TrojanDownloader:O97M/Donoff
Panda O97M/Downloader
Sophos AV Troj/DocDl-KBA
Symantec W97M.Downloader
Tencent Win32.Trojan-downloader.Agent.Sxyr
TrendMicro W2KM_DLOADR.YYTCY
TrendMicro-HouseCall W2KM_DLOADR.YYTCY
ViRobot W97M.S.Agent.76249
ZoneAlarm HEUR:Trojan.Script.Agent.gen
Email analysis :
NOTE : Return-Path: < noreply@xo.net >
NOTE : identity=mailfrom; client-ip=208.36.229.61;
NOTE : helo=xo.net; envelope-from=noreply@xo.net;
NOTE : Received: from xo.net (208.36.229.61.ptr.us.xo.net [208.36.229.61])
NOTE : Content-Type: application/msword; name="317061979269082.doc"
NOTE : From: < noreply@ulegv.com >
NOTE : 208.36.229.61.ptr.us.xo.net)
Virus analysis :
Ad-Aware W97M.Downloader.GDB
AegisLab Troj.Script.Agent!c
AhnLab-V3 W97M/Downloader
ALYac Trojan.Downloader.W97M.Gen
Arcabit HEUR.VBA.Trojan.e
Avast Other:Malware-gen [Trj]
AVG Other:Malware-gen [Trj]
Avira W97M/Dldr.Agent.mgjui
Baidu VBA.Trojan-Downloader.Agent.bup
BitDefender W97M.Downloader.GDB
Comodo UnclassifiedMalware
Cyren PP97M/Downldr
DrWeb W97M.DownLoader.1961
Emsisoft Trojan-Downloader.Agent (A)
eScan W97M.Downloader.GDB
ESET-NOD32 VBA/TrojanDownloader.Agent.DYZ
F-Prot New or modified PP97M/Downldr
F-Secure W97M.Downloader.GDB
Fortinet WM/Agent.Q!tr.dldr
GData W97M.Downloader.GDB
Ikarus Trojan-Downloader.VBA.Agent
Kaspersky HEUR:Trojan.Script.Agent.gen
MAX malware (ai score=99)
McAfee W97M/Downloader.cfm
McAfee-GW-Edition W97M/Downloader.cfm
Microsoft TrojanDownloader:O97M/Donoff
Panda O97M/Downloader
Sophos AV Troj/DocDl-KBA
Symantec W97M.Downloader
Tencent Win32.Trojan-downloader.Agent.Sxyr
TrendMicro W2KM_DLOADR.YYTCY
TrendMicro-HouseCall W2KM_DLOADR.YYTCY
ViRobot W97M.S.Agent.76249
ZoneAlarm HEUR:Trojan.Script.Agent.gen
Thursday, December 8, 2016
Message notification *@gmail.com (Link to virus)
Nddcole Watddson (Google Support) just sent you a message:
06/12/2016
Undeliverable messages (*@gmail.com).
Get more information
Don't want occasional updates about Gmail activity? Change what email Google Team sends you.
Email analysis :
NOTE : Received : from server.oeirasdigital.pt
NOTE : (server.oeirasdigital.pt. [213.229.111.207])
NOTE : client-ip=213.229.111.207;
NOTE : X-Php-Originating-Script : 10000:bisend.php
Link analysis :
CLICK : Get more information
OPEN : http://projetomac.org/wp/Undeliverable_messages.html
DOWNLOAD A FILE : Undeliverable_messages.zip
INFORMATION : Undeliverable_messages.zip is a virus
SHA256 : be0908fbf059517f8ea204d1636e00a7810146fb9c920fc01bb4315b8e8e0067
Virus analysis :
AegisLab Troj.Downloader.Script!c
Arcabit HEUR.JS.Trojan.ba
Cyren JS/Nemucod.EY!Eldorado
F-Prot JS/Nemucod.EY!Eldorado
Fortinet Malware_Generic.P0
K7AntiVirus Trojan ( 004dfe6d1 )
K7GW Trojan ( 004dfe6d1 ) 20161208
Kaspersky HEUR:Trojan-Downloader.Script.Generic
Sophos Mal/DrodZp-A
Exposing virus :
PASTEBIN : http://pastebin.com/20PLKDCB
RAW : http://pastebin.com/raw/20PLKDCB
Tuesday, November 29, 2016
New incoming Fax from 908.8325722
You Have a new Fax message
From: 908.8145483
Receiving date: November 28, 2016
Pages: 3
You can view your message on our website:
https://service.ringcentral.com/ messages/download.aspx?fax_id=1805802
Thank you for using RingCentral.
Link analysis :
CLICK : https://service.ringcentral.com/ messages/download.aspx?fax_id=1805802
OPEN : http://787.vn/wp-content/themes/tourpackage-v1-02/backup/get.php?id=dGVzdEB0ZXN0LmNvbQ==
DOWNLOAD : fax_test.doc
File analysis :
OPEN : fax_test.doc
SHA256 : c0b3934b594a23dd88a42c0e96ccbbf7f88c633a19d82833d6d9bbf47630a0c1
RESULT : fax_test.doc is a virus
Virus analysis :
Avast : VBA:Downloader-DSL [Trj]
ClamAV : Doc.Dropper.Agent-1847249
Kaspersky : Trojan-Downloader.MSWord.Agent.avj
Qihoo-360 : virus.office.gen.70
Sophos : Troj/DocDl-FTZ
Symantec : W97M.Downloader
Email analysis :
NOTE : ringcentral@faxmessage.com
NOTE : 74.143.65.242 (rrcs-74-143-65-242.central.biz.rr.com)
NOTE : Mime-Version : 1.0
From: 908.8145483
Receiving date: November 28, 2016
Pages: 3
You can view your message on our website:
https://service.ringcentral.com/ messages/download.aspx?fax_id=1805802
Thank you for using RingCentral.
Link analysis :
CLICK : https://service.ringcentral.com/ messages/download.aspx?fax_id=1805802
OPEN : http://787.vn/wp-content/themes/tourpackage-v1-02/backup/get.php?id=dGVzdEB0ZXN0LmNvbQ==
DOWNLOAD : fax_test.doc
File analysis :
OPEN : fax_test.doc
SHA256 : c0b3934b594a23dd88a42c0e96ccbbf7f88c633a19d82833d6d9bbf47630a0c1
RESULT : fax_test.doc is a virus
Virus analysis :
Avast : VBA:Downloader-DSL [Trj]
ClamAV : Doc.Dropper.Agent-1847249
Kaspersky : Trojan-Downloader.MSWord.Agent.avj
Qihoo-360 : virus.office.gen.70
Sophos : Troj/DocDl-FTZ
Symantec : W97M.Downloader
Email analysis :
NOTE : ringcentral@faxmessage.com
NOTE : 74.143.65.242 (rrcs-74-143-65-242.central.biz.rr.com)
NOTE : Mime-Version : 1.0
Tuesday, November 22, 2016
Your LogMein.com subscription has expired! (Virus)
Dear client,
You are receiving this message because your subscription for LogMeIn Central has expired.
We were not able to charge you with the due amount because your credit card was declined.
You can download the bill directly from the LogMeIn website:
https://accounts.logme.in/billing.aspx?clusterid=0724&view_bill_id=3716 4647&file_type=doc
Please use another credit card or payment method in order to avoid complete service interruption.
Event type: Credit Card Declined
Account email: *.*
At: 21/11/2016
If you need more help, visit LogMeIn Support at:
http://solutions.logmein. com/SalesContactUs
Important Security Notice:
LogMeIn will never for your password or other sensitive information by email.
(Please don't reply to this email, as it's sent from an address that's not monitored.)
© LogMeIn Inc
Virus analysis :
CLICK : https://accounts.logme.in/billing.aspx?clusterid=0724&view_bill_id=3716 4647&file_type=doc
OPEN : https://reg.vn/en/view_bill.php?id=d2VibWFzdGVyQHJiY2FmZS5jb20=
DOWNLOAD : lgm_bill89831.doc
lgm_bill89831.doc : VIRUS
lgm_bill89831.doc analysis :
SHA256 : fc1f1845e47d4494a02407c524eb0e94b6484045adb783e90406367ae20a83ac
FILE : lgm_bill89831.doc
ALYac : Trojan.Downloader.W97M.Gen
Ad-Aware : W97M.Downloader.ESE
AegisLab : Troj.Downloader.Msword.Agent!c
Arcabit : W97M.Downloader.ESE
BitDefender : W97M.Downloader.ESE
Cyren : W97M/Nastjencro
ESET-NOD32 : VBA/Kryptik.T
Emsisoft : W97M.Downloader.ESE (B)
F-Prot : New or modified W97M/Nastjencro
F-Secure : Trojan:W97M/Nastjencro.A
GData : W97M.Downloader.ESE
Ikarus : Trojan-Downloader.VBA.Agent 20161121
Kaspersky : Trojan-Downloader.MSWord.Agent.auz
McAfee : W97M/Dropper.cu
McAfee-GW-Edition : W97M/Dropper.cu
eScan : W97M.Downloader.ESE
Microsoft : TrojanDownloader:O97M/Donoff!map
Sophos : Troj/DocDl-FQK
Symantec : W97M.Downloader
Tencent : Win32.Trojan.Inject.Auto
TrendMicro : W2KM_HANCITOR.AUSTT
TrendMicro-HouseCall : W2KM_HANCITOR.AUSTT
Email analysis :
NOTE : billing@secure-lgm.com
NOTE : Received : from wsip-70-165-74-172.hr.hr.cox.net
NOTE : (HELO secure-lgm.com) (70.165.74.172)
You are receiving this message because your subscription for LogMeIn Central has expired.
We were not able to charge you with the due amount because your credit card was declined.
You can download the bill directly from the LogMeIn website:
https://accounts.logme.in/billing.aspx?clusterid=0724&view_bill_id=3716 4647&file_type=doc
Please use another credit card or payment method in order to avoid complete service interruption.
Event type: Credit Card Declined
Account email: *.*
At: 21/11/2016
If you need more help, visit LogMeIn Support at:
http://solutions.logmein. com/SalesContactUs
Important Security Notice:
LogMeIn will never for your password or other sensitive information by email.
(Please don't reply to this email, as it's sent from an address that's not monitored.)
© LogMeIn Inc
Virus analysis :
CLICK : https://accounts.logme.in/billing.aspx?clusterid=0724&view_bill_id=3716 4647&file_type=doc
OPEN : https://reg.vn/en/view_bill.php?id=d2VibWFzdGVyQHJiY2FmZS5jb20=
DOWNLOAD : lgm_bill89831.doc
lgm_bill89831.doc : VIRUS
lgm_bill89831.doc analysis :
SHA256 : fc1f1845e47d4494a02407c524eb0e94b6484045adb783e90406367ae20a83ac
FILE : lgm_bill89831.doc
ALYac : Trojan.Downloader.W97M.Gen
Ad-Aware : W97M.Downloader.ESE
AegisLab : Troj.Downloader.Msword.Agent!c
Arcabit : W97M.Downloader.ESE
BitDefender : W97M.Downloader.ESE
Cyren : W97M/Nastjencro
ESET-NOD32 : VBA/Kryptik.T
Emsisoft : W97M.Downloader.ESE (B)
F-Prot : New or modified W97M/Nastjencro
F-Secure : Trojan:W97M/Nastjencro.A
GData : W97M.Downloader.ESE
Ikarus : Trojan-Downloader.VBA.Agent 20161121
Kaspersky : Trojan-Downloader.MSWord.Agent.auz
McAfee : W97M/Dropper.cu
McAfee-GW-Edition : W97M/Dropper.cu
eScan : W97M.Downloader.ESE
Microsoft : TrojanDownloader:O97M/Donoff!map
Sophos : Troj/DocDl-FQK
Symantec : W97M.Downloader
Tencent : Win32.Trojan.Inject.Auto
TrendMicro : W2KM_HANCITOR.AUSTT
TrendMicro-HouseCall : W2KM_HANCITOR.AUSTT
Email analysis :
NOTE : billing@secure-lgm.com
NOTE : Received : from wsip-70-165-74-172.hr.hr.cox.net
NOTE : (HELO secure-lgm.com) (70.165.74.172)
Friday, November 18, 2016
RE: shipping done
We shipped your crap.
Here s the tracking invoice :
https://www.ups.com/?tracking_invoice=219371293129312& action=download
Let us know when it arrives.
Thanks
Phishing analysis :
CLICK : https://www.ups.com/?tracking_invoice=219371293129312& action=download
OPEN : http://invoice-portal.com/invoices/get.php?id=d2VibWFzdGVyQHJiY2FmZS5jb20=
RESULT : Download a file called : inv11172016.doc
File analysis :
ESET-NOD32 : VBA/Kryptik.T
F-Secure : Trojan:W97M/Nastjencro.A
Fortinet : WM/Agent.5110!tr
Kaspersky : HEUR:Trojan.Script.Agent.gen
McAfee : W97M/Dropper.cu
McAfee-GW-Edition : W97M/Dropper.cu
NANO-Antivirus : Trojan.Ole2.Vbs-heuristic.druvzi
Panda : O97M/Downloader 20161117
Qihoo-360 : virus.office.gen.75
Symantec : W97M.Downloader
TrendMicro : W2KM_HANCITOR.YYSXC
TrendMicro-HouseCall : W2KM_HANCITOR.YYSXC
inv11172016.doc is a virus.
Email analysis :
NOTE : Return-Path : < rm@restaurantcocotte.com >
NOTE : 162.252.121.130 ()
NOTE : Mime-Version : 1.0
NOTE : Content-Transfer-Encoding : 7bit
NOTE : X-Mailer : iPad Mail (11D169)
NOTE : Message-Id : < *@restaurantcocotte.com >
NOTE : Content-Type : text/html; charset="utf-8"
NOTE : Received : from unknown (HELO restaurantcocotte.com) (162.252.121.130)
NOTE : RE: shipping done
Here s the tracking invoice :
https://www.ups.com/?tracking_invoice=219371293129312& action=download
Let us know when it arrives.
Thanks
Phishing analysis :
CLICK : https://www.ups.com/?tracking_invoice=219371293129312& action=download
OPEN : http://invoice-portal.com/invoices/get.php?id=d2VibWFzdGVyQHJiY2FmZS5jb20=
RESULT : Download a file called : inv11172016.doc
File analysis :
ESET-NOD32 : VBA/Kryptik.T
F-Secure : Trojan:W97M/Nastjencro.A
Fortinet : WM/Agent.5110!tr
Kaspersky : HEUR:Trojan.Script.Agent.gen
McAfee : W97M/Dropper.cu
McAfee-GW-Edition : W97M/Dropper.cu
NANO-Antivirus : Trojan.Ole2.Vbs-heuristic.druvzi
Panda : O97M/Downloader 20161117
Qihoo-360 : virus.office.gen.75
Symantec : W97M.Downloader
TrendMicro : W2KM_HANCITOR.YYSXC
TrendMicro-HouseCall : W2KM_HANCITOR.YYSXC
inv11172016.doc is a virus.
Email analysis :
NOTE : Return-Path : < rm@restaurantcocotte.com >
NOTE : 162.252.121.130 ()
NOTE : Mime-Version : 1.0
NOTE : Content-Transfer-Encoding : 7bit
NOTE : X-Mailer : iPad Mail (11D169)
NOTE : Message-Id : < *@restaurantcocotte.com >
NOTE : Content-Type : text/html; charset="utf-8"
NOTE : Received : from unknown (HELO restaurantcocotte.com) (162.252.121.130)
NOTE : RE: shipping done
Wednesday, November 16, 2016
< no subject >
2016111105002973550858.zip
File analysis :
Download : 2016111105002973550858.zip
Result : 2016111105002973550858.zip is a virus.
Virus analysis :
ALYac Trojan.JS.Downloader.GYQ
AVG JS/Downloader.Agent.62_I
AVware Trojan-Downloader.JS.Nemucod.bbp (v)
Ad-Aware Trojan.JS.Downloader.GYQ
AegisLab Troj.Downloader.Js.Cryptoload!c
AhnLab-V3 JS/Obfus
Antiy-AVL Trojan/Generic.ASVCS3S.3F7
Arcabit Trojan.JS.Downloader.GYQ
Avast JS:Downloader-DSB [Trj]
Avira (no cloud) HEUR/Suspar.Gen
Baidu JS.Trojan-Downloader.Nemucod.od
BitDefender Trojan.JS.Downloader.GYQ
CAT-QuickHeal JS.Locky.JE
Cyren JS/Nemucod.CA2
DrWeb JS.DownLoader.1225
ESET-NOD32 JS/TrojanDownloader.Nemucod.BMK
Emsisoft Trojan.JS.Downloader.GYQ (B)
F-Prot JS/Nemucod.CA2
F-Secure Trojan.JS.Downloader.GYQ
Fortinet JS/Nemucod.BDA!tr
GData Trojan.JS.Downloader.GYQ
Ikarus Trojan-Downloader.JS.Nemucod
K7AntiVirus Trojan ( 004dfe6d1 )
K7GW Trojan ( 004dfe6d1 )
Kaspersky Trojan-Downloader.JS.Agent.nbi
McAfee JS/Nemucod.jg
McAfee-GW-Edition JS/Nemucod.jg
eScan Trojan.JS.Downloader.GYQ
Microsoft TrojanDownloader:JS/Nemucod!rfn
NANO-Antivirus Trojan.Script.Heuristic-js.iacgm
Rising Downloader.Cryptoload!8.7DA (topis)
Sophos Mal/DrodZp-A
Symantec Trojan.Gen.NPE
Tencent Js.Trojan.Raas.Auto
TrendMicro JS_NEMUCOD.SMK14
VIPRE Trojan-Downloader.JS.Nemucod.bbp (v)
Final result :
I opened the virus, and the raw version of this virus is here : http://pastebin.com/raw/FVM8wh4v
This virus sounds like a ransomware...
Email analysis :
NOTE : diann.laughton99@winterbrew.com
NOTE : User-Agent : Microsoft-MacOutlook/14.0.0.100825
NOTE : Received : from customer-SLRC-130-213.megared.net.mx
NOTE : (unknown [201.164.130.213])
Thursday, September 22, 2016
documents (Virus)
Ramona huger Office Manager
Box Rentals LLC
Sanibel Executive Suites
Crestwood Apts.
Cleveland Apts.
rayatboxrentals@cableone.net
www.sanibelsuites.com
2230 East 8th St / Office
Joplin, Mo.64801
Cell-417-312-3661
Office-417-624-7900
Fax- 417-624-7971
5496921_55724.zip
Email analysis :
NOTE :
NOTE : Return-Path : < ramona.huger@cableone.net >
NOTE : Mime-Version : 1.0
NOTE : Message-Id : < *.*.*.JavaMail.zimbra@cableone.net >
NOTE : X-Mailer : Zimbra 8.0.7_GA_6021 (ZimbraWebClient - GC46 (Win)/8.0.7_GA_6021)
NOTE : Thread-Topic : documents
NOTE : Received : from PHC-i5-VAIO (unknown [113.186.230.214])
NOTE : [SPAM] documents
File analysis :
Download : 5496921_55724.zip.
Result : 5496921_55724.zip is a virus.
Virus analysis :
SHA256 16bb72cc0a9a02626ef293df46696f489935e5890df483251976d38d1bf613d9
ALYac JS:Trojan.Crypt.PV
AVG JS/Downloader.Agent.54_Q
Ad-Aware JS:Trojan.Crypt.PV
AhnLab-V3 JS/Obfus.S137
Antiy-AVL Trojan/Generic.ASMalwRG.70
Arcabit JS:Trojan.Crypt.PV
Avira (no cloud) HEUR/Suspar.Gen
Baidu JS.Trojan-Downloader.Nemucod.jn
BitDefender JS:Trojan.Crypt.PV
CAT-QuickHeal JS.Locky.FA
Cyren JS/Nemucod.CA1
DrWeb JS.DownLoader.2236
ESET-NOD32 JS/TrojanDownloader.Nemucod.AZC
Emsisoft JS:Trojan.Crypt.PV (B)
F-Prot JS/Nemucod.CA1
F-Secure JS:Trojan.Crypt.PV
Fortinet JS/Nemucod.SMK9!tr
GData JS:Trojan.Crypt.PV
Ikarus Trojan-Ransom.Script.Locky
K7AntiVirus Trojan ( 004f43681 )
K7GW Trojan ( 004f43681 )
Kaspersky Trojan-Downloader.JS.Cryptoload.als
McAfee JS/Nemucod.jg
McAfee-GW-Edition JS/Nemucod.jg
eScan JS:Trojan.Crypt.PV
Microsoft TrojanDownloader:JS/Swabfex.P
Sophos Mal/DrodZp-A
Tencent Js.Trojan.Raas.Auto
Open Virus :
NOTE : CYTUKE64504.wsf
NOTE : Windows Script File (WSF)
NOTE : http://pastebin.com/BqrxRQqW
RAW : http://pastebin.com/raw/BqrxRQqW
Box Rentals LLC
Sanibel Executive Suites
Crestwood Apts.
Cleveland Apts.
rayatboxrentals@cableone.net
www.sanibelsuites.com
2230 East 8th St / Office
Joplin, Mo.64801
Cell-417-312-3661
Office-417-624-7900
Fax- 417-624-7971
5496921_55724.zip
Email analysis :
NOTE :
NOTE : Return-Path : < ramona.huger@cableone.net >
NOTE : Mime-Version : 1.0
NOTE : Message-Id : < *.*.*.JavaMail.zimbra@cableone.net >
NOTE : X-Mailer : Zimbra 8.0.7_GA_6021 (ZimbraWebClient - GC46 (Win)/8.0.7_GA_6021)
NOTE : Thread-Topic : documents
NOTE : Received : from PHC-i5-VAIO (unknown [113.186.230.214])
NOTE : [SPAM] documents
File analysis :
Download : 5496921_55724.zip.
Result : 5496921_55724.zip is a virus.
Virus analysis :
SHA256 16bb72cc0a9a02626ef293df46696f489935e5890df483251976d38d1bf613d9
ALYac JS:Trojan.Crypt.PV
AVG JS/Downloader.Agent.54_Q
Ad-Aware JS:Trojan.Crypt.PV
AhnLab-V3 JS/Obfus.S137
Antiy-AVL Trojan/Generic.ASMalwRG.70
Arcabit JS:Trojan.Crypt.PV
Avira (no cloud) HEUR/Suspar.Gen
Baidu JS.Trojan-Downloader.Nemucod.jn
BitDefender JS:Trojan.Crypt.PV
CAT-QuickHeal JS.Locky.FA
Cyren JS/Nemucod.CA1
DrWeb JS.DownLoader.2236
ESET-NOD32 JS/TrojanDownloader.Nemucod.AZC
Emsisoft JS:Trojan.Crypt.PV (B)
F-Prot JS/Nemucod.CA1
F-Secure JS:Trojan.Crypt.PV
Fortinet JS/Nemucod.SMK9!tr
GData JS:Trojan.Crypt.PV
Ikarus Trojan-Ransom.Script.Locky
K7AntiVirus Trojan ( 004f43681 )
K7GW Trojan ( 004f43681 )
Kaspersky Trojan-Downloader.JS.Cryptoload.als
McAfee JS/Nemucod.jg
McAfee-GW-Edition JS/Nemucod.jg
eScan JS:Trojan.Crypt.PV
Microsoft TrojanDownloader:JS/Swabfex.P
Sophos Mal/DrodZp-A
Tencent Js.Trojan.Raas.Auto
Open Virus :
NOTE : CYTUKE64504.wsf
NOTE : Windows Script File (WSF)
NOTE : http://pastebin.com/BqrxRQqW
RAW : http://pastebin.com/raw/BqrxRQqW
Wednesday, August 17, 2016
Infração de Transito 10-08-2016 (Virus)
A partir do dia 10/08/2016, a Via Fácil realmente iniciou a aplicação de multas.
Todo motorista que passar a mais de 40 km/h receberá uma multa por excesso
de velocidade. Segundo a STP (empresa administradora), a multa do Sem Parar
é gerada pela Policia Rodoviária.
você foi multado veja abaixo copia da multa.
Download da multa aqui...
Email analysis :
NOTE : detran@drz.com.br
NOTE : Received : from unknown (HELO pc-PC)
NOTE : (menoli@drz.com.br@200.204.161.106)
NOTE : by beta.sercomtel.com.br
Link analysis :
CLICK : Download da multa aqui...
OPEN : https://tinyurl.com/j3nav3q?=visualizar/multa/10/08/2016
DOWNLOAD FILE FROM : https://dc431.4shared.com
RESULT : File is a virus.
Virus analysis :
FILENAME : Infração-de-transito-15-08-2016.rar
SHA256 : b3baf1dedb71e91ca1006d412b8ee7eb59bf6a0388bb89abd3aefc3ee0c14dd6
Ad-Aware : Gen:Variant.Symmi.60015
Arcabit : Trojan.Symmi.DEA6F
Avast : Win32:Malware-gen
Avira (no cloud) : TR/Downloader.sdtq
BitDefender : Gen:Variant.Symmi.60015
ESET-NOD32 : Win32/TrojanDownloader.Banload.XMW
Emsisoft : Gen:Variant.Symmi.60015 (B)
F-Secure : Gen:Variant.Symmi.60015
GData : Gen:Variant.Symmi.60015
Ikarus : Trojan-Downloader.Win32.Banload
K7GW : Trojan-Downloader ( 004f64451 )
Kaspersky : Trojan-Downloader.Win32.Delf.kkdi
McAfee : Artemis!383F16692822
eScan : Gen:Variant.Symmi.60015
TrendMicro : HEUR_NAMETRICK.A
TrendMicro-HouseCall : TROJ_GE.4D16FF7F
Conclusion :
Virus hosted by 4shared.com
Link to the virus hosted by tinyurl.com
Todo motorista que passar a mais de 40 km/h receberá uma multa por excesso
de velocidade. Segundo a STP (empresa administradora), a multa do Sem Parar
é gerada pela Policia Rodoviária.
você foi multado veja abaixo copia da multa.
Download da multa aqui...
Email analysis :
NOTE : detran@drz.com.br
NOTE : Received : from unknown (HELO pc-PC)
NOTE : (menoli@drz.com.br@200.204.161.106)
NOTE : by beta.sercomtel.com.br
Link analysis :
CLICK : Download da multa aqui...
OPEN : https://tinyurl.com/j3nav3q?=visualizar/multa/10/08/2016
DOWNLOAD FILE FROM : https://dc431.4shared.com
RESULT : File is a virus.
Virus analysis :
FILENAME : Infração-de-transito-15-08-2016.rar
SHA256 : b3baf1dedb71e91ca1006d412b8ee7eb59bf6a0388bb89abd3aefc3ee0c14dd6
Ad-Aware : Gen:Variant.Symmi.60015
Arcabit : Trojan.Symmi.DEA6F
Avast : Win32:Malware-gen
Avira (no cloud) : TR/Downloader.sdtq
BitDefender : Gen:Variant.Symmi.60015
ESET-NOD32 : Win32/TrojanDownloader.Banload.XMW
Emsisoft : Gen:Variant.Symmi.60015 (B)
F-Secure : Gen:Variant.Symmi.60015
GData : Gen:Variant.Symmi.60015
Ikarus : Trojan-Downloader.Win32.Banload
K7GW : Trojan-Downloader ( 004f64451 )
Kaspersky : Trojan-Downloader.Win32.Delf.kkdi
McAfee : Artemis!383F16692822
eScan : Gen:Variant.Symmi.60015
TrendMicro : HEUR_NAMETRICK.A
TrendMicro-HouseCall : TROJ_GE.4D16FF7F
Conclusion :
Virus hosted by 4shared.com
Link to the virus hosted by tinyurl.com
Saturday, July 23, 2016
Your SSL Certificate has expired
Dear customer,
You are receiving this notification because your Salesforce SSL certificate has expired.
In order to continue using Salesforce.com, you are required to update your digital certificate.
The new Salesforce digital certificate can be downloaded from:
https://salesforce.dattodrive.com/index.php/s/ZoeW7Vs1kfLcUdF/download
Instruction:
Unzip the downloaded file first. SSL certificate cannot be installed if it is zipped.
Double click the SSL certificate file and click 'OK' to confirm installation.
According to our Terms and Conditions, failing to renew the SSL certificate will result in account suspension or cancellation:
http://www.salesforce.com/company/privacy/security.jsp
Thank you for using Salesforce.com
Email screenshot :
Email analysis :
NOTE : support@salesforce.com
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; rv:24.0) Gecko/20100101 Thunderbird/24.2.0
NOTE : Return-Path : < americanexpress@welcome.aexp.com >
NOTE : Mime-Version : 1.0
NOTE : Content-Transfer-Encoding : 7bit
NOTE : Content-Type : text/plain; charset=ISO-8859-1; format=flowed
NOTE : paultayoy@alpestour.com
NOTE : Received : from 62.42.178.94.dyn.user.ono.com
NOTE : (62.42.178.94.dyn.user.ono.com [62.42.178.94])
NOTE : Your SSL Certificate has expired
Analysis of the link :
CLICK : https://salesforce.dattodrive.com/index.php/s/ZoeW7Vs1kfLcUdF/download
OPEN : https://salesforce.dattodrive.com/index.php/s/ZoeW7Vs1kfLcUdF/download
SCREENSHOT :
You are receiving this notification because your Salesforce SSL certificate has expired.
In order to continue using Salesforce.com, you are required to update your digital certificate.
The new Salesforce digital certificate can be downloaded from:
https://salesforce.dattodrive.com/index.php/s/ZoeW7Vs1kfLcUdF/download
Instruction:
Unzip the downloaded file first. SSL certificate cannot be installed if it is zipped.
Double click the SSL certificate file and click 'OK' to confirm installation.
According to our Terms and Conditions, failing to renew the SSL certificate will result in account suspension or cancellation:
http://www.salesforce.com/company/privacy/security.jsp
Thank you for using Salesforce.com
Email screenshot :
Email analysis :
NOTE : support@salesforce.com
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; rv:24.0) Gecko/20100101 Thunderbird/24.2.0
NOTE : Return-Path : < americanexpress@welcome.aexp.com >
NOTE : Mime-Version : 1.0
NOTE : Content-Transfer-Encoding : 7bit
NOTE : Content-Type : text/plain; charset=ISO-8859-1; format=flowed
NOTE : paultayoy@alpestour.com
NOTE : Received : from 62.42.178.94.dyn.user.ono.com
NOTE : (62.42.178.94.dyn.user.ono.com [62.42.178.94])
NOTE : Your SSL Certificate has expired
Analysis of the link :
CLICK : https://salesforce.dattodrive.com/index.php/s/ZoeW7Vs1kfLcUdF/download
OPEN : https://salesforce.dattodrive.com/index.php/s/ZoeW7Vs1kfLcUdF/download
SCREENSHOT :
Sunday, July 3, 2016
Tyler Butler sent you "Scanned Documents.zip"
Tyler Butler a file with you on Dropbox
The updated agreement with BDO
Scanned Documents.zip
Download
© 2016 Dropbox
Screenshot of the email :
Email analysis :
NOTE : no-reply@dropbox.com
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; rv:24.0)
NOTE : Gecko/20100101 Thunderbird/24.2.0
NOTE : americanexpress@welcome.aexp.com
NOTE : 14.174.35.53
NOTE : Received : from static.vnpt.vn (unknown [14.174.35.53])
File analysis :
CLICK : Download
OPEN :
https://www.cubbyusercontent.com/pl/Scanned+Documents.zip/_08fa4c28262f424b970037c786caf840
DOWNLOAD : Scanned Documents.zip
RESULT : Scanned Documents.zip is a virus.
Virus analysis :
FILENAME : Scanned Documents.zip
SHA256 : 27d79850e1bae0d14a689e1d019ef6217d805189b04e486e3d54ed8a363d3689
====================================
Ad-Aware : Trojan.GenericKD.3363605
AegisLab : Troj.Generickd!c
Arcabit : Trojan.Generic.D335315
Avira (no cloud) : HEUR/Suspar.Gen
BitDefender : Trojan.GenericKD.3363605
DrWeb : JS.DownLoader.1225
ESET-NOD32 : JS/TrojanDownloader.Nemucod.AGS
Emsisoft : Trojan.GenericKD.3363605 (B)
F-Secure : Trojan.GenericKD.3363605
Fortinet : JS/Nemucod.1509!tr
GData : Trojan.GenericKD.3363605
Ikarus : Trojan.Script
K7AntiVirus : Trojan ( 004dfe6d1 )
K7GW : Trojan ( 004dfe6d1 )
Kaspersky : HEUR:Trojan-Downloader.Script.Generic
McAfee : JS/Nemucod.la
McAfee-GW-Edition : JS/Nemucod.la
eScan : Trojan.GenericKD.3363605
Microsoft : TrojanDownloader:JS/Nemucod.EW
Sophos : Troj/JSDldr-PH
====================================
Extraction of the zip : 3 files extracted.
Result : Scan001.js, Scan002.js, Scan003.js
File Scan001.js
File Scan002.js
File Scan003.js
The updated agreement with BDO
Scanned Documents.zip
Download
© 2016 Dropbox
Screenshot of the email :
Email analysis :
NOTE : no-reply@dropbox.com
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; rv:24.0)
NOTE : Gecko/20100101 Thunderbird/24.2.0
NOTE : americanexpress@welcome.aexp.com
NOTE : 14.174.35.53
NOTE : Received : from static.vnpt.vn (unknown [14.174.35.53])
File analysis :
CLICK : Download
OPEN :
https://www.cubbyusercontent.com/pl/Scanned+Documents.zip/_08fa4c28262f424b970037c786caf840
DOWNLOAD : Scanned Documents.zip
RESULT : Scanned Documents.zip is a virus.
Virus analysis :
FILENAME : Scanned Documents.zip
SHA256 : 27d79850e1bae0d14a689e1d019ef6217d805189b04e486e3d54ed8a363d3689
====================================
Ad-Aware : Trojan.GenericKD.3363605
AegisLab : Troj.Generickd!c
Arcabit : Trojan.Generic.D335315
Avira (no cloud) : HEUR/Suspar.Gen
BitDefender : Trojan.GenericKD.3363605
DrWeb : JS.DownLoader.1225
ESET-NOD32 : JS/TrojanDownloader.Nemucod.AGS
Emsisoft : Trojan.GenericKD.3363605 (B)
F-Secure : Trojan.GenericKD.3363605
Fortinet : JS/Nemucod.1509!tr
GData : Trojan.GenericKD.3363605
Ikarus : Trojan.Script
K7AntiVirus : Trojan ( 004dfe6d1 )
K7GW : Trojan ( 004dfe6d1 )
Kaspersky : HEUR:Trojan-Downloader.Script.Generic
McAfee : JS/Nemucod.la
McAfee-GW-Edition : JS/Nemucod.la
eScan : Trojan.GenericKD.3363605
Microsoft : TrojanDownloader:JS/Nemucod.EW
Sophos : Troj/JSDldr-PH
====================================
Extraction of the zip : 3 files extracted.
Result : Scan001.js, Scan002.js, Scan003.js
File Scan001.js
File Scan002.js
File Scan003.js
Monday, May 9, 2016
DOCUMENT DE NON CONFORMITE (Virus)
Ci-joint le document de non conformité.
Bien � toi,
--
�
SCopieur VA9812357665355478.gz
Virus analysis :
SHA256 : 0235a1aded1737d8c89186b29a34610be835ff45f896091d6dcd6eb9a3152061
Filename : SCopieur VA9812357665355478.gz
ALYac : JS:Trojan.JS.Downloader.IQ
AVG : JS/Downloader.Agent
Ad-Aware : JS:Trojan.JS.Downloader.IQ
Arcabit : JS:Trojan.JS.Downloader.IQ
Avast : JS:Downloader-CZW [Trj]
Avira (no cloud) : JS/Dldr.Locky.98765
BitDefender : JS:Trojan.JS.Downloader.IQ
CAT-QuickHeal : JS.Locky.P
Cyren : JS/Locky.AC
DrWeb : JS.DownLoader.1397
ESET-NOD32 : JS/TrojanDownloader.Nemucod.WU
F-Prot : JS/Locky.AC
F-Secure : JS:Trojan.JS.Downloader.IQ
Fortinet : JS/Nemucod.WU!tr.dldr
GData : JS:Trojan.JS.Downloader.IQ
Ikarus : Trojan-Ransom.Script.Locky
Kaspersky : Trojan-Downloader.JS.Agent.kee
McAfee : JS/Nemucod.is
McAfee-GW-Edition : JS/Nemucod.is
eScan : JS:Trojan.JS.Downloader.IQ
Microsoft : TrojanDownloader:JS/Nemucod.EK
Rising : Downloader.Ransomware!8.625A-SOAAbihlG7H (Cloud)
Sophos : JS/Dldr-MD
Email analysis :
NOTE : lg46@valoritech.fr
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; WOW64; rv:38.0) Gecko/20100101 Thunderbird/38.7.0
NOTE : Received : from cmodem.201.140.226-163.wirenet.com.ar (unknown [201.140.226.163])
Bien � toi,
--
�
SCopieur VA9812357665355478.gz
Virus analysis :
SHA256 : 0235a1aded1737d8c89186b29a34610be835ff45f896091d6dcd6eb9a3152061
Filename : SCopieur VA9812357665355478.gz
ALYac : JS:Trojan.JS.Downloader.IQ
AVG : JS/Downloader.Agent
Ad-Aware : JS:Trojan.JS.Downloader.IQ
Arcabit : JS:Trojan.JS.Downloader.IQ
Avast : JS:Downloader-CZW [Trj]
Avira (no cloud) : JS/Dldr.Locky.98765
BitDefender : JS:Trojan.JS.Downloader.IQ
CAT-QuickHeal : JS.Locky.P
Cyren : JS/Locky.AC
DrWeb : JS.DownLoader.1397
ESET-NOD32 : JS/TrojanDownloader.Nemucod.WU
F-Prot : JS/Locky.AC
F-Secure : JS:Trojan.JS.Downloader.IQ
Fortinet : JS/Nemucod.WU!tr.dldr
GData : JS:Trojan.JS.Downloader.IQ
Ikarus : Trojan-Ransom.Script.Locky
Kaspersky : Trojan-Downloader.JS.Agent.kee
McAfee : JS/Nemucod.is
McAfee-GW-Edition : JS/Nemucod.is
eScan : JS:Trojan.JS.Downloader.IQ
Microsoft : TrojanDownloader:JS/Nemucod.EK
Rising : Downloader.Ransomware!8.625A-SOAAbihlG7H (Cloud)
Sophos : JS/Dldr-MD
Email analysis :
NOTE : lg46@valoritech.fr
NOTE : User-Agent : Mozilla/5.0 (Windows NT 6.1; WOW64; rv:38.0) Gecko/20100101 Thunderbird/38.7.0
NOTE : Received : from cmodem.201.140.226-163.wirenet.com.ar (unknown [201.140.226.163])
Tuesday, April 26, 2016
invoice confirmation (Virus)
Good day,
Please find attached invoice for the past months. Remit the new payment
by 30/05/2016 as outlines under our payment agreement.
Regards
Sino
FILE : invoice0879657_pdf.ace
invoice0879657_pdf.ace is a virus.
SHA256: fe382fb45d36b6e03728384999eb79b38f198168dc6fcc4ddbdabb69439a205a
DrWeb : Trojan.PWS.Stealer.1932
ESET-NOD32 : a variant of MSIL/Injector.OZV
Sophos : Mal/DrodAce-A
Email analysis :
NOTE : bik@isioco.fr
NOTE : User-Agent : Roundcube Webmail/1.1.4
NOTE : Received : from us32L.aryadns.com (us132.aryadns.com. [64.31.31.132])
NOTE : Received : from webmail.isioco.fr (localhost [IPv6:::1])
NOTE : by us32L.aryadns.com (Postfix)
NOTE : client-ip=64.31.31.132;
Please find attached invoice for the past months. Remit the new payment
by 30/05/2016 as outlines under our payment agreement.
Regards
Sino
FILE : invoice0879657_pdf.ace
invoice0879657_pdf.ace is a virus.
SHA256: fe382fb45d36b6e03728384999eb79b38f198168dc6fcc4ddbdabb69439a205a
DrWeb : Trojan.PWS.Stealer.1932
ESET-NOD32 : a variant of MSIL/Injector.OZV
Sophos : Mal/DrodAce-A
Email analysis :
NOTE : bik@isioco.fr
NOTE : User-Agent : Roundcube Webmail/1.1.4
NOTE : Received : from us32L.aryadns.com (us132.aryadns.com. [64.31.31.132])
NOTE : Received : from webmail.isioco.fr (localhost [IPv6:::1])
NOTE : by us32L.aryadns.com (Postfix)
NOTE : client-ip=64.31.31.132;
Thursday, January 14, 2016
URGENT RFQ (MORE VIRUS)
Dear Sir,
We sent you an order inquiry last week, but we did not receive any response from your regarding our order.
ATTACHED is a copy of NEW ORDER LIST for December Shipment. Please let me know the availability and your best prices of MATERIALS MARKED IN BLUE.
We will be waiting for your quotation.
Best Regards,
Roy
Al Nasser LLC
Virus analysis :
RFQ NO (14203) JAN DELIVERY ETA ETD PMM 01062016 jpeg1..ace
SHA256 : dacb8ff543c462f954500431f2a795a24ed10fa454cd7f27e3f0f1787dbe58fa
AVG : MSIL9.BEMV
Ad-Aware : Gen:Variant.Zusy.175290
Arcabit : Trojan.Zusy.D2ACBA
Avast : MSIL:Injector-NE [Trj]
BitDefender : Gen:Variant.Zusy.175290
Cyren : W32/Trojan.ZNMT-3910
DrWeb : Trojan.PWS.Siggen1.45471
ESET-NOD32 : a variant of MSIL/Injector.NLR
Emsisoft : Gen:Variant.Zusy.175290 (B)
F-Prot : W32/Trojan3.TDU
F-Secure : Gen:Variant.Zusy.175290
Fortinet : PossibleThreat.P0
GData : Gen:Variant.Zusy.175290
Ikarus : Evilware.Outbreak
Kaspersky : Trojan-PSW.Win32.Tepfer.psxdsw
MicroWorld-eScan : Gen:Variant.Zusy.175290
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Sophos : Mal/DrodAce-A
RFQ#Requirments Quote list ETD 05012015 RFxNumber 6200133094 jpeg2..ace
SHA256 : b7dd4530f2b97c33d1ea6df114d8fd7a9a6c6b1b78288394fbcf175b182e4da0
AVG : MSIL9.BEMV
Ad-Aware : Gen:Variant.Zusy.175290
Arcabit : Trojan.Zusy.D2ACBA
Avast : MSIL:Injector-NE [Trj]
Avira : TR/Dropper.MSIL.242773
BitDefender : Gen:Variant.Zusy.175290
Cyren : W32/Trojan.PNIW-7381
DrWeb : Trojan.PWS.Siggen1.45471
ESET-NOD32 : a variant of MSIL/Injector.NLR
Emsisoft : Gen:Variant.Zusy.175290 (B)
F-Secure : Gen:Variant.Zusy.175290
Fortinet : PossibleThreat.P0
GData : Gen:Variant.Zusy.175290
Ikarus : Evilware.Outbreak
Kaspersky : Trojan-PSW.Win32.Tepfer.psxdsx
MicroWorld-eScan : Gen:Variant.Zusy.175290
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Sophos : Mal/DrodAce-A
Email analysis :
NOTE : brainkings24@gmail.com
NOTE : ecos@atr.ecos.kz
NOTE : Received : from [142.54.171.74] (helo=User)
NOTE : by ecos.kz
We sent you an order inquiry last week, but we did not receive any response from your regarding our order.
ATTACHED is a copy of NEW ORDER LIST for December Shipment. Please let me know the availability and your best prices of MATERIALS MARKED IN BLUE.
We will be waiting for your quotation.
Best Regards,
Roy
Al Nasser LLC
Virus analysis :
RFQ NO (14203) JAN DELIVERY ETA ETD PMM 01062016 jpeg1..ace
SHA256 : dacb8ff543c462f954500431f2a795a24ed10fa454cd7f27e3f0f1787dbe58fa
AVG : MSIL9.BEMV
Ad-Aware : Gen:Variant.Zusy.175290
Arcabit : Trojan.Zusy.D2ACBA
Avast : MSIL:Injector-NE [Trj]
BitDefender : Gen:Variant.Zusy.175290
Cyren : W32/Trojan.ZNMT-3910
DrWeb : Trojan.PWS.Siggen1.45471
ESET-NOD32 : a variant of MSIL/Injector.NLR
Emsisoft : Gen:Variant.Zusy.175290 (B)
F-Prot : W32/Trojan3.TDU
F-Secure : Gen:Variant.Zusy.175290
Fortinet : PossibleThreat.P0
GData : Gen:Variant.Zusy.175290
Ikarus : Evilware.Outbreak
Kaspersky : Trojan-PSW.Win32.Tepfer.psxdsw
MicroWorld-eScan : Gen:Variant.Zusy.175290
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Sophos : Mal/DrodAce-A
RFQ#Requirments Quote list ETD 05012015 RFxNumber 6200133094 jpeg2..ace
SHA256 : b7dd4530f2b97c33d1ea6df114d8fd7a9a6c6b1b78288394fbcf175b182e4da0
AVG : MSIL9.BEMV
Ad-Aware : Gen:Variant.Zusy.175290
Arcabit : Trojan.Zusy.D2ACBA
Avast : MSIL:Injector-NE [Trj]
Avira : TR/Dropper.MSIL.242773
BitDefender : Gen:Variant.Zusy.175290
Cyren : W32/Trojan.PNIW-7381
DrWeb : Trojan.PWS.Siggen1.45471
ESET-NOD32 : a variant of MSIL/Injector.NLR
Emsisoft : Gen:Variant.Zusy.175290 (B)
F-Secure : Gen:Variant.Zusy.175290
Fortinet : PossibleThreat.P0
GData : Gen:Variant.Zusy.175290
Ikarus : Evilware.Outbreak
Kaspersky : Trojan-PSW.Win32.Tepfer.psxdsx
MicroWorld-eScan : Gen:Variant.Zusy.175290
Microsoft : Trojan:Win32/Dynamer!ac
Panda : Trj/CI.A
Sophos : Mal/DrodAce-A
Email analysis :
NOTE : brainkings24@gmail.com
NOTE : ecos@atr.ecos.kz
NOTE : Received : from [142.54.171.74] (helo=User)
NOTE : by ecos.kz
Urgent RQF
Dear Sir,
We sent you an order inquiry last week, but we did not receive any response from your regarding our order.
ATTACHED is a copy of NEW ORDER LIST for December Shipment. Please let me know the availability and your best prices of MATERIALS MARKED IN BLUE.
We will be waiting for your quotation.
Best Regards,
Roy
Al Nasser LLC
Proforma Invoice
RFQ#Requirments Quote list ETA ETD 05012015 RFxNumber 6200133094 jpeg.ace
Virus analysis :
DrWeb : Trojan.PWS.Stealer.15120
ESET-NOD32 : a variant of MSIL/Injector.NLF
Qihoo-360 : HEUR/QVM03.0.Malware.Gen 20160105
Sophos : Mal/DrodAce-A 20160105
Email analysis :
NOTE : prabhukumar59@yahoo.com
NOTE : ecos@atr.ecos.kz
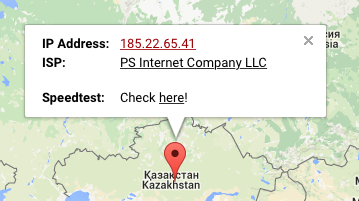
NOTE : 185.22.65.41 (mail.ecos.kz)
NOTE : Received : from [142.54.171.74] (helo=User) by ecos.kz
We sent you an order inquiry last week, but we did not receive any response from your regarding our order.
ATTACHED is a copy of NEW ORDER LIST for December Shipment. Please let me know the availability and your best prices of MATERIALS MARKED IN BLUE.
We will be waiting for your quotation.
Best Regards,
Roy
Al Nasser LLC
Proforma Invoice
RFQ#Requirments Quote list ETA ETD 05012015 RFxNumber 6200133094 jpeg.ace
Virus analysis :
DrWeb : Trojan.PWS.Stealer.15120
ESET-NOD32 : a variant of MSIL/Injector.NLF
Qihoo-360 : HEUR/QVM03.0.Malware.Gen 20160105
Sophos : Mal/DrodAce-A 20160105
Email analysis :
NOTE : prabhukumar59@yahoo.com
NOTE : ecos@atr.ecos.kz
NOTE : 185.22.65.41 (mail.ecos.kz)
NOTE : Received : from [142.54.171.74] (helo=User) by ecos.kz
Wednesday, December 2, 2015
Rép : New order (Virus)
GoodDay,
Find the attached specifications in the purchase order for our company end of the year sales before sending your Proforma Invoice and do get back to me with your quotations asap. An Official order placement will follow as soon as possible. But note that we have restructured the order so the first order will not exceed 20-40feet containers.
Thanks & Best Regards,
Manager Purchasing Department
Shirley Lee
TMS Titanium
HEADQUARTERS
12215 Kirkham Rd., Suite 300
Poway, CA 92064
EMAIL: sales@tmstitanium.com
SALES AND CUSTOMER SERVICE
Toll Free: (888) 748-8510
Local: (858) 748-8510
FAX
(858) 748-8526
scanned purchase order.ace
File analysis :
NOTE : Open scanned purchase order.ace
NOTE : scanned purchase order.ace is a virus.
Virus analysis :
Avast : Win32:Malware-gen
ESET-NOD32 : a variant of Win32/Injector.CNFH
GData : Archive.Trojan.Agent.14JCQ5
Ikarus : Trojan.Win32.Injector
Kaspersky : Trojan.Win32.Scarsi.aaab
Panda : Generic Suspicious
Qihoo-360 : HEUR/QVM03.0.Malware.Gen
Sophos : Mal/DrodAce-A
Email analysis :
NOTE : sales@tmstitanium.com
NOTE : SUNSHINESLISA1@YAHOO.COM
NOTE : Received : from [67.227.193.36]
NOTE : (UnknownHost [67.227.193.36]) by mail2.postbulletin.com
Find the attached specifications in the purchase order for our company end of the year sales before sending your Proforma Invoice and do get back to me with your quotations asap. An Official order placement will follow as soon as possible. But note that we have restructured the order so the first order will not exceed 20-40feet containers.
Thanks & Best Regards,
Manager Purchasing Department
Shirley Lee
TMS Titanium
HEADQUARTERS
12215 Kirkham Rd., Suite 300
Poway, CA 92064
EMAIL: sales@tmstitanium.com
SALES AND CUSTOMER SERVICE
Toll Free: (888) 748-8510
Local: (858) 748-8510
FAX
(858) 748-8526
scanned purchase order.ace
File analysis :
NOTE : Open scanned purchase order.ace
NOTE : scanned purchase order.ace is a virus.
Virus analysis :
Avast : Win32:Malware-gen
ESET-NOD32 : a variant of Win32/Injector.CNFH
GData : Archive.Trojan.Agent.14JCQ5
Ikarus : Trojan.Win32.Injector
Kaspersky : Trojan.Win32.Scarsi.aaab
Panda : Generic Suspicious
Qihoo-360 : HEUR/QVM03.0.Malware.Gen
Sophos : Mal/DrodAce-A
Email analysis :
NOTE : sales@tmstitanium.com
NOTE : SUNSHINESLISA1@YAHOO.COM
NOTE : Received : from [67.227.193.36]
NOTE : (UnknownHost [67.227.193.36]) by mail2.postbulletin.com
Tuesday, October 27, 2015
Openings? (Virus)
Hi there.
I saw your business today Sat, 24 Oct 2015 and found it very likeable.
I was praying there was any possibility of employment, just to prove my competence.
As you will see in my resume, I am very qualified and have a very sweeping experience in this field of work. I am confident it will be worth your time reviewing it, and I am even more positive you will find me very suitable in your corporation.
Please see my CV.
I'm very much looking forward to hearing from you.
Thanks,
Theda Deisch
My_Resume_64004.doc
My_Resume_64004.doc analysis :
My_Resume_64004.doc is a virus.
Virus analysis :
AVware LooksLike.Macro.Malware.h (v)
AhnLab-V3 : DOC/Downloader
Arcabit : HEUR.VBA.Trojan
CAT-QuickHeal : O97M.Dropper.LQ
Fortinet : WM/Agent!tr
Ikarus : Trojan-Downloader.VBA.Agent
Sophos : Troj/DocDl-AFA
Symantec : W97M.Downloader
TrendMicro : TROJ_FRS.0NA004JP15
TrendMicro-HouseCall : TROJ_FRS.0NA004JP15
VIPRE : LooksLike.Macro.Malware.h (v)
Email analysis :
NOTE : thedaobmhf@rambler.ru
NOTE : Mime-Version : 1.0
NOTE : 81.19.67.206
NOTE : X-Rambler-User : thedaobmhf@rambler.ru/117.253.216.19
NOTE : X-Mailer : Rambler WebMail, http://mail.rambler.ru/
NOTE : Received : from [117.253.216.19] by mail.rambler.ru
NOTE : Openings?
I saw your business today Sat, 24 Oct 2015 and found it very likeable.
I was praying there was any possibility of employment, just to prove my competence.
As you will see in my resume, I am very qualified and have a very sweeping experience in this field of work. I am confident it will be worth your time reviewing it, and I am even more positive you will find me very suitable in your corporation.
Please see my CV.
I'm very much looking forward to hearing from you.
Thanks,
Theda Deisch
My_Resume_64004.doc
My_Resume_64004.doc analysis :
My_Resume_64004.doc is a virus.
Virus analysis :
AVware LooksLike.Macro.Malware.h (v)
AhnLab-V3 : DOC/Downloader
Arcabit : HEUR.VBA.Trojan
CAT-QuickHeal : O97M.Dropper.LQ
Fortinet : WM/Agent!tr
Ikarus : Trojan-Downloader.VBA.Agent
Sophos : Troj/DocDl-AFA
Symantec : W97M.Downloader
TrendMicro : TROJ_FRS.0NA004JP15
TrendMicro-HouseCall : TROJ_FRS.0NA004JP15
VIPRE : LooksLike.Macro.Malware.h (v)
Email analysis :
NOTE : thedaobmhf@rambler.ru
NOTE : Mime-Version : 1.0
NOTE : 81.19.67.206
NOTE : X-Rambler-User : thedaobmhf@rambler.ru/117.253.216.19
NOTE : X-Mailer : Rambler WebMail, http://mail.rambler.ru/
NOTE : Received : from [117.253.216.19] by mail.rambler.ru
NOTE : Openings?
Your account expires in less than 48 hours .
Hello,
please, kindly quote your best prices for our attached order.Your company came higly recommeded for this order. For item No 1,4,6 & 7..give your best prices for we wish to make large order. Add me on Skype for detailed discussion
Awaiting your urgent confirmation
Thanks & Best Regards
NAZIR AHMED
PHONE: +92-222-633263, +92-222-617906,
FAX: +92-222-612877
Mobile : +92-300-3010717
EMAIL: info@almarryamint.com afintpk@yahoo.com
SKYPE: afintpk
subject...Order No. 1,4,6 & 7
ORDER.ace
File analysis :
ORDER.ace : virus.
ORDER.ace : Qihoo-360 : htm.faceliker.d.39
Email analysis :
NOTE : arabico2222@gmail.com
NOTE : Mime-Version : 1.0
NOTE : User-Agent : SquirrelMail/1.5.2 [SVN]
NOTE : Received : from march.alignhosting.com
NOTE : (march.alignhosting.com. [67.205.123.150])
NOTE : authenticated_id: info@stcotransport.com
please, kindly quote your best prices for our attached order.Your company came higly recommeded for this order. For item No 1,4,6 & 7..give your best prices for we wish to make large order. Add me on Skype for detailed discussion
Awaiting your urgent confirmation
Thanks & Best Regards
NAZIR AHMED
PHONE: +92-222-633263, +92-222-617906,
FAX: +92-222-612877
Mobile : +92-300-3010717
EMAIL: info@almarryamint.com afintpk@yahoo.com
SKYPE: afintpk
subject...Order No. 1,4,6 & 7
ORDER.ace
File analysis :
ORDER.ace : virus.
ORDER.ace : Qihoo-360 : htm.faceliker.d.39
Email analysis :
NOTE : arabico2222@gmail.com
NOTE : Mime-Version : 1.0
NOTE : User-Agent : SquirrelMail/1.5.2 [SVN]
NOTE : Received : from march.alignhosting.com
NOTE : (march.alignhosting.com. [67.205.123.150])
NOTE : authenticated_id: info@stcotransport.com
Tuesday, September 1, 2015
Payment for driving on toll road, invoice #00000485134 (Virus)
Notice to Appear,
You have not paid for driving on a toll road.
You are kindly asked to service your debt in the shortest time possible.
You can find the invoice is in the attachment.
Yours faithfully,
Warren Mccarthy,
E-ZPass Manager.
E-ZPass_Invoice_00000485134.zip
File analysis :
OPEN : E-ZPass_Invoice_00000485134.zip
RESULT : File is a virus.
Virus analysis :
ALYac : JS:Trojan.Crypt.NO
AVware : Malware.JS.Generic (JS)
Ad-Aware : JS:Trojan.Crypt.NO
Arcabit : JS:Trojan.Crypt.NO
Avira : HTML/ExpKit.Gen2
BitDefender : JS:Trojan.Crypt.NO
Comodo : Heur.Dual.Extensions
Cyren : JS/Nemucod.D.gen
DrWeb : SCRIPT.Virus
ESET-NOD32 : JS/TrojanDownloader.Nemucod.AV
Emsisoft : JS:Trojan.Crypt.NO (B)
F-Prot : JS/Nemucod.D.gen
F-Secure : JS:Trojan.Crypt.NO
Fortinet : JS/Nemucod.AJ!tr.dldr
GData : JS:Trojan.Crypt.NO
McAfee : JS/Nemucod.i
MicroWorld-eScan : JS:Trojan.Crypt.NO
Microsoft : TrojanDownloader:JS/Nemucod.P
NANO-Antivirus Trojan.Script.Agent.dtchtk
Rising : NORMAL:Trojan.DL.Script.JS.Nemucod.b!1616509[F1]
Sophos : Troj/JSDldr-AF
VIPRE : Malware.JS.Generic (JS)
nProtect : JS:Trojan.Crypt.NO
Email analysis :
NOTE : cadaloz@kadir.doyumsuzgeceler.com
NOTE : Mime-Version : 1.0
NOTE : X-Priority : 3
NOTE : X-Php-Script : cadaloz.net/post.php for 94.23.148.159
NOTE : Received : from kadir.doyumsuzgeceler.com
NOTE : (37.58.75.120-static.reverse.softlayer.com. [37.58.75.120])
You have not paid for driving on a toll road.
You are kindly asked to service your debt in the shortest time possible.
You can find the invoice is in the attachment.
Yours faithfully,
Warren Mccarthy,
E-ZPass Manager.
E-ZPass_Invoice_00000485134.zip
File analysis :
OPEN : E-ZPass_Invoice_00000485134.zip
RESULT : File is a virus.
Virus analysis :
ALYac : JS:Trojan.Crypt.NO
AVware : Malware.JS.Generic (JS)
Ad-Aware : JS:Trojan.Crypt.NO
Arcabit : JS:Trojan.Crypt.NO
Avira : HTML/ExpKit.Gen2
BitDefender : JS:Trojan.Crypt.NO
Comodo : Heur.Dual.Extensions
Cyren : JS/Nemucod.D.gen
DrWeb : SCRIPT.Virus
ESET-NOD32 : JS/TrojanDownloader.Nemucod.AV
Emsisoft : JS:Trojan.Crypt.NO (B)
F-Prot : JS/Nemucod.D.gen
F-Secure : JS:Trojan.Crypt.NO
Fortinet : JS/Nemucod.AJ!tr.dldr
GData : JS:Trojan.Crypt.NO
McAfee : JS/Nemucod.i
MicroWorld-eScan : JS:Trojan.Crypt.NO
Microsoft : TrojanDownloader:JS/Nemucod.P
NANO-Antivirus Trojan.Script.Agent.dtchtk
Rising : NORMAL:Trojan.DL.Script.JS.Nemucod.b!1616509[F1]
Sophos : Troj/JSDldr-AF
VIPRE : Malware.JS.Generic (JS)
nProtect : JS:Trojan.Crypt.NO
Email analysis :
NOTE : cadaloz@kadir.doyumsuzgeceler.com
NOTE : Mime-Version : 1.0
NOTE : X-Priority : 3
NOTE : X-Php-Script : cadaloz.net/post.php for 94.23.148.159
NOTE : Received : from kadir.doyumsuzgeceler.com
NOTE : (37.58.75.120-static.reverse.softlayer.com. [37.58.75.120])
Subscribe to:
Posts (Atom)